A researcher from the Ben-Gurion University of the Negev in Israel has published a paper describing a method that can be used to silently exfiltrate data from air-gapped systems using the LEDs of various types of networked devices.
The new attack has been dubbed ETHERLED and it relies on the LEDs attached to the integrated network interface controller (NIC) of devices such as PCs, servers, printers, network cameras, and embedded controllers.
An attack scenario assumes that the attacker has somehow managed to gain access to the targeted air-gapped device — via social engineering, malicious insiders or a supply chain attack — to plant a piece of malware that collects sensitive data and uses a covert channel to exfiltrate it to the attacker.
Researcher Mordechai Guri showed that an attacker could transmit sensitive information such as passwords, encryption keys and even text files by encoding and modulating them over optical signals that rely on the blinking patterns or blinking frequency of the Ethernet LEDs.
The NIC typically has two LEDs: an activity LED that is usually green and a status LED that changes between green and amber depending on the link speed. For example, the status LED can be amber for 1 Gb connections, green for 100 Mb connections and it can turn off for 10 Mb connections.
There are several methods that can be used to control these LEDs, including via code that runs as a kernel driver or within the NIC firmware. This only works if the attacker has elevated privileges, but it also provides the highest level of control.
An attacker could also control the link status LED by using operating system commands to change the link speed of the Ethernet controller in order to cause the LED to turn green, amber or off. The attacker can also turn the status LED on or off by enabling or disabling the Ethernet interface.
In order to transmit the data, the attacker can use several types of modulation, including on-off keying (OOK), blink frequency, and color modulation.
When the OOK modulation is used, a ‘0’ bit is transmitted if the LED is turned off, and a ‘1’ bit is transmitted if the LED is turned on. When the blink frequency variant is used, the LED blinking at a certain frequency means ‘0’ and a different frequency means ‘1’. Also, each LED color can be used to encode a different bit — for example, green is ‘1’ and amber is ‘0’.
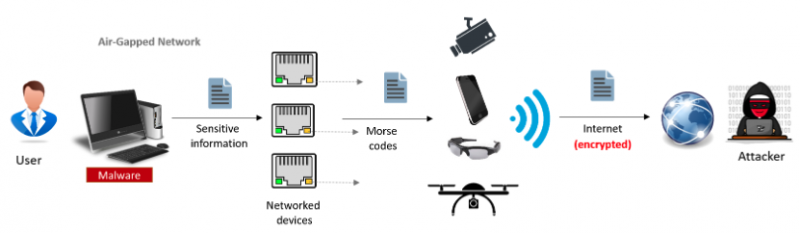
The transmitted data — that is, the blinking LEDs — can be recorded using various types of cameras. Experiments conducted by Guri showed that an HD webcam could record from up to 10 meters (32 feet), but a telescope could allow the attacker to capture the data from more than 100 meters (320 feet). A Samsung Galaxy phone’s camera can be used for distances of up to 30 meters (98 feet).
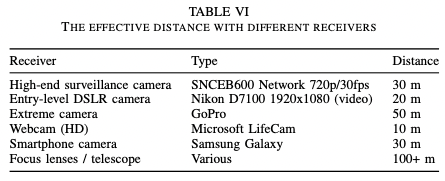
As for how quickly the data can be exfiltrated, it depends on the type of modulation that is used and the method used to control the LEDs. If the link status control is used with OOK and blink frequency modulation, only 1 bit/sec can be exfiltrated, but the maximum bit rate jumps to 100 bits/sec if the driver/firmware control method is used.
If driver/firmware control are used with two LED colors, a password can be exfiltrated in just one second and a Bitcoin private key in 2.5 seconds. A 1 Kb text file can be stolen in less than two minutes.
This is not the first time a researcher from the Ben-Gurion University of the Negev has presented a way to covertly exfiltrate data from air-gapped networks. In the past years, the university’s researchers showed how hackers could exfiltrate data using RAM-generated Wi-Fi signals, fan vibrations, heat emissions, HDD LEDs, infrared cameras, magnetic fields, power lines, router LEDs, scanners, screen brightness, USB devices, and noise from hard drives and fans.














