Malicious cyber actors pose a serious threat to Europe’s industrial infrastructure, with at least ten hacker groups known to target European organizations, according to a new report from industrial cybersecurity firm Dragos.
The number of threat groups observed targeting organizations with industrial control system (ICS) or other operational technology (OT) environments has increased significantly over the past years. In February, Dragos said it had been tracking 18 such groups, including ones that have actually breached ICS/OT networks.
In a report published on Tuesday, Dragos said ten of the threat groups tracked by the company have conducted operations aimed at European entities, including disruptive and destructive attacks. These groups are tracked as Xenotime, Magnallium, Electrum, Allanite, Chrysene, Kamacite, Covellite, Vanadinite, Parisite, and Dymalloy. Some of these groups have been linked to China, Russia, Iran and North Korea.
In addition to these advanced persistent threats (APTs), Europe’s industrial sector is often also targeted by profit-driven cybercrime groups.
Learn more about threats to industrial organizations at
SecurityWeek’s ICS Cyber Security Conference
Of the roughly 3,200 OT-specific vulnerabilities tracked by Dragos, nearly 500 directly impact organizations in Europe, and over 100 of them can be exploited to cause loss of view and/or loss of control.
However, the cybersecurity firm believes Europe is at low risk for destruction or disruption campaigns targeting industrial infrastructure. From the report:
“Dragos assesses with moderate confidence Europe is at low risk for widespread Industrial Infrastructure-targeted destruction and disruption campaigns originating from cyberattacks due to the deterrence posed by potential political and economic impact as well as the direct effect on civilian lives and infrastructure.
Additionally, Dragos assesses with low confidence Europe is at a low risk for localized or small-scale disruption or destruction, as motivated state-executed adversaries may perform low-stakes operations when deemed politically or economically advantageous.”
On the other hand, there are various other threats that should not be ignored by European organizations, and one of them is ransomware. An analysis of the websites operated by various ransomware groups — these are the sites where cybercriminals name and shame victims to convince them to pay up — showed that roughly one-quarter of claimed victims are located in Europe, particularly in the manufacturing sector.
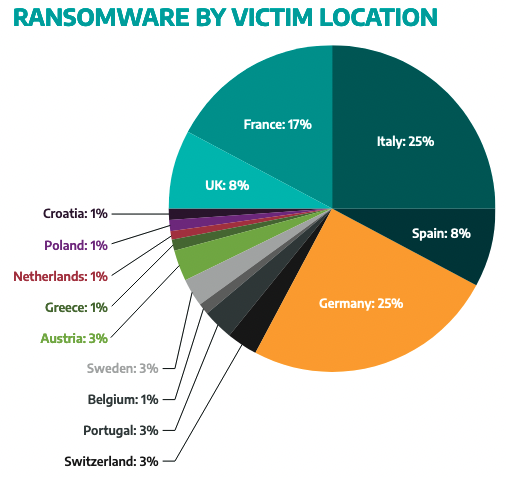
“Dragos assesses with moderate confidence ransomware operators will continue to target [Germany, Austria, Switzerland and Italy], and specifically manufacturing firms located in these countries, motivated by profit,” Dragos said. “While state-affiliated ransomware operations are extremely difficult to prove, Dragos assesses with low confidence this type of attack may occur in DAS+I countries and greater Europe.”
Dragos has also highlighted the threat posed to the oil and gas sector by groups such as Xenotime and Dymalloy. The report also highlights the threat to the UK’s energy sector — particularly small energy distributors and power stations — which may be targeted in ransomware or other disruptive attacks.
Dragos’ report, which also mentions the theft of intellectual property and insider threats, provides some recommendations for defenders.
“Dragos assesses with high confidence that the biggest cybersecurity weaknesses European asset owners currently face are a lack of asset visibility into their network and weak network authentication policies,” the company said. “Without asset visibility organizations are unable to properly secure their OT environments as defenders cannot protect what they cannot see. Industrial operators should evaluate and implement the principle of least privilege to limit unauthorized access to OT environments.”
Related: Increasing Number of Threat Groups Targeting OT Systems in North America
Related: Cybercriminals Target Industrial Organizations in Information Theft Campaign
Related: Ransomware Often Hits Industrial Systems, With Significant Impact












