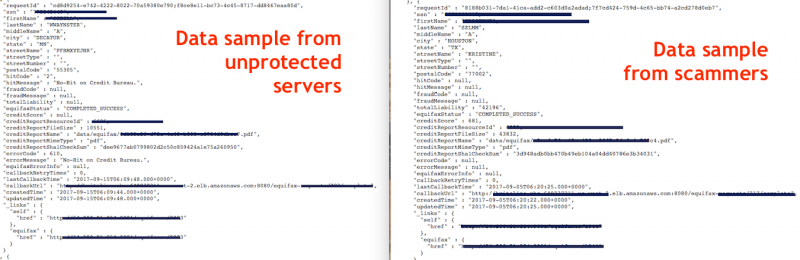
A data sample provided last month by scammers trying to make a profit by claiming to have breached U.S. credit reporting agency Equifax may have been obtained from unprotected Amazon Web Services (AWS) instances owned by a different company.
Hackers exploited a known Apache Struts vulnerability to breach the systems of Equifax. They had access between mid-May and late July and they may have stolen the details of over 145 million consumers in the United States, Canada and the United Kingdom. The compromised information included names, social security numbers (SSNs), dates of birth, addresses and, in some cases, driver’s license numbers, credit card numbers and dispute documents.
Scammers have been trying to make a profit by claiming to sell the stolen Equifax data for several hundred bitcoins, worth millions of dollars. One scam was run by a group calling itself Equihax, which leaked the records of Donald Trump, Kim Kardashian and Bill Gates to prove that they had the Equifax data. They also provided the records of a non-famous individual in an effort to convince people that they were the real Equifax hackers.
While they likely haven’t breached the credit reporting agency, they still may have obtained some Equifax customer data, but not from Equifax itself.
Researchers Aditya K Sood and Rehan Jalil had been looking for potentially new cloud threats when they identified several unprotected AWS instances that referenced Equifax.
“Upon accessing the HTTP service hosted on TCP port 9000/9001, we found that the web server returned a list of APIs,” Sood and Jalil explained in a blog post. “We then queried one of the APIs and found that it was possible to retrieve data.”
While the misconfigured databases reference Equifax, the researchers determined that they actually belong to an unnamed securities lending company based in Chicago. More precisely, they are part of the firm’s QA systems. Some of the data stored in cleartext in the unprotected AWS cloud storage instances was valid, but some of it appeared to be test data, the experts said.
A data sample provided by Sood to SecurityWeek after querying the unprotected servers was in the exact same format as the data shared by scammers, which could mean they and possibly others also discovered these servers.
“It could be possible that scammers utilized this security flaw as well. The data dump is the same,” Sood told SecurityWeek.
Sood and Jalil have not named Equifax in their blog post – they only reference a “credit bureau” – but there are various strings referencing “equifax” in the data they found. The credit bureau (i.e. Equifax) has confirmed to the researchers that it does not control the servers exposing data.
The securities lending firm was contacted by the researchers, but it had not taken any action to protect the servers as of October 8. However, some of the sensitive data stored in the databases was encrypted between September 15, when the experts first found the servers, and October 8, when they conducted additional tests.
The relationship between Equifax and the securities lending company is unclear. Equifax has not responded to SecurityWeek’s inquiry regarding these unprotected systems.
Related: Equifax Website Redirects Users to Adware, Scams
Related: Equifax Sent Breach Victims to Fake Website
Related: Equifax Cybersecurity Failings Revealed Following Breach