Researchers Find Vulnerabilities in Belkin WeMo Home Automation Products
Researchers from Invincea have identified serious vulnerabilities in Belkin WeMo home automation devices and their associated Android application. The vendor has fixed the mobile app and will soon release firmware updates to patch the device flaws.
Belkin WeMo products are designed to allow users to control their home electronics from anywhere. The product line includes smart switches, cameras, coffeemakers, lightbulbs, humidifiers, heaters and even slow cookers.
Researchers disclosed several serious vulnerabilities in this Belkin product line back in 2013 and 2014. Due to the popularity and significant market share of these devices, Invincea Labs researchers Scott Tenaglia and Joe Tanen decided to take another look at WeMo products and discovered two serious flaws that can be exploited for various types of malicious activities.
One of the issues found by Tenaglia and Tanen can be exploited to remotely gain root access to a WeMo gadget. When users program these Internet of Things (IoT) devices — for example, setting a switch to turn off at a specified hour, or changing a slow cooker’s heat setting after a certain time — they actually create a set of rules. These rules, created and managed via the WeMo Android application, are stored in a SQLite database that is uploaded to the device. The device unpacks the file, pulls the rule information via SQL queries, and updates the rules stored in its memory.
The problem is that the value of a column in the rule database is not sanitized, allowing an attacker to insert a specially crafted value. According to Invincea, an attacker who has access to a WeMo user’s smartphone can send the vulnerable device a specially crafted database file that creates and executes a root shell. This allows the hacker to execute arbitrary commands with root privileges, and potentially install IoT malware that results in the device becoming part of a botnet, such as the notorious Mirai botnet.
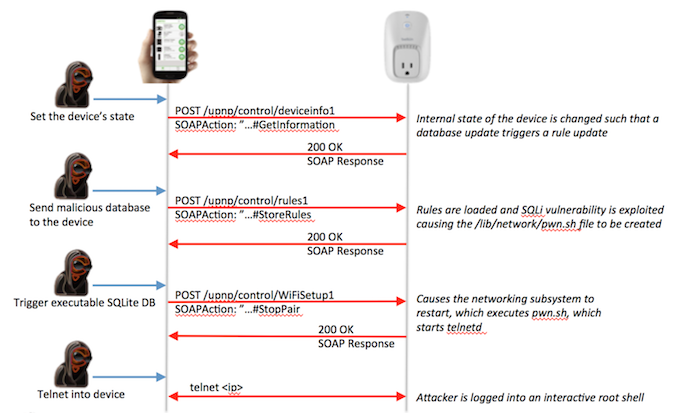
Interestingly, once the attacker gains root access to the WeMo device, they actually have more privileges than a legitimate user. The only way for the user to remove the malware is through a firmware update from the vendor, but experts warned that the attacker can easily break the firmware update process and prevent the victim from regaining access to their device.
The second vulnerability found by Invincea researchers, the one affecting the WeMo Android app, is a cross-site scripting (XSS) issue. An attacker who has network access to a vulnerable WeMo device can execute arbitrary JavaScript code in the context of the Android application.
When the WeMo app is executed, it attempts to discover and identify all WeMo devices in range. Researchers discovered that an attacker can replace the device’s friendly name with JavaScript code, which gets executed on the phone or tablet when the name is fetched by the Android app.
Experts demonstrated an attack by injecting JavaScript code that replaces the app’s interface with content obtained from a specified IP address. The WeMo app can access location, file storage, camera, Wi-Fi connection, contacts, user accounts and phone capabilities, allowing an attacker to conduct a wide range of malicious activities.
A proof-of-concept (PoC) released by Invincea shows how a hacker can download all the pictures on a phone and track the device’s location. Experts pointed out that a network attacker can easily change the device’s friendly name, without the need to root it, simply by sending it a UPnP message.
“To the best of our knowledge, using an IoT device to compromise a smartphone is a nuance of IoT security that hasn’t been explored prior to our research. It brings to light the larger issue of the second and third order effects of IoT insecurity,” the researchers said.
In an attack scenario described by Tenaglia for SecurityWeek, the attacker emulates a WeMo device with a specially crafted name and follows the victim to a coffee shop. When they both connect to the same Wi-Fi, the WeMo app automatically queries the network for WeMo gadgets, and when it finds the malicious device set up by the attacker, the code inserted into the name field is executed on the victim’s smartphone.
Tenaglia said the vulnerabilities were reported to Belkin on August 11 and the vendor confirmed them on the same day. The WeMo Android app was patched in August with the release of version 1.15.2. The SQL injection vulnerability should be resolved in firmware updates 10884 and 10885, which Belkin plans on releasing this week.
In addition to disclosing these vulnerabilities, Invincea discovered a hardware authentication bypass technique. Experts believe this and the method used to exploit the SQL injection flaw for arbitrary code execution could apply to other products as well.














