A recently disclosed crypto-related vulnerability affecting some Infineon chips can be exploited in a shorter amount of time than initially believed, researchers demonstrated.
A team of experts from the Czech Republic, the U.K. and Italy showed recently that millions of products using chips from German semiconductor manufacturer Infineon Technologies are affected by a vulnerability related to a library responsible for generating RSA encryption keys.
The flaw, tracked as CVE-2017-15361 and dubbed ROCA (Return of the Coppersmith Attack), allows an attacker who knows the public key to obtain the private RSA key. Depending on what the product is used for, an attacker can use the compromised private key to impersonate legitimate users, decrypt messages, and forge software signatures.
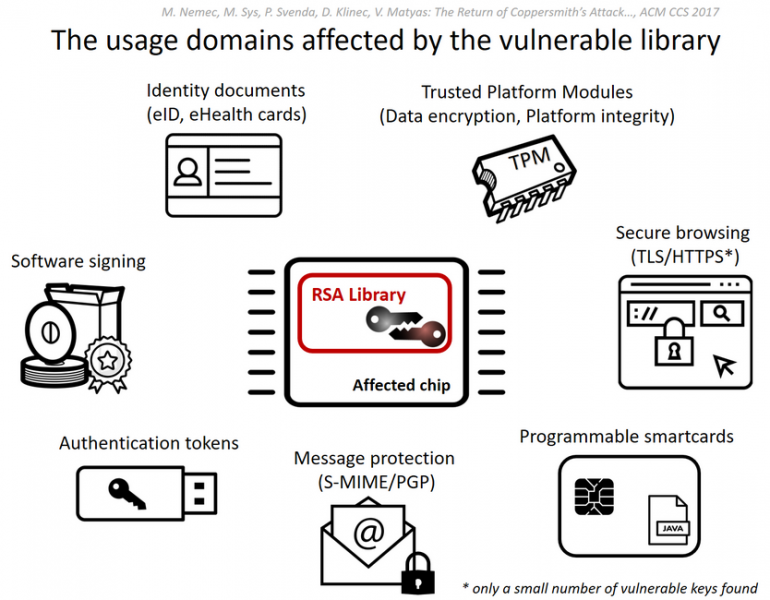
Microsoft, Google, HP, Lenovo, Fujitsu and other companies published advisories to warn customers of the risks. The flaw also impacts Gemalto’s IDPrime.NET smart cards, which are no longer sold by the firm but are still used by many organizations worldwide.
The vulnerability also affects Estonia’s national ID cards, which are also supplied by Gemalto. Estonia has decided to suspend roughly 760,000 ID cards, which are also used by citizens to vote, in response to the incident. The IDs used in other countries could be vulnerable as well, according to some reports.
Researchers said a 1024-bit RSA key can be cracked in 97 CPU days for a cost of $40-80 using an older Intel Xeon processor, and a 2048-bit key in 140 CPU years for a cost ranging between $20,000 and $40,000.
Estonia assured citizens that large-scale vote fraud would be too expensive to conduct – some estimated that the cost for hacking all ID cards would be roughly €60 billion ($70 billion) at a cost of approximately $80,000 per card.
However, researchers Daniel J. Bernstein and Tanja Lange pointed out over the weekend that the actual cost of obtaining the RSA keys was in reality much lower, even before they found a faster way to conduct an attack. Furthermore, they highlighted that vote fraud would not require all cards to be compromised as even 10% could make a difference.
The $80,000 estimate cited by Estonia refers to an initial algorithm used by the original authors of the research. They later managed to decrease costs to $20,000.
Bernstein and Lange attempted to conduct an attack using only the limited information made available by the original researchers. They not only managed to replicate the attack, but they also found a way to obtain a 2048-bit key 5-25% faster, which further reduces the cost of an attack.
Bernstein and Lange also noted that the issue with Infineon chips has actually been known since August 2016 and they are concerned that malicious actors may have been exploiting the flaw before the ROCA disclosure.
“Attackers could already have figured out the whole attack from [the 2016 research paper],” the experts said in a blog post. “Or attackers could have looked at Infineon keys on their own and found the same information. Our best guess is that serious attackers found the Infineon vulnerability years ago and have been quietly exploiting it since then.”













