Many organizations are still having difficulties protecting their systems against the most common infiltration, exfiltration and lateral movement methods used by attackers, according to the latest Hacker’s Playbook report from SafeBreach.
The company provides a platform designed to test an organization’s defenses by continuously simulating attacks and breaches. For the third edition of its Hacker’s Playbook report, SafeBreach has analyzed data from roughly 11.5 million automated simulations conducted between January and November 2017. The simulations covered more than 3,400 attack methods – from exploit kits and malware to brute force and credential harvesting – that allowed the company to see where attackers are blocked and where they are successful.
An analysis of the top 5 infiltration methods used by malware showed that more than 55 percent of attack attempts are successful. The methods used by notorious malware families such as the WannaCry ransomware, which leverages SMB, and the Carbanak (Anunak) banking Trojan, which relies on HTTP, had a success rate of 63.4% and 59.8%, respectively, in SafeBreach’s simulations.
Other popular infiltration methods involve malicious executables packed in CHM, VBS and JavaScript files. These help attackers trick both end users and high-level scanners, and they had success rates between 50% and 61%.
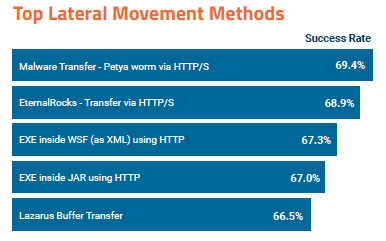
Once they gain access to a targeted organization’s network, attackers use various methods for lateral movement. The most common methods, all of which involve a piece of malware or exploit, were successful in 65%-70% of the simulations run by SafeBreach.
The relatively high success rates show that organizations often fail to implement proper segmentation controls. Once the perimeter has been breached, there is no malware scanning in place within the network, allowing attackers to easily move from one machine to another.
As for exfiltrating data, success rates range between 40% and 57% for methods involving MySQL queries, TLS, SSL, HTTP POST and HTTP GET. The most commonly targeted ports are 123 (NTP), 443 (HTTPS), and 80 (HTTP).
“Attackers will always try the easiest routes first – and sadly, it appears they will often find success,” SafeBreach said in its report. “Techniques like DNS tunneling, or trickling data out within packet headers to slowly steal data without raising suspicion are clever, but attackers don’t get bonus points for creativity. When simply sending data outbound via clear or encrypted web traffic will work – attackers will happily take the easy way out.”
“We also took a deeper look into this traffic, and validated that indeed traditional web traffic, over traditional web ports, is the leading risk of data exfiltration. However, some sneakier tactics were also highlighted, as we were often able to sneak data out over NTP – which is often open and unscanned,” the company added.
WannaCry, Locky and Cryptolocker have made many organizations realize that ransomware should be taken seriously. However, SafeBreach found that these types of attacks are often successful even if the deployed security solutions are working as designed.
The security firm pointed out that most of its customers have managed to significantly reduce attack success rates simply by optimizing existing security controls.
“Security teams already have the tools/controls they need for security. Oftentimes, teams chase after every new security fad, when they should be optimizing their current technology,” SafeBreach told SecurityWeek.
Related: Researchers Devise “Perfect” Data Exfiltration Technique
Related: SafeBreach Raises $15 Million to Give Enterprises a ‘Hackers View’













