IT management software maker Kaseya is still working on patching the vulnerabilities exploited in the recent ransomware attack, but some cybercriminals are sending out emails offering the patches in an effort to distribute their malware.
The attack on Kaseya and its customers came to light on July 2. The company immediately shut down its VSA remote monitoring and management product to prevent further damage. An investigation revealed that the attackers exploited some zero-day vulnerabilities to deliver the REvil ransomware to the MSPs that use VSA, as well as the customers of those MSPs.
Kaseya has determined that only on-premises VSA installations are impacted and it has been working on patches for the exploited vulnerabilities, but it has yet to release the fixes due to some issues uncovered at the last moment.
However, some cybersecurity companies reported seeing a spam campaign that leverages news of the Kaseya patches to deliver a piece of malware.
The malicious emails, seen by Malwarebytes and Trustwave, carry subject lines related to package deliveries and they appear to come from an “Order Status” email account.
“Guys please install the update from microsoft to protect against ransomware as soon as possible. This is fixing a vulnerability in Kaseya,” the emails read.
The messages contain a link that appears to point to Kaseya’s official website, but it actually leads to an executable file (pload.exe) hosted on a remote server. The emails also contain an attachment named “SecurityUpdates.exe.”
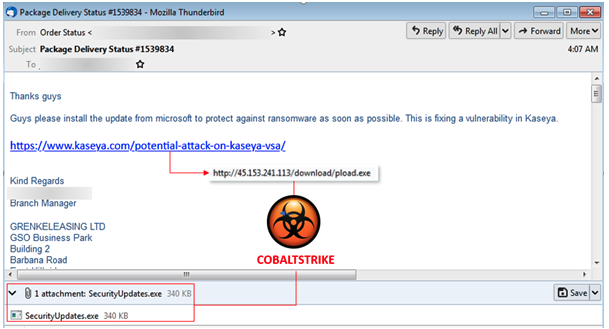
Both executable files hide CobaltStrike, a legitimate penetration testing tool that has often been abused by malicious actors in their attacks.
“The executable file loads a Cobalt Strike launcher that unpacks and executes a Cobalt Strike beacon.dll in memory and creates an encrypted tunnel between the infected host and the adversaries,” Trustwave explained in a blog post.
Continuous Updates: Everything You Need to Know About the Kaseya Ransomware Attack
Trustwave also analyzed the REvil (Sodinokibi) ransomware variant delivered in the Kaseya attack, and noted that it avoids encrypting files on systems that use Russian and other languages associated with former Soviet Union countries. While some media outlets covered this as if it was new, the fact that REvil avoids these countries has been known since 2019.
Kaseya plans on releasing patches for on-premises installations within 24 hours after restoring the VSA SaaS service, which was not impacted by the attack, but was shut down as a precaution. The SaaS service should have been restored on July 6, but there was a last minute issue and a new timeline has yet to be provided.
Researchers at managed detection and response company Huntress have reproduced the exploit chain used in the Kaseya attack.
The Dutch Institute for Vulnerability Disclosure (DIVD) reported several vulnerabilities to Kaseya in April, including ones exploited in the ransomware attack. The vendor had been in the process of creating patches, but the attack was launched before all of the flaws reported by DIVD could be fixed. DIVD on Wednesday shared more information on the types of issues it reported to Kaseya.
Kaseya said the attack only impacted roughly 50 of its direct customers, and between 800 and 1,500 of their customers. However, some experts believe the actual number of affected organizations is higher.
Related: Hackers Demand $70 Million as Kaseya Ransomware Victim Toll Nears 1,500 Firms













