Thousands of individuals and hundreds of organizations across six continents have been targeted by the same hack-for-hire group over the past several years, Citizen Lab reveals in a new report.
Referred to as Dark Basin and linked to Indian company BellTroX InfoTech Services, the threat actor is believed to have targeted senior politicians, government prosecutors, CEOs, journalists, and human rights defenders, among others.
As part of an investigation that started in 2017, Citizen Lab identified around 28,000 shortened URLs containing e-mail addresses of targets. Initially suspected to be state-sponsored, the threat actor was later identified as a hack-for-hire operation, given the variety of targets.
The group is suspected of conducting commercial espionage on high-profile public events, criminal cases, financial transactions, news stories, and advocacy.
Attribution to BellTroX InfoTech Services
Citizen Lab is confident that the activity is the work of BellTroX InfoTech Services. The company’s director, Sumit Gupta (also known as Sumit Vishnoi), was indicted in 2015 by U.S. authorities for participating in a similar hack-for-hire scheme.
Gupta appears to have never been arrested in relation to the indictment. In fact, hack-for-hire companies continue to promote their services despite several indictments from the Department of Justice, suggesting that they do not expect to face legal consequences.
Citizen Lab linked the activity to India because hundreds of phishing emails associated with Dark Basin show timestamps consistent with working hours in India’s time zone, and the same timestamps were observed in phishing kit source code the group left openly online. Moreover, several of the employed URL shortening services had names associated with India: Holi, Rongali, and Pochanchi.
Furthermore, several individuals involved in the operation used personal documents, including a CV, as bait content when testing their URL shorteners, which allowed the researchers to link them to BellTroX. They also advertised some of their operations in social media posts, and included screenshots of links to Dark Basin infrastructure.
The company’s website claims a mixture of services, such as cybercrime investigation and social engineering assessment, while BellTroX staff activities listed on LinkedIn include email penetration, exploitation, corporate espionage, phone pinger, and conducting cyber intelligence operations. The BellTroX website was taken down just days before Citizen Lab published its report and some of the incriminating materials were removed recently.
BellTroX and its employees received endorsements on LinkedIn from an individual claiming to be an official in the Canadian government, an investigator at the US Federal Trade Commission (previously a contract investigator for US Customs and Border Patrol), local and state law enforcement officers, and private investigators (many with prior roles in the FBI, police, military and other branches of government).
“Dark Basin has a remarkable portfolio of targets, from senior government officials and candidates in multiple countries, to financial services firms such as hedge funds and banks, to pharmaceutical companies. Troublingly, Dark Basin has extensively targeted American advocacy organizations working on domestic and global issues. These targets include climate advocacy organizations and net neutrality campaigners,” Citizen Lab notes.
Targeting the #ExxonKnew campaign
In 2017, Citizen Lab discovered that multiple individuals and organizations engaged in environmental issues in the US were targeted, likely because they were all linked to the #ExxonKnew campaign, which points to Exxon’s decades-long knowledge of climate change.
The targets include Rockefeller Family Fund, Climate Investigations Center, Greenpeace, Center for International Environmental Law, Oil Change International, Public Citizen, Conservation Law Foundation, Union of Concerned Scientists, M+R Strategic Services, and 350.org.
The #ExxonKnew campaign was first discussed by a group of environmental organizations and funders at a private meeting in January 2016. Campaigners were invited to the meeting via a private email that was later leaked to two newspapers.
All but two recipients of the leaked January email were identified as Dark Basin targets. The targeting spiked in February and March 2016, and then in June and July 2017, after the New York Attorney General made a filing alleging evidence of “potential materially false and misleading statements by Exxon.” Another spike was observed before New York’s Attorney General filed a lawsuit against ExxonMobil in January 2018.
