Austria-based crane manufacturer Palfinger on Monday informed customers that its IT infrastructure suffered serious disruptions as a result of an “ongoing global cyber attack.”
Only limited information has been shared about the incident, but the company says the attack disrupted its email and enterprise resource planning (ERP) systems. The crane maker said a “large proportion” of its worldwide locations have been hit.
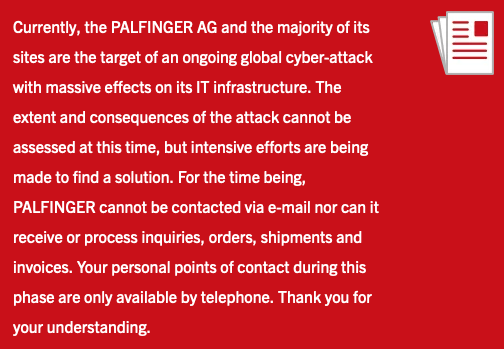
“Currently, the PALFINGER AG and the majority of its sites are the target of an ongoing global cyber-attack with massive effects on its IT infrastructure. The extent and consequences of the attack cannot be assessed at this time, but intensive efforts are being made to find a solution,” reads a message currently greeting users who access the company’s website. “For the time being, PALFINGER cannot be contacted via e-mail nor can it receive or process inquiries, orders, shipments and invoices. Your personal points of contact during this phase are only available by telephone.”
Palfinger’s description of the incident suggests that it may be a breach involving a piece of ransomware.
SecurityWeek has reached out to the company for more information and will update this article if it responds.
Palfinger provides lifting, loading and handling solutions to organizations in the construction, forestry and agriculture, industrial, infrastructure, railway, government, transportation and logistics, and waste management and recycling sectors. The company says it has 11,000 employees across 35 locations.
Also on Monday, American packaging giant WestRock informed customers that it was recently targeted in a ransomware attack that impacted both IT and OT systems.
UPDATE: Palfinger told SecurityWeek that the attackers have “partly encrypted data on several IT systems” belonging to the company, which confirms that this was a ransomware attack.
The company has shared the following statement:
PALFINGER AG is prepared for such a scenario and immediately set up a task force consisting of internal and external IT and forensics experts, who are currently conducting a thorough investigation of the incident.
At the same time, the law enforcement authorities have been called in and a criminal complaint has been filed. In addition, the responsible data protection authorities in Austria and abroad have been notified. As most of our employees are currently unable to continue their work, the Management Board has decided to reduce all operational activities to a minimum or to suspend them where necessary. Of course, we are keeping our customers, employees and the media continuously up to date and will provide the latest information in a timely manner.
Related: University Project Tracks Ransomware Attacks on Critical Infrastructure
Related: HR Giant Randstad Hit by Egregor Ransomware
Related: Metro Vancouver Transportation Agency TransLink Hit by Ransomware















