Malware has always been a global effort, and that hasn’t changed in recent years, as FireEye identified C&C servers in over 180 countries pushing out malware and communicating with infected machines.
 Cyber-criminals are transforming the command-and-control infrastructure to a more distributed model in order to make it harder for organizations to know where the threats are coming from, FireEye said in its Advanced Cyber Attack Landscape report released Tuesday. Once infected, the computers generally contact a command-and-control server to download additional malware or receive instructions on what it should do next. For the most part, these callbacks are to C&C servers located in the same country or region as the infected machine, FireEye found.
Cyber-criminals are transforming the command-and-control infrastructure to a more distributed model in order to make it harder for organizations to know where the threats are coming from, FireEye said in its Advanced Cyber Attack Landscape report released Tuesday. Once infected, the computers generally contact a command-and-control server to download additional malware or receive instructions on what it should do next. For the most part, these callbacks are to C&C servers located in the same country or region as the infected machine, FireEye found.
FireEye tracked more than 12 million malware communication callbacks across hundreds of thousands of infected enterprise hosts for the report. FireEye found C&C servers operating out of 184 countries in 2012, compared to “only” 130 countries back in 2010.
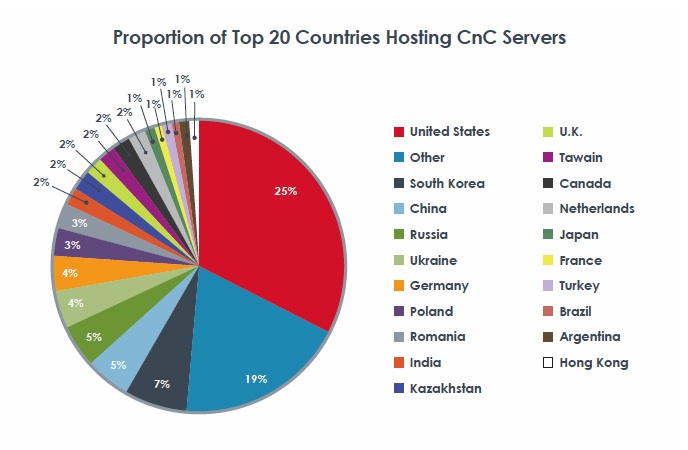
To underscore the idea that infected machines are communicating with local C&C servers, about 44 percent of C&C servers were located in the United States. Techniques for disguising callback communications are becoming more sophisticated, according to FireEye.
Cyber-criminals “easily evade detection and establish connections inside the perimeter of major organizations,” said FireEye CEO David DeWalt.
Network administrators frequently looked at network traffic and identified malicious traffic based on where it was originating from. If most of the customers are based out of the United States, chances were there was no legitimate reason for that organization to have systems communicating with Belarus, for example. However, FireEye’s report makes it clear that administrators can’t rely on geographic regions to find malicious traffic anymore.
Attackers are also increasingly hiding their activities by using social sites such as Facebook and Twitter to communicate with infected machines or embedding information inside JPG images, FireEye said. This way, malicious traffic seem benign to administrators.
“The threat landscape has evolved, as cyber threats have outpaced traditional signature-based security defenses, such as anti-virus,” DeWalt said.
While China is frequently accused of being the largest source of attacks, it is not the only offender. Parts of South and East Asia, as well as Eastern Europe are hotbeds for cyber-criminal activity, FireEye said. China, South Korea, Indi, Japan, and Hong Kong together account for 24 percent of cyber-attacks, while Russia, Romania, Poland, Ukraine, Kazakhstan, and Latvia accounted for another 22 percent.
Technology companies were the most targeted, followed by manufacturing, healthcare, energy and utilities, and financial services, FireEye said. Technology companies are most likely targeted because of the wealth of intellectual property residing on their networks. Other motivations include sabotage or modifying source code to further criminal activities.
Attacks are “impacting nearly every major bank, technology company, government agency and critical infrastructure provider,” FireEye said.
FireEye also looked at advanced persistent threat-style attacks, and found that the majority—or 89 percent—of APT callback activities were associated with tools made in China or by known Chinese hacking groups. The most commonly used tool was Gh0st RAT, FireEye said. About two-third of the C&C servers associated with APT activity were based in the United States.















