Japanese video game giant Capcom this week confirmed that a large amount of data was stolen from its systems during a ransomware attack several weeks ago.
Best known for multi-million-selling game franchises such as Ace Attorney, Devil May Cry, Resident Evil, and Street Fighter, Capcom has subsidiaries in Asia, Europe, and North America.
In early November, Capcom announced that it was forced to suspend some operations due to unauthorized access to its internal network and that email and file servers were affected.
The Ragnar Locker ransomware gang, which was responsible for the attack, claimed at the time that it managed to steal vast troves of data from Capcom, including bank statements, financial documents, intellectual property, personal information of both customers and employees, emails and private chats, and other data.
On Monday, Capcom revealed that its investigation into the incident has indeed confirmed that data was stolen during the ransomware attack, including personal information of current and former employees, sales reports, and financial information.
The stolen data, the company says, includes names and signatures, addresses, passport information, and human resources information.
According to the game maker, a large amount of other information might have been stolen as well, including help desk information (Japan), store member and esports operations website member information (North America), a list of shareholders, and former employee and applicant data.
The potentially affected information includes names, addresses, emails, phone numbers, photos, birthdates, shareholder numbers, and amount of shareholdings. More than 350,000 people could be affected, Capcom revealed.
Additionally, the game maker says confidential corporate data — including partner information, sales data and documents, development documents, and more — might have been compromised as well.
“None of the at-risk data contains credit card information. All online transactions etc. are handled by a third-party service provider, and as such Capcom does not maintain any such information internally,” the company says.
Capcom also noted that it could not determine the exact number of impacted people or the amount of stolen data, so it decided to list the “maximum number of items it has determined to potentially have been affected at the present time.”
While the investigation continues, the video game giant is in the process of informing affected people of the incident.
The company also confirmed that the attack, which was identified on November 2, was indeed the work of the Ragnar Locker gang, and revealed that some of the actions it took following the discovery include shutting down the infected systems, contacting the authorities, strengthening its security posture, and engaging with a third-party security company to investigate the incident.
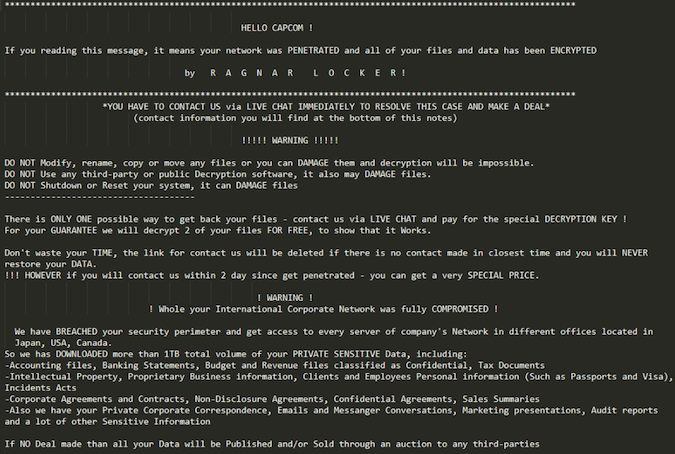
“Investigation and analysis, etc., of this incident took additional time due to issues such as the information saved on servers being encrypted and access logs being deleted in the attack,” the company also explains.
Capcom also noted that this was a targeted attack and that the employed ransomware appears to have been specifically tailored to encrypt data on its systems and delete access logs. Additional information will be revealed as the investigation advances.
“While it’s good that no payment information was taken in this breach, the amount of personal data stolen amounts to something worse. A stolen credit card can be stopped and payments refused, but we only get one identity – if the digital version is stolen in a breach, then that is much harder to replace. Capcom needs to contact affected members immediately and should be providing information on the steps they are taking to provide identity protection, as well as what members can do to protect themselves,” Laurence Pitt, Technical Security Lead, Juniper Networks, said in an emailed comment.
Related: Hackers Demand $11 Million From Capcom After Ransomware Attack
Related: Biotech Company Miltenyi Biotec Discloses Malware Attack
Related: Carnival Corp. Confirms Personal Information Compromised in Ransomware Incident













