A new piece of ransomware named Epsilon Red has been used to target at least one organization in the United States, and its operators have apparently already made a significant profit.
Cybersecurity firm Sophos reported last week that Epsilon Red operators have been spotted targeting a US-based company in the hospitality sector. The cryptocurrency address provided by the cybercriminals shows a bitcoin transaction for an amount worth roughly $210,000, which seems to indicate that at least one victim has agreed to pay the ransom demanded by the cybercriminals.
Sophos researchers noticed that the ransom note dropped by Epsilon Red is similar to the one displayed by the REvil ransomware, but Epsilon Red’s ransom note is better written — it does not contain some of the grammar errors in the REvil note.
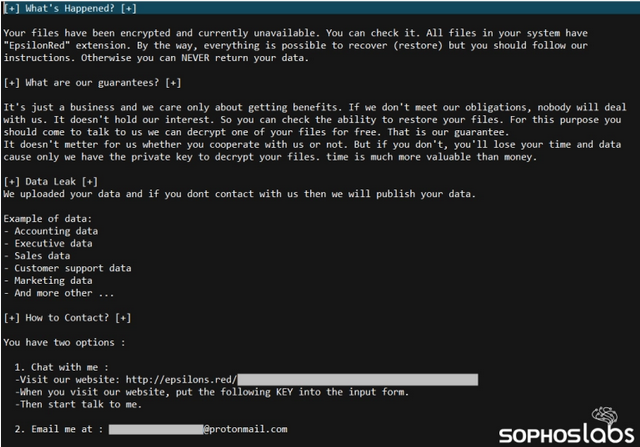
Victims are informed that their files have been encrypted and that their data has been stolen and will be leaked unless they pay the ransom. However, Sophos noted that the ransomware doesn’t contain a list of targeted file types and instead encrypts every file in a folder, which can lead to the entire system becoming inoperable.
Epsilon Red, developed in the Go language, has been described as “bare-bones ransomware.” The ransomware executable is small due to the fact that it’s only designed to scan the system for folders it can encrypt and perform the actual encryption. The remaining tasks are carried out by a dozen PowerShell scripts, which prepare the machine for the final encryption payload.
These PowerShell scripts are designed to modify firewall rules to allow the attackers’ remote connections, disable or kill processes that could prevent encryption, delete the Volume Shadow Copy to prevent recovery of encrypted files, delete Windows event logs, grant elevated permissions, uninstall security software, and obtain valuable data.
The attackers have also been spotted using Remote Utilities, a commercial solution that is available for free. Sophos researchers believe the attackers have used this tool to be able to maintain access to compromised systems in case their initial access point gets removed.
The initial access point in the attack spotted by Sophos was likely an unpatched Microsoft Exchange server. The attackers may have leveraged the vulnerabilities known as ProxyLogon, which have been exploited by many threat groups in the past months.
Sophos said it had not found any links to other cybercrime groups — except for the REvil ransom note similarities — and noted that the name Epsilon Red stems from an X-Men villain who has Russian origins.
Related: Security Researchers Dive Into DarkSide Ransomware
Related: SonicWall Zero-Day Exploited by Ransomware Group Before It Was Patched















