Companies have become more open in the past year to receiving vulnerability reports from security researchers, according to ethical hackers surveyed by bug bounty platform HackerOne.
According to HackerOne’s 2018 Hacker Report, which surveyed nearly 2,000 white hat hackers across 100 countries, companies are somewhat more open (38%) or far more open (34%) to receiving vulnerability reports. Only less than 10% of respondents said firms are less open.
On the other hand, nearly a quarter of respondents said they had not reported vulnerabilities due to the fact that the affected software’s developer had not provided a channel for responsible disclosure.
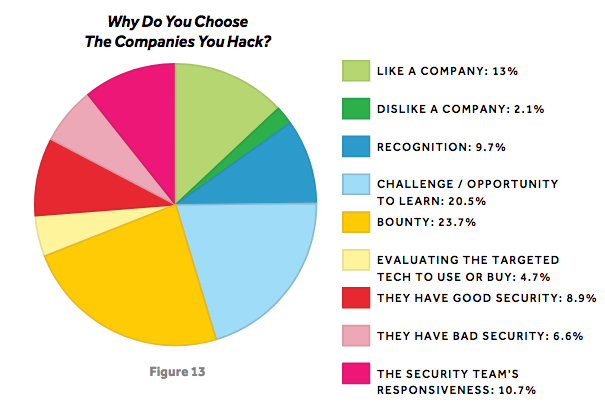
When it comes to motivation, money is not the most important – as it was in the previous year. There are more researchers hacking to learn new techniques (14.7%), for fun (14%), and for the challenge (14%) than ones who do it for the money (13.1%). Nearly one-quarter of respondents said they donated money earned from bug bounties to charities.
A majority of HackerOne users named websites as their favorite target (70%), followed by APIs (7.5%), Android apps (4.2%), operating systems (3.1%), and IoT systems (2.6%).
Burp Suite is the favorite tool of nearly one-third of hackers, but more than 15% claim they use their own tools to find vulnerabilities. Other popular tools include web proxies and scanners, network scanners, fuzzers, and debuggers.
A vast majority of the white hats who have signed up on the HackerOne platform, which hosts the bug bounty programs of more than 1,000 organizations, are under the age of 35, and many of them learned how to hack on their own. Most of them either work in IT (software or hardware), consulting, or they are students.
Roughly 66% spend less than 20 hours per week hacking, and only 13% spend 40 hours or more. More than 71% have less than 5 years experience, and only 10% have been hacking for more than 10 years.
Over $23 million have been paid out through HackerOne, with more than $4 million paid to researchers in the U.S., $3 million to India, and $1.3 million each to Australia and Russia. The largest chunk came from companies in the United States ($16 million) and Canada ($1.2 million).
In some places, bug bounty hunters earn far more than they would as a software engineer in their country. For example, in India and Argentina they earn roughly 16 times more than the median annual wage of a software engineer, while in Hong Kong and Egypt they earn 8 times more.
A quarter of respondents said bug bounties represent at least half of their annual income and 14% said they represent 90-100% of their income. Three percent reported making more than $100,000 per year from bug bounty programs, and 1% make more than $350,000.
Related: HackerOne Penetrates VC Pockets for $40 Million
Related: HackerOne Offers Free Service to Open Source Projects












