The Cloud is Very Different, but the Approach to Adoption Needs to go Back to Basics. Buyer Beware? No, buyer be Smart and Educated.
Senior managers and decision makers have to be educated on the risks that they are exposing their companies and organizations to when they jump on the band wagon and move to the cloud. Senior managers can be seduced by tales of ROI. Or they can be drawn to focusing on core competencies, getting off the IT OPEX express, or always funding a technology refresh. These are all good reasons to move to a cloud, but the cloud is a mysterious place. Is it a new hype, a fad, something that will change everything? It depends on who you ask. I tend to believe that although it is going to change a lot, there are some real qualities that the cloud brings to an organization. These qualities make its adoption attractive, and seem to provide a way forward into the next decade. Among other qualities, it’s elastic, quickly provisioned, and you only pay for what you eat– a real edge on ROI.
 But what I would like to discuss is the security of the cloud, which apparently remains a bit of a mystery to many senior managers as well. As someone who has worked for a cloud provider, I have seen the same security questions and confusions over and over– about who does what to whom, and for each generally accepted cloud model. There is not a lot to understand, but it is something that needs to be understood if someone is going to get into the cloud with two eyes open and no (unpleasant) surprises.
But what I would like to discuss is the security of the cloud, which apparently remains a bit of a mystery to many senior managers as well. As someone who has worked for a cloud provider, I have seen the same security questions and confusions over and over– about who does what to whom, and for each generally accepted cloud model. There is not a lot to understand, but it is something that needs to be understood if someone is going to get into the cloud with two eyes open and no (unpleasant) surprises.
Remember, you can outsource the effort, time, and control – but the risk remains! Always remember the following three rules:
1) The cloud security model is SHARED between the customer and the provider, and is different for each flavor of cloud service: IaaS, PaaS, and SaaS.
2) (See Rule #1!) The consumer can get into trouble if they do not understand rule number 1 and the risks associated with those differences.
3) The consumer can outsource infrastructure, platform, and software (the I, P, S in IaaS, PaaS, and SaaS respectively) to the cloud, but they cannot outsource risk. So, regardless of who does what to whom by way of security responsibilities, the consumer’s risks are the consumer’s, and if things go wrong, the consumer suffers.
Again, although there is nothing new here, it does take a deliberate effort and a total understanding of who does what to make sure your organization’s risk is understood. Start at the beginning. The definitions of exactly what the cloud means in its permutations must be agreed upon before any meaningful investigation of the security model. The National Institutes Standards and Technology (NIST) has published a paper on cloud computing which is considered the de facto standard for what the cloud means and should do. Anyone considering a cloud implementation should read this document for the purposes of understanding what each service and product offering a cloud provider might bring to the table. The security model for all cloud-based services is SHARED. The cloud provider owes you some things and you are responsible for some things. The model shifts across the three different types of cloud services: Iaas, PaaS, and SaaS.
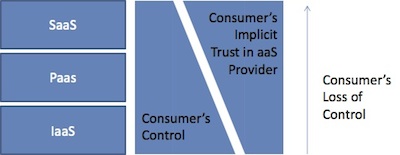 The shared security model involves greater consumer responsibility with IaaS. This leaves the security of everything except the underlying technology to the customer and the burden for security shifts toward the vendor as you move up the stack toward SaaS. Rather than rehash this, a great reference for understanding the shared security model can be found on the Cloud Security Alliance web site . The site explains the shifting shared model very well. The major point that needs to be emphasized is that regardless of the cloud model a consumer uses, the consumer’s data is in someone else hands, and the consumer must make sure that they understand all the risks that are part of that paradigm. Although there is a level a trust involved, stuff happens. There have been real world cloud outages that have put major B2B and B2C off line for days and even resulted in unrecoverable loss of critical data, hurting a lot of companies that used the services.
The shared security model involves greater consumer responsibility with IaaS. This leaves the security of everything except the underlying technology to the customer and the burden for security shifts toward the vendor as you move up the stack toward SaaS. Rather than rehash this, a great reference for understanding the shared security model can be found on the Cloud Security Alliance web site . The site explains the shifting shared model very well. The major point that needs to be emphasized is that regardless of the cloud model a consumer uses, the consumer’s data is in someone else hands, and the consumer must make sure that they understand all the risks that are part of that paradigm. Although there is a level a trust involved, stuff happens. There have been real world cloud outages that have put major B2B and B2C off line for days and even resulted in unrecoverable loss of critical data, hurting a lot of companies that used the services.
All organizations move a service or function to the cloud for one reason or another. It might mean moving your internal IT to Google Office, or your development efforts to a IaaS sandbox. There must be a careful analysis to ensure that your business goals and the cloud service being considered are in sync. Is what you are buying going to do what you think? Is what you are buying going to meet your availability needs? What should an organization do when they are considering a movement to the cloud?
1. Understand the definitions and the business imperatives to move to the cloud. Consider what data will move with it, and what the value of that data is.
2. Every organization must conduct a risk assessment to understand what exposure a company is willing to consider when moving to the cloud. Assume the worst. Fire, destruction, catastrophic disk failure, or unrecoverable issues. What would that mean to your business if your data in the cloud disappeared? Demand Service Level Agreements that support your uptime requirements.
3. Consider providers that can demonstrate that they can protect your data from hadware and software site failure or consider solutions to save your own data and configurations. These solutions might be options that you might have to pay for, but if they are critical, then consider it a cost of moving to the cloud. Business continuity and disaster recovery can never be assumed, it has to be a requirement, and it needs to be embodied in the service contract. Again, this might be an option you have to pay for, but ‘stuff’ does and will happen and if it does, your data could be gone.
4. Ask questions about exactly how your data is being separated from all the others. What are the physical and logical controls that stop unauthorized access to your data?
Your level of control will diminish from IaaS toward SaaS, but again, it is your data and service availability, and if it is important, then protect it with service providers that can prove they will back up your data, keep the site up and running, and keep your data private. The technologies and cloud providers have exploded in the last year with lots of players running into the space. To summarize, the cloud is very different, but the approach to adoption needs to go back to basics. Does the cloud support your business imperatives, and can a provider demonstrate that they can meet your requirements? Buyer beware? No, buyer be smart and educated.












