Enterprises Experience 643 “Advanced Malware” Infections Each Week
According to FireEye’s most recent threat report released today, organizations are seeing a massive increase in advanced malware that is working its way inside enterprise walls by bypassing traditional IT security defenses.
FireEye, a provider of anti-malware solutions, describes “advanced malware” as unknown threats previously unseen, that bypass traditional signature-based security defenses such as next-generation firewalls, IPS, gateways, and anti-virus.
These types of advanced malware attacks have spiked to the tune of a nearly 400% increase in the first half of 2012 vs. the first half of 2011, according to the report.
In fact, FireEye’s data shows that, on average, large and medium sized enterprises from many different vertical segments experience 643 advanced malware infections per week.
“Organizations are under persistent attack, and the attacks being waged continue to grow more dynamic, effective, and damaging,” the report said.
The trend of attacks becoming more targeted and increasingly sophisticated is nothing new, and FireEye researchers said that attackers are increasingly using techniques such as the use of limited-use domains in their spear phishing emails in order to evade traditional security defenses.
These advanced malware threats infiltrate organizations via several threat vectors—the Web, email, and files, the company said.
“Advanced threats are posing challenges to enterprises and government agencies across the board. Industries with intellectual property, customer information, or critical infrastructure to protect are particularly vulnerable to advanced threats,” FireEye explained.
Other Findings from FireEye’s Advanced Threat Report include:
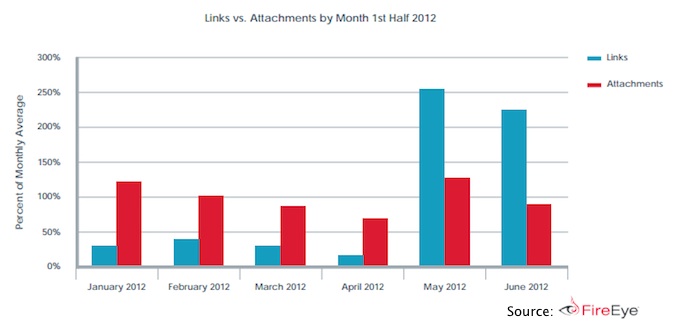
• Intensified danger of email-based attacks – FireEye researchers saw 56 percent growth in email-based attacks in 2Q 2012 versus 1Q 2012. Additionally, malicious links were more widely used than malicious attachments in the last two months of the second quarter of 2012.
• Increased use of dynamic, throw-away domains – FireEye saw a significant increase in dynamic links that were used five times or less. Originating from large-volume email-based attacks, links that were seen just once grew from 38% in the second half of 2011 to 46% in the first half of 2012.
• Industries with significant intellectual property or customer and financial data remain the primary targets as attacks increase.
“The results of this report make it even more clear that reactive signature-based defenses cannot prevent evasive strains of malware from making their way into the enterprise,” said Ashar Aziz, FireEye founder, CEO and CTO.
“As cybercriminals develop and invest in advanced malware, enterprises must reinforce their traditional defenses with a new layer of dynamic security that is able to detect unknown threats in real-time, thwarting malware communications back to command and control servers and blocking data exfiltration,” the company said.
As you could probably guess, FireEye sells the type of technology they are suggesting here, but nevertheless, the threats they are talking about are real.
“While web-based threats are significant, the dangers of email-based threats are growing more severe,” FireEye said. “Links and attachments delivered via email have been the source of some of the high-profile advanced persistent threat (APT) attacks such as the RSA breach, GhostNet, and NightDragon. These targeted spear-phishing emails are up, because they work. But, spear phishing emails are evolving with the use of malicious links becoming more prevalent than the use of malicious attachments.”
Interestingly, FireEye noticed that patterns of attack and trends varied substantially across industries, and that each industry seems to experiences peaks in attack volumes at different times.
Between January 2012 and June 2012, the number of events detected at healthcare organizations had nearly doubled. The report also highlighted that fact that technology companies are the most targeted organizations overall, as the overall number of attacks remain high compared to other industries. In the energy/utilities sector, there appears to be significant fluctuations in incidents, but overall the vertical has seen a large increase in attacks. In the past six months, the report shows, energy and utility organizations saw a 60% increase in security incidents.
“No industry or government agency is immune,” the report (PDF) concludes.
















