A researcher says BMW was informed of the mobile app vulnerability that allows hackers to locate and unlock cars months before the attack method was disclosed.
At the recent DEF CON conference in Las Vegas, security researcher Samy Kamkar showcased a $100 gadget that allowed him to intercept the login credentials of General Motors car owners who used the company’s OnStar RemoteLink iOS app.
GM’s OnStar service allows users to locate, unlock and even start their car from a smartphone app. However, Kamkar discovered that the iOS application fails to validate SSL certificates, exposing users to man-in-the-middle (MitM) attacks.
Kamkar’s gadget, dubbed OwnStar, is designed to impersonate a familiar Wi-Fi hotspot in order to trick the potential victim’s phone into connecting to it — AT&T phones for example will automatically connect to networks named “attwifi.” Once the target’s phone has connected to OwnStar, the device can leverage the SSL vulnerability to capture the target’s OnStar credentials when they use the RemoteLink app.
Once they obtain the credentials, hackers can log into the victim’s account and perform various actions, including locating the car, unlocking it, and starting the engine. An attacker would still need a key to drive off, but Kamkar believes this is still a serious issue.
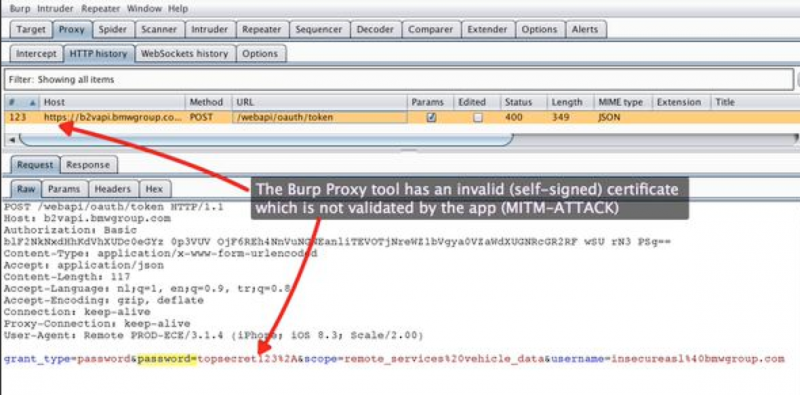
GM updated its iOS app to address the vulnerability, but Kamkar discovered that the iOS applications offered by Mercedes (mbrace), BMW (My BMW Remote) and Chrysler (Uconnect) were affected by the same type of SSL issue.
Kamkar reported his findings to the car manufacturers, but BMW appears to have known about the vulnerability for months before the researcher disclosed his findings.
Han Sahin, co-founder of Netherlands-based security firm Securify, said he reported the MitM SSL vulnerability to the BMW Group on April 22. The car maker’s CISO confirmed receiving the bug report the next day, but the My BMW Remote app for iOS is still vulnerable.
“Securify has reported identical issues in the past to various organizations; ranging from small organizations to enterprises. Most organizations take these issues seriously and update their apps in a timely fashion. In our opinion, three months should be enough to resolve issues like this,” Sahin told SecurityWeek.
“At the time of writing the BMW iOS app is still vulnerable to man in the middle attacks. We’ve informed BMW more than 120 days ago. We have yet to receive a formal response from BMW,” the expert added. “We think BMW has had enough time to resolve this issue. Had they done so, they would not have been affected by the OwnStar attack.”
BMW has not provided a statement to SecurityWeek by the time of publication. However, in a statement sent to Wired on August 15, the company said its apps “conform to the same industry standards as other apps that use SSL-encrypted communication with a backend, such as online banking apps.” The company also noted that “a man-in-the-middle attack on client-server communication can never be completely ruled out, but is virtually impossible to carry out and the probability of such a specific attack in everyday life is highly unlikely.”
Many mobile app developers don’t seem to be concerned about the fact that they expose users to MitM attacks. The CERT Coordination Center at Carnegie Mellon University (CERT/CC) conducted an analysis of Android applications last year and discovered that thousands of apps fail to properly validate SSL certificates.
As far as car hacking is concerned, several researchers demonstrated this summer that the IT systems in modern cars are plagued by serious vulnerabilities. Experts hacked a Jeep, a Corvette, and even a Tesla Model S.
Related Reading: Industry Reactions to Remote Car Hacking
Related Reading: Researchers Hack Car via Insurance Dongle
Related Reading: Tesla Increases Bug Bounty Payout After Experts Hack Model S