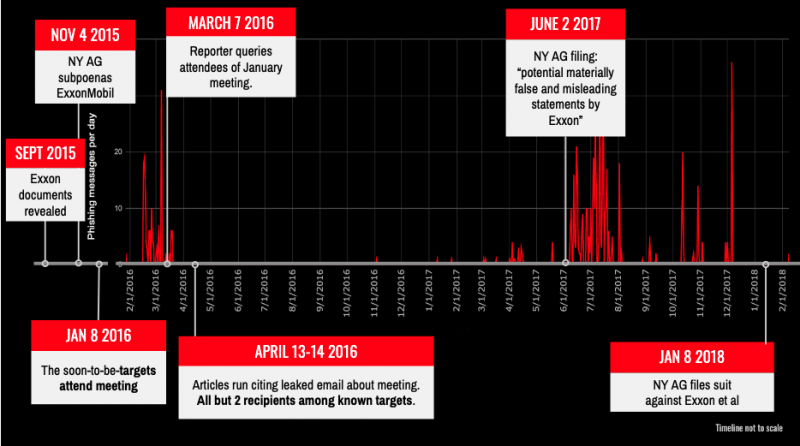
Phishing emails were sent to both personal and institutional email accounts, and both individuals involved in the #ExxonKnew campaign and their family members were targeted, indicating “both the well-informed nature of the targeting, and an intelligence gathering objective.”
Citizen Lab points out that Dark Basin operators were likely provided with specific details on whom to target and what lures to use, and says it cannot conclude with high confidence who commissioned the attacks.
“We are not conclusively attributing Dark Basin’s phishing campaign against these organizations to a particular Dark Basin client at this time,” the researchers say.
Other targets
Dark Basin also targeted at least two American advocacy groups during a period when they were asking the Federal Communications Commission (FCC) to preserve net neutrality rules in the US. Non-governmental organizations Fight for the Future and Free Press were targeted between July 7 and August 8, 2017. Other US civil society groups were targeted as well, along with journalists from multiple major US media outlets.
Dark Basin targeted a large number of industries, but the financial sector appears to have been hit the most, Citizen Lab reports. The most prominent targeting involved a cluster of hedge funds, short sellers, journalists, and investigators of market manipulation at German payment processor Wirecard AG.
International banks and investment firms, and prominent corporate law firms in the US, Asia, and Europe were also targeted, the same as companies involved in offshore banking and finance. Furthermore, Dark Basin targeted individuals in major US and global law firms, working on corporate litigation and financial services in the US, UK, Israel, France, Belgium, Norway, Switzerland, Iceland, Kenya, and Nigeria.
Citizen Lab also identified targets pertaining to the energy and extractive sectors, including petroleum companies, targets in Eastern and Central Europe, and Russia (associated with extremely wealthy individuals), and targets in multiple governments (senior elected officials, members of the judiciary, prosecutors, members of parliament, and political parties).
Regularly updated TTPs
The researchers also observed Dark Basin regularly adapting tactics, techniques, and procedures (TTPs): they sent phishing emails from a range of emails and adapted the bait content, message volume, and persistence over time, supposedly based on received payment.
Over a period of nearly a year and a half, the hack-for-hire group used 28 unique URL shortener services, and the researchers identified a total of 27,591 different long URLs leading to Dark Basin credential phishing websites. They also discovered that the target’s email address was often included in the URL. Dark Basin created phishing websites for a variety of web services used or operated by the target or their organization.
“This campaign operated at a scale we had not previously detected in our research into targeted intrusion operations (versus generic phishing operations),” Citizen Lab notes.
The researchers also discovered that the operators left the source code of their phishing kit openly accessible. This revealed interactions with credential phishing websites, including testing activity that Dark Basin operators carried out, as well as scripts meant for processing information entered by the victim, including usernames and passwords.
Successful with at least some of their phishing campaigns, Dark Basin operators were employing commodity VPNs to access accounts using stolen credentials.
“Dark Basin’s reliance on a rarely seen URL shortener software, continued reuse of the same registration identities and hosting providers for their infrastructure, and the uniqueness of their phishing kit all contributed to our ability to track them continuously during these campaigns. Perhaps most important however was the additional visibility provided by working closely with the targeted individuals and organizations,” Citizen Lab notes.
Dark Basin’s activity, the researchers say, clearly indicates that hack-for-hire is a serious problem for all sectors of society, from politics, advocacy and government to global commerce. Allowing companies to outsource specific activities, the hack-for-hire industry is likely growing, fueled by normalization of other forms of commercialized cyber offensive activity, such as digital surveillance and “hacking back,” and the growth of the private investigations industry.
“We believe it is especially urgent that all parties involved in these phishing campaigns are held fully accountable. For this reason, and on the request of multiple targets of Dark Basin, Citizen Lab provided indicators and other materials to the US DOJ,” Citizen Lab also says.
Related: Report Reveals Widespread Use of Pegasus Spyware
Related: Report Links Vast Online Disinformation Campaign to Iran















