Security researchers from Trend Micro have shared details on an attack targeting personnel at government agencies in Europe and Asia, the latest of many attacks that have exploited CVE-2012-0158, a vulnerability in Microsoft Office.
As is the case in a majority of targeted attacks, the attackers used a phishing email, which in this case purported to be from the Chinese Ministry of National Defense, and was sent to 16 officials representing European countries.
According to Trend Micro’s Jonathan Leopando, the email included a malicious attachment, which exploits CVE-2012-0158, a popular vulnerability leveraged in targeted attacks, but one that was patched more than a year ago.
Register for Free Webcast:
Addressing the Open Doors in Your APT Strategy – July 17th 1PM ET
In what was sloppy attack execution, the email appeared to have been sent from a Gmail account and did not use a Chinese name.
“The exploit is used to drop a backdoor onto the system, which steals login credentials for websites and email accounts from Internet Explorer and Microsoft Outlook,” Leopando explained in a blog post. “It also opens a legitimate “dummy” document, to make the target believe that nothing malicious happened. Any stolen information is uploaded to two IP addresses, both of which are located in Hong Kong.”
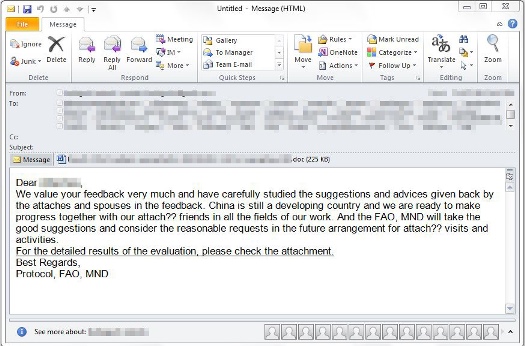
(Phishing Email Used. Image Credit: Trend Micro)
Interestingly, Trend Micro noted that that Chinese media organizations were also targeted in the attack.
The backdoor itself has been detected in the wild, but has been most frequently detected in China and Taiwan, with a more limited presence in other Asian countries, Trend Micro said.
Trend Micro detects the malicious attachment is as TROJ_DROPPER.IK and the backdoor itself as BKDR_HGDER.IK.
This latest attack is just one of many campaigns targeting CVE-2012-0158. Other recent attacks capitalizing on CVE-2012-0158 include, “Safe” (originally called SafeNet by Trend Micro), Taidoor, and even “Operation Red October”, a complex cyber espionage campaign uncovered by Kaspersky Lab in January. Red October targeted specific groups throughout the world for over five years and used CVE-2012-0158 as one of several vulnerabilities exploited as part of the advanced attacks.
In April 2013, researchers from FireEye discovered malware that targeted CVE-2012-0158 used in attacks targeting governments in the Middle East and Central Asia. That malware, called Trojan.APT.BaneChant, monitors mouse clicks to determine whether or not it is being analyzed in a sandbox.
Just last month, researchers from Rapid7 discovered a series of attacks targeting users in Vietnam and India that infected users with a backdoor designed to steal massive amounts of information. Dubbed “KeyBoy”, the malware used weaponized attachments that targeted CVE-2012-0158, along with CVE-2012-1856.
Also in June, FireEye researchers uncovered a campaign that used Google Docs to redirect victims and evade callback detection mechanisms. The document used in the attack exploits CVE-2012-0158, and creates a decoy document and a malware dropper named exp1ore.exe.
In May, researchers from ESET discovered another attack leveraging CVE-2012-0158 that targeted organizations in Pakistan and other nations.
Register for Webcast: Addressing the Open Doors in Your APT Strategy – July 17th 1PM ET














