Olga Redmon is an attractive young professional whose resume includes experience in customer service and Microsoft Office. Her LinkedIn profile boasts 500+ connections and dozens of endorsements, all of which come from Midwestern professionals in the automotive industry. Olga’s profile picture depicts her in a tight black tank top and red lipstick.
Unfortunately for the hundreds of professionals connected to her, she isn’t real. Corresponding accounts on other networks are equally shady and incomplete, none of which have posted in months. No other information about her exists online, and the “People Also Viewed” panel contains equally suspicious profiles of scantily-clad women. But astoundingly, Olga has a considerable following in the Ohio/Michigan area, all of whom seem to believe the account is genuine. The hacker responsible could very well be distributing malicious links via direct message, or executing a comprehensive social engineering campaign targeting the auto industry.
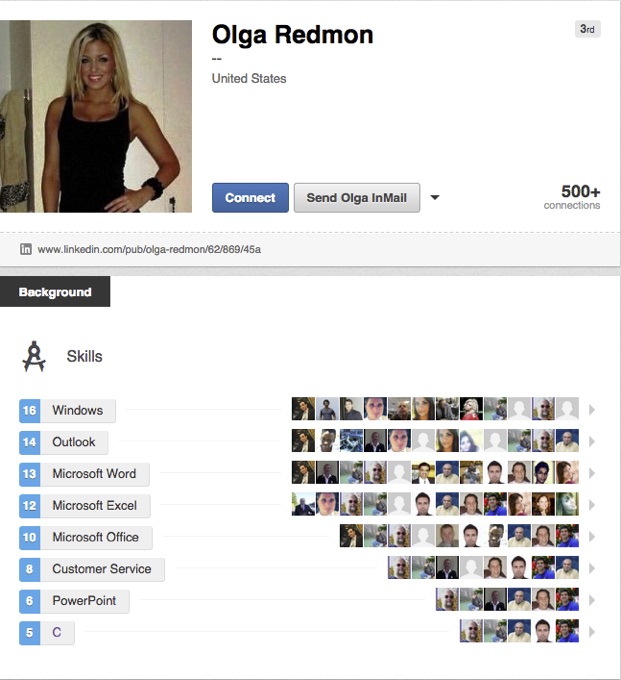
While Olga Redmond could be written off a satirical account, the amount of time and effort someone spent making it seem legitimate and connecting with such specific industry professionals suggests that this is something more sinister than satire. Olga Redmon is a well planned and executed next generation social engineering campaign. Social engineering is when a hacker creates convincing fake profiles to connect and interact with a target or group of targets. Hackers create the profiles, build up a network of connections to make them appear trustworthy, and eventually connect with their actual target. Once the request is accepted a hacker can steal information or launch a cyberattack. Instead of a promising HR, marketing, or sales lead, profiles like Olga Redmon’s can be serious cyber security threat.
Social engineering campaigns are shockingly easy to carry out. This was made clear at the RSA Europe conference last year when IT services provider World Wide Technology presented the results of a comprehensive penetration test carried out for one of their clients. The story will sound familiar – a fake account under the named Emily Williams, claiming to be an MIT grad with 10 years experience. Within days, the pen-testers received endorsements, job offers, and even a company laptop.
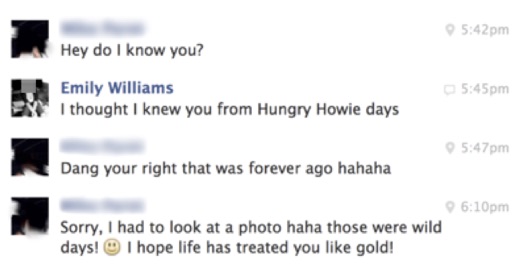
Had this been an actual attack, as a cyber criminal could have compromised an entire corporate network or brand by just creating a single fake account. From this point, the potential for attack would be nearly endless. The hacker could launch phishing and malware campaigns with increased effectiveness or begin to mine sensitive company information from unsuspecting employees.
By creating an account like Olga Redmon, no actual hacking, in the traditional sense, has been done, meaning this type of attack goes completely unaddressed by traditional security measures like anti-virus or email gateways. A tweenager with no programming experience could bypass existing security infrastructure with no more than a free afternoon and an Internet connection. Now imagine it in the hands of a skilled hacker.
In the event of a serious information breach, the CMO and the sales team will most likely not be held liable. They will always be able to point to the extensive body of research supporting social media as a robust business development tool. Social media isn’t going anywhere–the CISO need to learn how to manage the corresponding risks.
Social media is already ripe with threats, and not just Olga Redmon. Our research suggests that between 4-8% of all social media links are malicious in nature, meaning the daily number of malicious links on Twitter alone nearly exceeds the population of Spain. Expect these trends to continue.
Monitoring social media is a daunting task. It’s not a matter of logging into a company’s profiles once a day to look for suspicious activity. Employees, customers, executives, and anyone connected to your organization are the new endpoints for attack. A recent survey suggests that of the 74% of Internet users now active on social media, and the average person has 3 different social media accounts. Apply these stats to your company’s workforce and customer base – that is your full attack surface.
Social media is no longer exclusively in the realm of the marketers, and in truth, never has been. Information security professionals need to be in dialogue with all departments that leverage social media across an organization. Risk management plans need to be in place to monitor, identify, combat and remediate social media-based threats. A simple test is this – go back through your traditional information security risk management plans line by line. Ask yourself if, in all their complexity, they could prevent an attack originating from a carefully worded LinkedIn post from Olga Redmon.
The words “social media,” evoke colorful marketing infographics and peppy names like Hootsuite or Savyy or Feedly, not a massive, unchecked cyber security threat vector. CISOs need to change that, because adversaries are utilizing social media as the latest and greatest avenue for targeted attacks.















