The number of attacks abusing the remote desktop protocol (RDP) to compromise corporate environments has increased significantly over the past couple of months, Kaspersky reports.
With employees worldwide forced to work from home due to the current COVID-19 pandemic, the volume of corporate traffic has increased significantly, just as the use of third-party services to keep teams connected and efficient.
Furthermore, organizations were forced to expose additional systems to the Internet to provide their employees with remote access, and cybercriminals have already started to take advantage of the situation.
According to Kaspersky, the number of brute-force RDP attacks has rocketed all around the world. At the beginning of March, the security company was observing in the low hundreds of thousands of RDP attempts per country, per day, but the volume grew to nearly 1 million attacks per day toward the end of the month, in some countries. In others, it spiked well above the million mark.
“The lockdown has seen the appearance of a great many computers and servers able to be connected remotely, and right now we are witnessing an increase in cybercriminal activity with a view to exploiting the situation to attack corporate resources that have now been made available (sometimes in a hurry) to remote workers,” Kaspersky says.
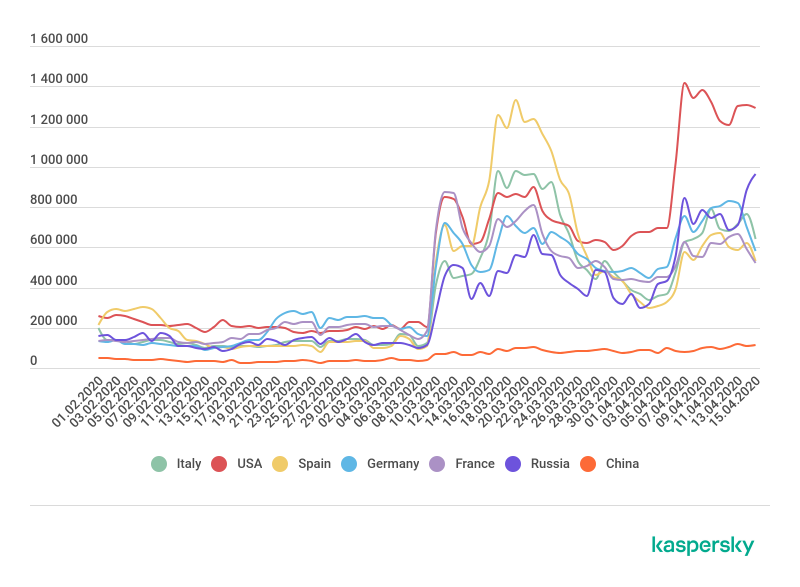
Adversaries attempt to connect to Windows workstations or servers through Microsoft’s proprietary protocol by systematically trying common or weak username and password combinations or random characters, until the correct one is found.
Brute-force attackers hypothesized that the number of poorly configured RDP servers would increase following the mass transition to working from home, and immediately attempted to take advantage of the situation.
According to Kaspersky, the attacks on remote-access infrastructure and collaboration tools will likely continue for a long period of time.
Organizations that employ RDP for their work are advised to adopt strong passwords, ensure that RDP is available through a corporate VPN only, set up and use Network Level Authentication (NLA), enable two-factor authentication, and disable and close the RDP port (port 3389) if the protocol is not used.
“Companies need to closely monitor programs in use and update them on all corporate devices in a timely manner. This is no easy task for many companies at present, because the hasty transition to remote working has forced many to allow employees to work with or connect to company resources from their home computers, which often fall short of corporate cybersecurity standards,” Kaspersky concludes.
Related: Nation-backed Hackers Tune Attacks to COVID-19 Fears: Google
Related: Organizations Warned of Dual Threat Posed by RDP and Disruptive Ransomware
Related: RDP-Capable TrickBot Targets Telecoms Sectors in U.S. and Hong Kong














