So far on our journey through the threat intelligence mind map, we’ve gone through an overview of the many intel levels and components and we’ve drilled down into strategic cyber threat intelligence. In this article we will focus on another level of CTI – operational cyber threat intelligence.
 Operational threat intelligence is a level down from strategic CTI, and really articulates information and analysis on intelligence at the campaign level. At the operational level, adversary capabilities (in the form of tactics, techniques and procedures) as well as intentions are identified. Additionally, this is where the analysis of actor capabilities and the opportunities presented by the organization should occur. I’ve written previously about how to use intel to reduce actor opportunities and what operational CTI does is it gives you the proper context to more effectively and more quickly pivot to address critical cyber risks.
Operational threat intelligence is a level down from strategic CTI, and really articulates information and analysis on intelligence at the campaign level. At the operational level, adversary capabilities (in the form of tactics, techniques and procedures) as well as intentions are identified. Additionally, this is where the analysis of actor capabilities and the opportunities presented by the organization should occur. I’ve written previously about how to use intel to reduce actor opportunities and what operational CTI does is it gives you the proper context to more effectively and more quickly pivot to address critical cyber risks.
Make note that in the graphic above external collection is referenced. You may have noticed in my first article in this series there is a category labeled DRM or Digital Risk Monitoring. DRM is an emerging space where intelligence collection moves beyond the traditional “IT Security” aspects of CTI (in the form of IOC type data delivered via feeds) to focus on threats and exposures that materialize externally to the organization, such as a malicious actor talking about an organization in a dark web forum. I’ll dig into this category in a future article, but I bring this up to drive home an important point – in order to fully understand a threat’s avenue of approach, your collection requirements must extend beyond the traditional forms of IT security-based CTI (such as partnering with a CTI provider) to also include external DRM.
With operational cyber threat intelligence, stakeholders across the organization can understand:
• Who are the malicious actors that have the capability, motivation and opportunity to target your organization or vendors with whom you conduct business?
• What assets are those actors targeting?
• What is the business impact to the organization if they succeed?
• What are the methods they would most likely use to carry out the cyber-attack?
Malicious actors plan campaigns against targets based upon their own intel work. What information do you have that is of value to them? What is your level of presence that they can exploit? What defenses do you have in place that they need to evade? And so on. They build and expand upon their capabilities to support the successful execution of their campaign. And they shift their tactics as necessary.
By understanding malicious actors’ motivations, historical trends and current activities, you can then plan your defenses accordingly for when that threat comes your way. Think about how tough it is to defend against every possible threat out there – it’s impossible, hence the phrase that “there is no such thing as being 100% secure”. But, if you have intel on an adversary’s capabilities (i.e. their tactics, techniques and procedures (TTPs)) and their intentions, in addition to understanding your own level of presence, you know how to focus on the key areas of your defense in the pre-planning stages – before that actor is able to move forward on their intentions. This is pretty powerful, but it’s not easy to build this type of capability. It takes work in the form of a organized CTI program that includes people, process and automation.
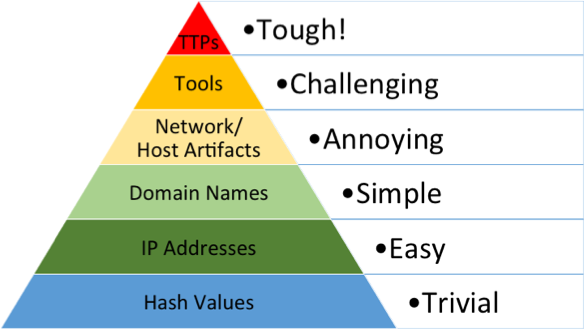 A few years back, David Bianco wrote about “The Pyramid of Pain”, which shows the relationship between the types of indicators used to detect adversarial activities and the level of corresponding pain to change their tactics (this is referenced in the CTI world quite often). Basically, the stuff at the bottom is easier for attackers to change to avoid detection and break into your network thus it is a low pain point for them to react. The higher up you go, the harder it is for actors to make such changes and you start becoming a very hard target, which obviously impacts an actor’s motivations and intentions. You become a much harder nut to crack and the actor has to decide if you are worth the effort. Remember, cybercrime is a business and time is money.
A few years back, David Bianco wrote about “The Pyramid of Pain”, which shows the relationship between the types of indicators used to detect adversarial activities and the level of corresponding pain to change their tactics (this is referenced in the CTI world quite often). Basically, the stuff at the bottom is easier for attackers to change to avoid detection and break into your network thus it is a low pain point for them to react. The higher up you go, the harder it is for actors to make such changes and you start becoming a very hard target, which obviously impacts an actor’s motivations and intentions. You become a much harder nut to crack and the actor has to decide if you are worth the effort. Remember, cybercrime is a business and time is money.
With sound and timely operational threat intelligence, you can make life a lot harder for adversaries, have a much better understanding of how your organization is positioned against today’s cyber threats and have a much clearer understanding of what you can do about it.














