FireEye has released its 2013 Advanced Threat Report (ATR), which provides a high-level overview of attacks that the company discovered last year.
According to FireEye, malware activity has become so pervasive globally that attack servers communicating with malware are now hosted in 206 countries and territories.
In its report, released Feb. 27, FireEye said that it discovered eleven zero-day attacks in 2013. While in the first half of the year Java was the most common target for zero-days, the security firm witnessed a surge in Internet Explorer (IE) zero-day attacks used in watering hole attacks during the second half of the year.
“Unfortunately, Java has historically received less attention from security researchers, but the recent surge in publicized Java vulnerabilities may help to improve security for the platform in the future,” the report said. “What was once limited to a subset of APT actors has now become mainstream for many crimeware groups. Java exploit development has become that easy.”
Drawing on data gathered from nearly 40,000 unique cyber attacks (more than 100 per day) and over 22 million malware command and control (CnC) communications, the report provides a global look into cyber attacks that routinely bypass traditional defenses such as firewalls, next-generation firewalls, IPS, anti-virus, and security gateways.
Based on FireEye data from 2013, the top 10 countries targeted by APT actors are:
1. United States
2. South Korea
3. Canada
4. Japan
5. United Kingdom
6. Germany
7. Switzerland
8. Taiwan
9. Saudi Arabia
10. Israel
While the United States had nearly one quarter of the world’s initial CnC infrastructure in 2013, the largest international clusters of malicious servers were based in Europe and Asia, the report said.
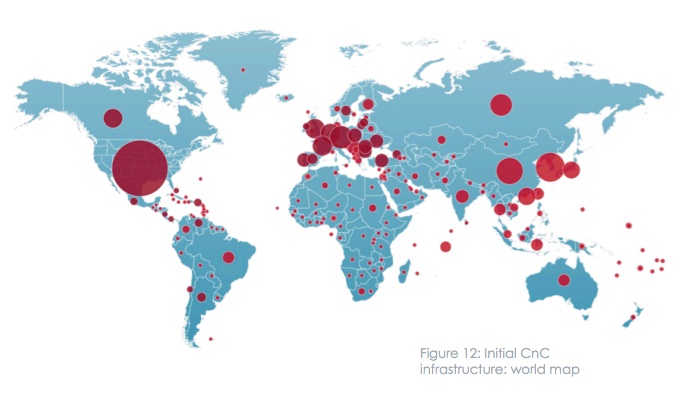
The top ten countries that were home to CnC infrastructure in 2013:
1. United States (24.1%)
2. Germany (5.6%)
3. South Korea (5.6%)
4. China (4.2%)
5. Netherlands (3.7%)
6. United Kingdom (3.5%)
7. Russia (3.2%)
8. Canada (2.9%)
9. France (2.7%)
10. Hong Kong (1.9%)
Other Key findings in the 22-page Advanced Threat Report include:
• In 2013, FireEye analyzed 767,318 unique CnC communications, or more than one per minute; and 22,509,176 total CnC communications, or more than one every 1.5 seconds on average.
• Enterprises are attacked on average once every 1.5 seconds.
• Malware attack servers, command and control (CnC) infrastructure have been placed in 206 countries and territories, up from 184 in 2012. The U.S., Germany, South Korea, China, Netherlands, United Kingdom, and Russia were home to the most CnC servers.
• FireEye identified five times more Web-based attacks than email-based attacks globally, and that per country, there were three times more Web attacks than email attacks.
“The increasing frequency at which cyber attacks are happening illustrates the allure of malware to those with malicious intentions,” said Dr. Kenneth Geers, senior global threat analyst at FireEye. “Across the board, we are seeing a global expansion of APTs, malware, CnC infrastructure, and the use of publically available tools to facilitate the attack process. The global scale of the threat has put cyber defenders in the very difficult position of not having any clue where the next attack will come from.”
“The 2013 ATR offers strong evidence that malware infections occur within enterprises at an alarming rate, that attacker infrastructure is global in scope, and that advanced attackers continue to penetrate legacy defenses, such as firewalls and anti-virus (AV), with ease,” Geers concluded.
A full copy of the Advanced Threat Report is available online (PDF).















