Amazon announced this week that a new feature designed to prevent data leaks has been added to Amazon Web Services (AWS).
Improperly configured Simple Storage Service (S3) buckets can expose an organization’s sensitive files, as demonstrated by several incidents involving companies such as Viacom, Verizon, Accenture, Booz Allen Hamilton, and Dow Jones.
As a result of numerous incidents, AWS last year introduced a new feature that alerts users of publicly accessible buckets, but researchers have still found data leaks resulting from misconfigured buckets.
AWS’s latest attempt to prevent leaks is called Amazon S3 Block Public Access, which should provide an additional layer of protection for both an entire account and individual buckets.
Users can leverage Access Control Lists (ACLs) and bucket policies to specify who should be granted access. They can give access to specified accounts or IP addresses, or require the use of multi-factor authentication. However, there is still a chance that users may unintentionally grant public access to their buckets.
Amazon S3 Block Public Access aims to address this by providing settings for blocking existing public access and ensuring that public access is not granted to new items.
“If an AWS account is used to host a data lake or another business application, blocking public access will serve as an account-level guard against accidental public exposure. Our goal is to make clear that public access is to be used for web hosting!” said Jeff Barr, Chief Evangelist for AWS.
The new settings can be accessed from the S3 console, the command-line interface (CLI) or the S3 APIs, and they allow users to manage public ACLs and public bucket policies.
The user can disallow the use of new public bucket or object ACLs (without affecting existing items), or remove public access granted through public ACLs. They can also block new public bucket policies (without impacting existing items), or block public and cross-account access to buckets with public policies.
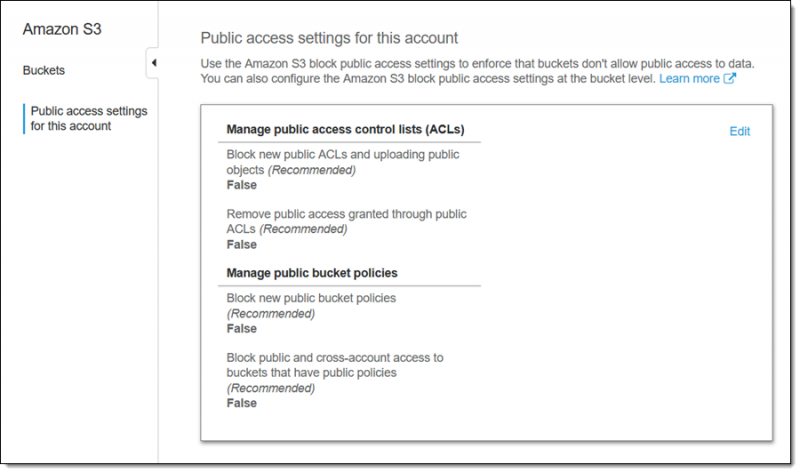
These settings can be applied to the entire account or to individual buckets. Each time a change is made, the user needs to provide confirmation by typing “confirm” into a text field and clicking a “Confirm” button.
The new feature is free and immediately available in all commercial AWS regions. Amazon has advised users to start using it to prevent data leaks.
Related: Amazon S3 Bucket Exposed GoDaddy Server Information
Related: AWS S3 Buckets at Risk of “GhostWriter” MiTM Attack

















