Can you survive a massive Cyber-Attack? Is your organization prepared?
Early in 2010, Dennis Blair, the Director of the US National Intelligence Agency told members of the House Intelligence Committee that the United States is at risk of a crippling cyber attack that could “wreak havoc” on the country because the “technological balance” is tilted in a way that it “favors those who want to use the Internet for malicious purposes.” The Canadian Security Intelligence Service has warned that “compromises” of the computer networks of the government, universities, private companies and individual networks in Canada have “increased substantially.” Other experts have opined that the threat of an all out cyber-war is real.
Are these claims exaggerated? Could the DNS survive a massive cyber-attack? And how best should the DNS industry – and your organization – reduce the risks of suffering from a significant outage?
Earlier this year there was a call for the creation of a DNS Computer Emergency Response Team (or DNS-CERT) along the same lines as other CERTs in existence today. The original CERT Coordination Center, hosted at Carnegie Mellon University, was created in response to the Morris worm all the way back in 1988, before the Web, as we know it, even existed. Many governments now host CERTs. For example, the US government, created US-CERT in 2003 under the umbrella of the newly formed Department of Homeland Security, to coordinate responses to attacks on government networks. The private sector collaborated to setup the DNS Operations, Analysis and Research Center, DNS-OARC, created to allow companies and organizations to share data and arrive at better solutions about how to secure the DNS. The DNS-OARC is great for post-attack analysis and the sharing of preventative best practices, but it does not currently enable the coordination of incident response during incidents.
In this connected world, a good defense against attacks begins with concerted coordination among cooperating entities. For example, when the Conficker worm struck in 2008, domain name registries from dozens of countries had to work together, along with Microsoft and other security organizations, in order to slow the creation of an enormous botnet. A short time later, the Kaminsky bug forced dozens of vendors, researchers, registries and backbone providers to cooperate to fix a fundamental flaw in the DNS that allowed cache poisoning and spurred the deployment of DNSSEC (Domain Name System Security Extensions). Effective solutions in both cases were made possible only because of voluntary cooperation among organizations with a stake in Internet infrastructure security.
Nowadays, when most people speak of “cyber attacks,” they are really referring to Distributed Denial of Service attacks. DDoS has been a plague on the DNS industry, and others, for many years. Although reported attacks rarely cause significant issues for the average Web user, they can sometimes result in hours of downtime for service providers and their customers.
As the amount of bandwidth available to residential Internet subscribers increases and attackers become more adept at turning these endpoints into bots, DDoS attacks are multiplying in size. Publicly reported attacks have peaked at almost 50 Gbps, which is far beyond the capacity of the vast majority of Internet sites, and even some service providers.
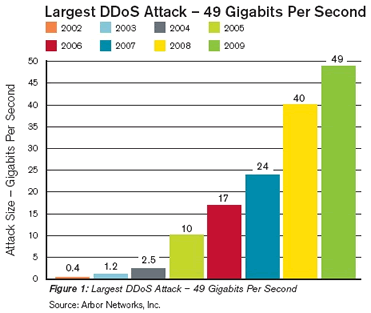
It’s hardly surprising that research from Arbor Networks shows that DDoS is the biggest security concern among enterprises. However, even these attacks rarely cause outages of more than an hour or two, as the victim and its providers work together to block or throttle the malicious traffic.
It’s widely acknowledged that one of the best ways to mitigate the effects of a large DDoS attack is through the use of IP Anycast, an Internet standard that enables the global mirroring of critical resources. When DNS networks use Anycast, identical name servers advertise the same IP address from multiple, strategically distributed locations, enabling the efficient local resolution of domain names. This can also help during DDoS attacks, by spreading the unwanted load between multiple sites based on network topography. Depending on the distribution of sources used in the attack, this can mean that the effects of the DDoS are felt by users in certain geographic areas but not others.
Anycast has been in heavy use at most of the DNS root servers and many of the top-level domain zones for several years. Indeed, Anycast has been instrumental in fighting off the largest DDoS attacks that perpetrated to date. In this regard, based on historical evidence, the DNS has already proved its resilience – the DNS will likely survive a massive cyber attack. But, will you? If your organization is not utilizing Anycast, or has not contracted with a managed DNS service provider to provide Anycast, or has not adopted any of a set of protective measures, you may be vulnerable at a time when you can hardly afford to be.
The fact is that organizations have to spend more and work harder than attackers do, and the balance is tilted more and more every day in favor of the attackers. Whether it’s defending DDoS attacks or fighting global botnets, success is determined by the level of cooperation among the commercial and non-commercial resources that administer the critical resources on the Internet. Cooperation, preparedness, budgeting and planning are all essential components of the coming battle for your organization’s network, and that of the Domain Name System.
DNS system operators report they are ready to face the challenge. Are you?













