Distributed denial-of-service (DDoS) attacks launched in recent days against popular flight tracking services may be linked to the conflict between Armenia and Azerbaijan.
UK-based live flight tracking service Plane Finder, which is used by millions of people, informed users on Tuesday via Twitter that its services were disrupted by a cyberattack. The disruption appears to have lasted at least 10 hours.
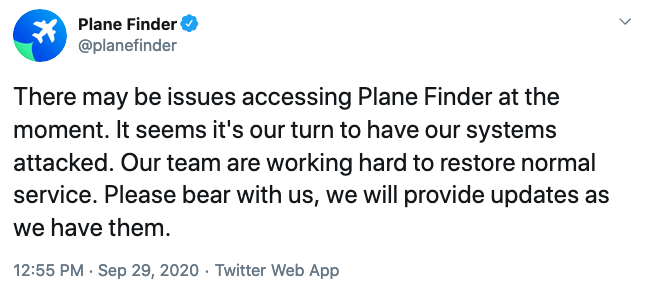
The even more popular Flightradar24, a Sweden-based company that claims to have over 2 million users per day, started experiencing problems even earlier, and on Monday it reported being under attack for the third time in two days. The company said that while its services were disrupted, it found no evidence of user information being compromised.
FlightAware has also reported service disruptions at around the same time as Flightradar24 and Plane Finder, but it did not say whether they were caused by an attack.
Several individuals believe the DDoS attack may be related to the fight between Armenia and Azerbaijan over the disputed Nagorno-Karabakh region. This is a decades-long conflict, but BBC described the recent events as “the most serious escalation in recent years.”
Turkey has been helping Azerbaijan, reportedly sending drones and fighter jets, and the DDoS attacks may have been launched in an effort to hide the movement of the aircraft.
There are also some unconfirmed reports that the Turkish Cyber Army, a pro-Turkey hacktivist collective, is behind the DDoS attacks on the flight tracking services. The same group has also allegedly taken responsibility for a Google Earth feature outage, but it’s not uncommon for these types of hackers to falsely claim responsibility for technical issues experienced by high-profile organizations.
SecurityWeek has reached out to Google for clarifications and will update this article if the company responds.
Related: Akamai, Amazon Mitigate Massive DDoS Attacks
Related: DDoS Extorters Claim to Be Armada Collective, Fancy Bear
Related: BIG-IP Vulnerability Exploited to Deliver DDoS Malware













