On Wednesday, NSS Labs released the results of a study that examined Next Generation Firewalls (NGFWs), and their ability to deal with SSL traffic. What they found was unfortunate, as many of the products – which are often the core of an enterprise’s defense strategy, failed to deal with the encrypted traffic properly.
The Fortinet 3600C, Sourcefire 8290, and Checkpoint 12600 firewalls were the poor performers during the NSS Labs test, but all of the vendors who took part had issues – especially when it came to SSL using 2048 bit ciphers. According to NSS Labs, the nature of SSL decryption itself is what causes performance problems; and as a result attackers are targeting this blind spot and using SSL as a transport method for malicious payloads.
 NSS Labs tested firewalls from Juniper (who performed the best of the bunch), Stonesoft, Palo Alto Networks, Sourcefire, Checkpoint, Dell SonicWALL, and Fortinet. On average, the seven devices experienced performance issues 74% of the time when faced with 512 bit and 1024 bit ciphers; and 81% of the time when faced with 2048 bit ciphers, which is a problem considering the SSL standard is expected to switch to 2048 by the end of the year.
NSS Labs tested firewalls from Juniper (who performed the best of the bunch), Stonesoft, Palo Alto Networks, Sourcefire, Checkpoint, Dell SonicWALL, and Fortinet. On average, the seven devices experienced performance issues 74% of the time when faced with 512 bit and 1024 bit ciphers; and 81% of the time when faced with 2048 bit ciphers, which is a problem considering the SSL standard is expected to switch to 2048 by the end of the year.
Further, the average number of transactions per-second suffered as well. The test results show that transactions seen a loss of 864% when tested against 512 bit ciphers; 87% against 1024 bit ciphers, and a loss of 92% against 2048 bit ciphers.
“I knew that onboard vs. offboard SSL/TLS decryption likely wouldn’t yield favorable results, but I was blown away with the increased performance loss created by moving from 1024 bit certificates to 2048 bit certificates,” said John Pirc, Research Vice President at NSS Labs.
Key findings by NSS Labs include:
• The average proportion of SSL traffic within a typical enterprise is 25% – 35%.
• NSS research indicates that the majority of threats that are using SSL as a transport fall under the targeted persistent attack (TPA) category.
• The mean average of performance loss across 7 NGFW’s: ~74% with 512b and 1024b ciphers ~81% with 2048b ciphers.
• The Sourcefire NGFW had the highest rated TPS performance, however, Sourcefire was the only vendor that used a dedicated SSL appliance.
• The Dell SonicWALL SuperMassive E10800 NGFW had the highest rated TPS performance with onboard SSL decryption.
• All vendors had significant performance issues and TPS loss with 2048b ciphers.
“Today, the percentage of malware using SSL/TLS is very small, however, as more decide to use SSL/TLS for both delivering malware and as a call back to a command and control server, we are going to be blind to the attacks. I think we still have time for vendors to improve their capabilities,” adds Pirc.
NSS also voiced concerns for the visability of SSL inspection in enterprise networks without the use of dedicated SSL decryption devices and suggests that enterprises measure the SSL traffic in their current network environment in order to allow for future capacity planning.
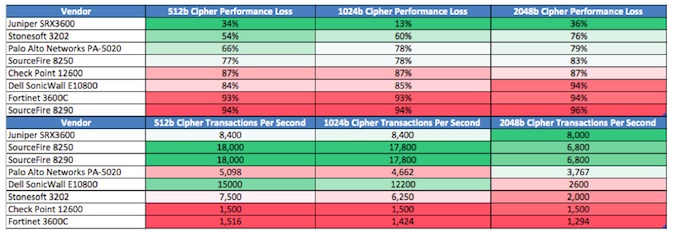
SSL Performance Impacts On Bandwidth And Transaction Per Second Loss (Source NSS Labs)
“Enterprises should seek to offset the SSL risk by deploying endpoint security solutions and breach detection solutions that are behavior-based, and that are able to detect command and control (C&C) and malware callbacks via SSL,” the report advised.
Additionally, NSS advises that organizations test platforms before buying, with consideration given to products that support the creation of rules for bypassing SSL decryption based on URL categories.
NSS also suggested that enterprises should educate users about the dangers of accepting a self-signed and non-valid certificate, similar to how they would educate employees about SPAM and phishing attacks.
The report can be seen here (PDF).
Related: Increasing SSL Traffic Challenging Enterprise Security Efforts
Additional reporting by Mike Lennon














