WASHINGTON, DC – Kaspersky Lab researchers have uncovered yet another cyber-espionage campaign targeting unnamed “high profile” businesses and government agencies around the world, and are laying the blame at the door of a Chinese-based hacking crew.
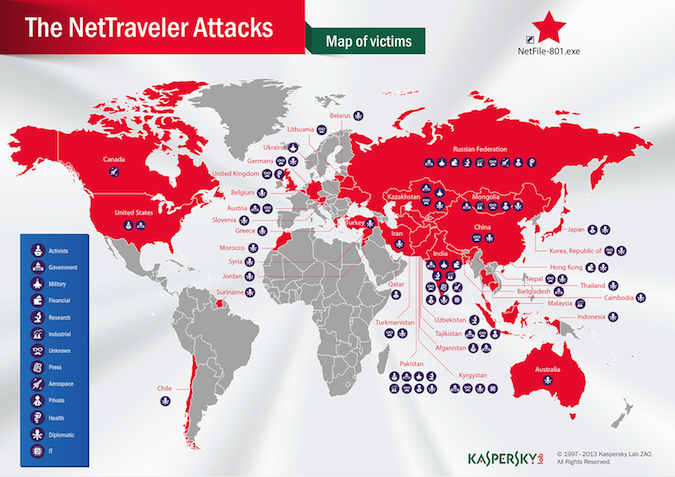
Led by a group researchers have codenamed Red Star, the campaign is focused on stealing information related to aerospace, nanotechnology, nuclear power cells, lasers, drilling, manufacturing in extreme conditions, and radio wave weapons, Costin Raiu, senior security researcher and director of the Global Research and Analysis Team at Kaspersky Lab, told attendees at the Kaspersky Lab Government Cybersecurity Forum in Washington, DC this morning. Vast amounts of sensitive data have already been compromised from over 350 organizations in over 40 countries, including the United States, United Kingdom, and Canada, Raiu said.
The attack campaign, codenamed Operation NetTraveler, relied on spear phishing to trick targeted individuals into opening a booby-trapped Word document. Once opened, the malicious code established communication with the command-and-control servers to download additional malware and transferred stolen information.
It appears the campaign was focused on cyber-espionage, not sabotage, Raiu said, noting that the malware infected both the private and public sectors, such as embassies, research centers, military contractors, oil and gas companies, and even activists.
The malicious documents targeted the CVE 2012-0158 and CVE-2010-3333 vulnerabilities, both of which have already been patched by Microsoft. These vulnerabilities are popular among various attack groups, and have been used in several recent attacks, Raiu said.
The malware had both keylogging and file transfer capabilities. It identified all the files on the infected machine that fit certain file types, such as PDFs, Excel spreadsheets, and Word documents. Attackers managed to open a backdoor in at least one victim, Raiu wrote in an analysis of the attack on SecureList.
At least six of the victims hit by NetTraveler were also previously infiltrated as part of the Red October campaign uncovered earlier this year.
Red Star appears to have been around since 2004, but has been the most active over the past three years. An analysis of the attack activity showed the group followed “military precision” starting work at 8am Beijing time and stopping at 6pm every day. The members of the group are most likely young, perhaps recent college graduates or army recruits, Raiu said.
Raiu showed an example of a job advertisement looking for individuals to work on these attacks– or “projects”– in various regions around China, including Guangdong, Beijing, and Gansu. They would be paid for every completed project, Raiu said.
Researchers also uncovered a training video sent to new NetTraveler recruits with instructions on how to craft a cyber-attack. The recruits were provided with an exploit builder, Trojans, and a list of targets and told to craft malicious Word documents to launch the attack. If even one target is compromised, the attacker is paid.
The video highlighted that the people carrying out the actual attacks weren’t all that sophisticated.
“They’re using people with not-so-high knowledge who are just following instructions,” Raiu said.
Raiu said researchers found hints linking Red Star to another hacking group with the same name known to have over 80 thousand members. Kaspersky Lab is not sure yet if there is a relationship between these two groups.
There is a common misperception that all these cyber-espionage campaigns are disconnected and operate independently, Raiu said. In reality, all these groups are interconnected.
“There is just one big ugly gorilla with a thousand heads, and we haven’t seen them all yet,” Raiu said.














