Organizations are getting better at detecting breaches, but the positive trend observed last year has been attributed by experts not only to improved cybersecurity capabilities, but also an increase in the number of attacks that are quickly detected by victims.
According to FireEye’s 2019 M-Trends Report, the median dwell time for breaches detected internally decreased from 57.5 days in 2017 to 50.5 days in 2018. Overall, when taking into consideration both internally and externally detected attacks, the median dwell time dropped to 78 days in 2018, from 101 days in the previous year and 416 days back in 2011.
FireEye describes the dwell time as the number of days an attacker is present on the victim’s network before their activity is detected.
This improvement has been partly attributed to organizations having better internal threat hunting capabilities and enhanced network, endpoint and cloud visibility. However, the smaller dwell time is also the result of an increase in attacks that are not meant to be stealthy. For example, in the case of ransomware attacks, the victim learns quickly that they have been hit as the attacker delivers a ransom note. Business email compromise (BEC) attacks are also often detected quickly as it typically does not take long for victims to realize that they have been targeted by fraudsters.
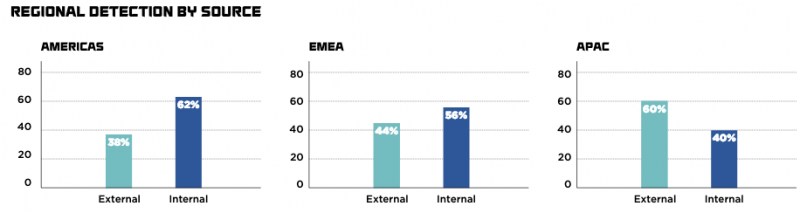
FireEye says nearly 60% of the breaches it investigated in 2018 were detected internally, but that is slightly less than the 62% in the previous year.
The security firm also found that it’s increasingly common for breached organizations to be re-targeted by either the same attack group or a similarly motivated threat actor. In last year’s report, the company revealed that 56% of its customers had been re-targeted and in the latest report the percentage has climbed to 64%. Sectors such as finance, education and health were the most re-targeted.
FireEye initially tracks threat actors as TEMP groups and when researchers believe that a group is sufficiently mature, the company assigns them an APT or FIN number – APT is for state-sponsored groups and FIN is for highly organized criminals groups.
Last year, FireEye assigned APT numbers to four groups: two linked to North Korea (APT37 and APT38), one linked to Iran (APT39), and one tied to China (APT40).
While it’s not uncommon for cybersecurity firms to attribute attacks to a certain government, FireEye pointed out that 2018 saw a significant increase in public attribution by governments, including indictments aimed at people believed to be responsible. For example, countries such as the US, UK and Australia have officially blamed the WannaCry attack on North Korea, and attributed the NotPetya attack to Russia. North Korean, Chinese and Russian nationals have been indicted in the U.S. over their roles in major attacks.
The complete 2019 M-Trends Report from FireEye is available in PDF format.
Related: Financial Attackers as Sophisticated as Nation-State Groups
Related: Organizations Still Slow to Detect Breaches, Says CrowdStrike













