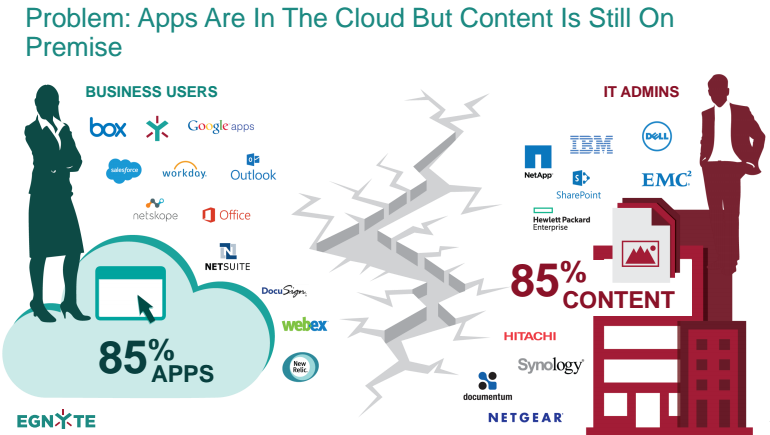
Cloud computing remains a problem for many businesses. While the move to IaaS is gathering pace, it is still true that most organizations operate a hybrid approach, combining cloud apps and on-premise data. According to Egnyte, 85% of apps are now in the cloud, while 85% of data is still on premises. This creates a huge governance issue as corporate data moves into and out of cloud applications.
Egnyte itself started life as one of those apps – a business-oriented file store, sync and share service. Now it claims to have taken everything it has learned about governance issues, international privacy concerns and geographical regulations to create a new product launched today: Egnyte Protect. “While our roots have been in the Enterprise File Sync and Share space,” explains CEO Vineet Jain, “we saw a real opportunity to capitalize on all the analytics we acquired and learned from our platform file usage to help customers get smarter about how they manage their content.”
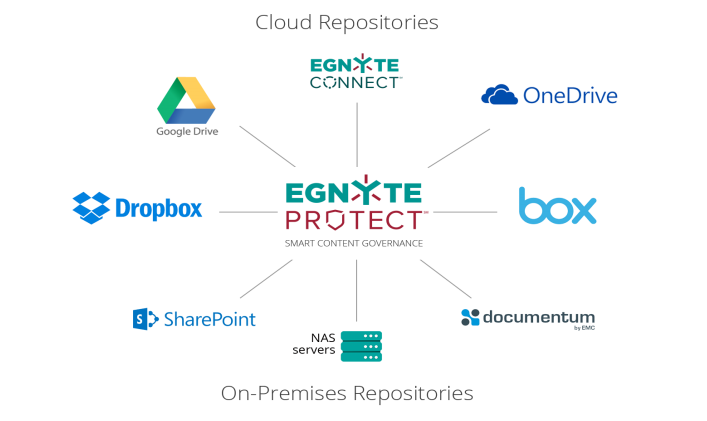
Companies store their data in multiple cloud applications – the enterprise might have a Box account while employees might also use Dropbox, Drive or OneDrive. Egnyte Protect doesn’t care. It will provide IT with data governance controls wherever that data might go.
The first release today provides access control. It can be used to eliminate insecure links, to unify permissions across content repositories, and to locate unusual access patterns to help locate and limit data leakage.
Three other modules will be added in the future: selective encryption, data residency and data retention. The encryption module will allow selected files to be encrypted locally and remain encrypted wherever they are stored. In this case the encryption keys remain with the company and are not held or known by the cloud service provider.
The data residency module will allow users to control where the data is stored; locally, in the cloud, in specified geographic regions or even specified cloud companies.
The data retention module will govern the life-cycle files, allowing the user to specify how long files should be retained and who can access or modify them.
At a time when many countries require that at least some types of data must remain within national borders, and the EU is applying strict and heavily sanctioned rules on all European personal information, Egnyte Protect is designed to give its customers the tools to apply strict governance and security rules on all of their data, wherever it goes.
“Data governance is an area IT departments historically tend to shy away from because of the perceived effort and time to value when it comes to creating and enforcing policies,” comments Sean Pike, program director, eDiscovery and Information Governance at IDC. Most organizations need to hire experts, invest in equipment and spend months figuring out the right implementation – modifying policies as they uncover issues. This is the problem that Egnyte Protect claims to have solved.













