A recently discovered variant of the KillDisk malware encrypts files and holds them for ransom instead of deleting them. Since KillDisk has been used in attacks aimed at industrial control systems (ICS), experts are concerned that threat actors may be bringing ransomware into the industrial domain.
Previous versions of KillDisk wiped hard drives in an effort to make systems inoperable, but a new variant observed by industrial cyber security firm CyberX encrypts files using a combination of RSA and AES algorithms. Specifically, each file is encrypted with an individual AES key and these keys are encrypted using an RSA 1028 key stored in the body of the malware.
CyberX VP of research David Atch told SecurityWeek that the KillDisk variant they have analyzed is a well-written piece of ransomware. The code is similar to earlier samples and its functionality is nearly the same.
The ransomware is designed to encrypt various types of files, including documents, databases, source code, disk images, emails and media files. Both local partitions and network folders are targeted.
Victims are instructed to pay 222 bitcoins ($210,000) to recover their files, which experts believe suggests that the attackers are targeting “organizations with deep pockets.” The contact email address provided to affected users is associated with Lelantos, a privacy-focused email provider only accessible through the Tor network. The Bitcoin address to which victims are told to send the ransom has so far not made any transactions.
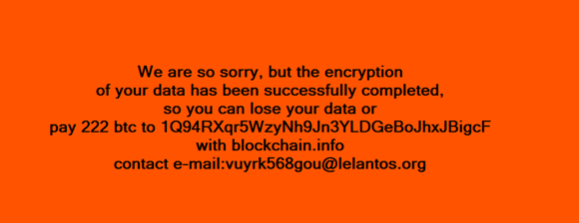
Atch pointed out that the same RSA public key is used for all samples, which means that a user who receives a decryptor will likely be able to decrypt files for all victims.
According to CyberX, the malware requires elevated privileges and registers itself as a service. The threat terminates various processes, but it avoids critical system processes and ones associated with anti-malware applications, likely to avoid disrupting the system and triggering detection by security products.
“Important thing to notice about the malware, the author/s are familiar with the crypto API, they are using some of it’s functions to generate truly random numbers,” Atch explained. “But they decided to avoid using the function CryptDecrypt, probably because this function can be easily hooked. Hooking the function may provide an Anti-Malware software an easy way of dealing with unwanted file encryption, the hooking will provide an ability to restore the keys.”
KillDisk evolution to ransomware
Earlier this month, security firm ESET published a report detailing attacks conducted by a threat group dubbed TeleBots. Researchers believe TeleBots is an evolution of the Russia-linked BlackEnergy (Sandworm) group, which is said to be responsible for several attacks on ICS/SCADA systems, including the December 2015 operation aimed at Ukraine’s energy sector.
One of the tools used by the BlackEnergy actor is KillDisk, a piece of malware originally designed to delete files and make systems inoperable. In the attacks that caused power outages in Ukraine, KillDisk was used to make it more difficult for affected power companies to restore service.
In recent cyber-sabotage campaigns launched against high-value targets in Ukraine’s financial sector, TeleBots used various tools, including a new version of KillDisk. This malware, used in the final stages of the attack, was executed with high privileges on servers and workstations after attackers likely obtained administrator credentials in the previous stages of the operation.
In these attacks, KillDisk was configured to activate at a predefined date and time. In addition to deleting important system files, it was set up to overwrite files with certain extensions – largely the same types that the ransomware variant encrypts.
CyberX believes threat actors turned KillDisk into a piece of ransomware because, unlike cyber-sabotage, the new functionality enables them to directly monetize their attacks.
Experts pointed out that industrial organizations can be an ideal target for ransomware for several reasons, including the fact that cyber-disruptions can result in physical safety risks and production outages, network operations typically cannot be easily shut down, data backup processes may not cover all the required data, and the employees of industrial organizations might be less aware of cyber threats.
“Enterprises are more likely to quietly pay the ransom because of concerns that going public with cyberattacks will invite greater scrutiny from regulators, and possibly fines (environmental, safety, etc.),” said Phil Neray, VP of industrial cybersecurity at CyberX.
Related: Ukraine Power Outage Possibly Caused by Cyberattack
Related: BlackEnergy, KillDisk Infect Ukrainian Mining, Railway Systems














