During the three months from mid-May to mid-August 2021, researchers detected a 300% increase in phishing URLs within their own telemetry targeting Chase Bank. Chase was the sixth most targeted brand, behind obvious companies as PayPal, Apple, and Facebook.
During this period, researchers from Cyren – a cloud-based threat intelligence and SaaS company – detected a notable increase in phishing kits designed to mimic the Chase banking portal. Of all the phishing kits collected by Cyren over the last six months, Chase is a close second to only Office 365, and well ahead of Microsoft and PayPal.
Phishing kits can be purchased from the internet and used by anyone. Typically, they provide the phishing URL complete with the code necessary to steal the victim’s details, leaving the buyer to compose and send the phishing email. Ready-made phishing messages can also be purchased, and email addresses of actual or potential Chase customers can be bought separately.
“Many of the phishing kits analyzed since May 2021 are highly sophisticated and built to harvest more than just the victim’s email address and password,” say the researchers in their report. “The kits collect banking and credit card information, social security numbers, home addresses, and other very sensitive information. Some of the kits are designed to capture the one-time use codes used for two-factor authentication.”
Chief among the current kits in use is the Chase XBALTI. XBALTI has been around for several years, but is currently primarily used against Chase and Amazon.
Smishing (phishing by phone text messages) is particularly popular. Short messages that do not necessarily obey standard grammar are expected by the target, and it is harder to detect disguised URLs. Email messages are longer and more easily expose the poor grammar and typos that often expose malicious emails.
The purpose, as with all phishing, is to lure the target into clicking a link that will lead to the phishing URL. In an XBALTI example analyzed by Cyren, the malicious link leads to a page looking very similar to the genuine Chase site, but hosted on a compromised Brazilian website. A series of separate data entry forms are used to harvest the victim’s credentials.
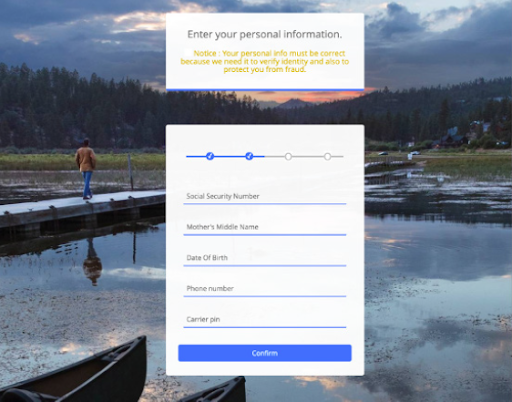
The first asks the user to enter his or her username and password. The second asks for the victim’s email address and password. The third says that the credentials are incorrect and asks for them to be re-entered – presumably just in case the victim did make an error.
The fourth page asks for more detailed information that can be used for identity theft, including a social security number, mother’s middle name, date of birth, and more.
The fifth collects credit card information, and the sixth asks for information on another credit/debit card. The victim is then asked to provide a home address before finally verifying the details. After this, the victim is redirected to the official Chase website, probably without realizing that his full Chase identity has just been stolen.
As each form is completed, XBALTI emails the details to the attacker, using an email address configured within the phishing kit, in the file Email.php. The full details are also collated and stored as HTML within a hidden but open file on the compromised website. From such files, the phishing kit provider can collect multiple details comprising all the stolen data from all the phishers using the kit across multiple phishing sites. “Complete and verified packages of identity information sell for a premium on dark web marketplaces and criminal networks,” note the researchers.
The phishing kits use evasion tactics to avoid detection – such as free dynamic domain name services like Duck DNS to point an URL to the server of their choice. Most employ user-agent blockers to stop crawlers accessing the site, while others use a combination of user-agent, IP host lookup and ISP blocking.
Phishing, especially financial fraud phishing, is popular among criminals because it works. “Phishing kits are built once, sold many times, and deployed onto thousands of active web servers each day,” say the researchers. The stolen data is used rapidly to commit bank fraud, and then the complete data is bundled and sold on the dark web for potential future full identity theft.
“Whether it’s the financial analyst that wires tens of thousands of dollars to fraudsters, the executive that exposes login credentials, or just the bank customer juggling remote work life, everyone is vulnerable to attack,” say the researchers.
Related: Microsoft: Ongoing, Expanding Campaign Bypassing Phishing Protections
Related: Coinbase Users Face Ongoing Phishing Attacks
Related: Evasive Malware Now a Commodity
Related: JPMorgan Chase Bank Notifies Customers of Data Exposure









