The advanced persistent threat (APT) actor behind the recent attacks targeting Ukraine has started delivering BlackEnergy malware using specially crafted Word documents with embedded macros.
BlackEnergy malware, which is leveraged by one or multiple groups, has become increasingly sophisticated and its operators have been using it to target energy and ICS/SCADA companies from across the world. A recent campaign involving BlackEnergy malware has been seen targeting Ukraine’s critical infrastructure.
A coordinated attack launched against the country’s energy sector in December resulted in power outages in the Ivano-Frankivsk region. Investigators found BlackEnergy malware on infected systems, along with a destructive plugin known as KillDisk that is designed to delete data and make systems inoperable. However, experts believe the malware is not directly responsible for the outages, and instead it only helped attackers cover their tracks and make it more difficult to restore service.
Ukrainian security firm Cys Centrum reported last year that the attackers had leveraged PowerPoint presentations to deliver the malware. In mid-2015, threat actors started using specially crafted Excel spreadsheets with embedded macros to drop the Trojan onto targeted systems.
Kaspersky Lab reported on Thursday that attackers recently started attaching malicious Microsoft Word documents to their spear phishing emails. ICS-CERT, which has been assisting CERT Ukraine in investigating the recent attacks, has confirmed the use of malicious Word documents.
A document sample was uploaded to an online scanner service on January 20 and a relatively low number of security products flagged it as a threat. The document in question referenced Ukrainian far-right nationalist political party Right Sector (Pravyi Sektor).
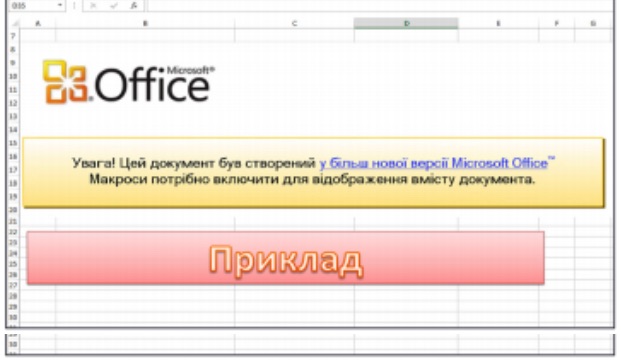
When the document is opened, the user is warned that macros have been disabled for security reasons. The malicious macro can only be executed if the victim clicks the “Enable Content” button in the document.
Microsoft disabled macros by default several years ago specifically because malicious actors started abusing the feature to deliver malware. However, threat actors have not given up on the technique and in many cases they’ve tricked users into enabling the feature by claiming that it’s needed to view content.
If macros are enabled, an executable file named “vba_macro.exe” is created and written to the disk. This executable is a BlackEnergy dropper designed to drop and run the final payload, Kaspersky said.
Security firm SentinelOne published a report on Wednesday detailing the use of Microsoft Office documents and macros in BlackEnergy attacks. The company concluded that internal actors might have helped BlackEnergy attackers, especially in operations aimed at SCADA systems.
SentinelOne, whose research focused on Excel spreadsheets, pointed out that macros embedded in documents can be executed either by getting the user to enable macros or by leveraging an Object Linking and Embedding (OLE) vulnerability in Office (CVE-2014-4114) that was patched by Microsoft in October 2014.
“The only two options then to carry out the attack is – target a victim’s machine that was not patched, or get an internal employee to either accidentally or deliberately execute the infected Excel documents causing the malware to propagate inside the network. At this point it would be highly unlikely that organizations have not deployed the patch against CVE-2014-4114, thus the most likely conclusion is use of an internal actor,” SentinelOne said in its report.
Udi Shamir, Chief Security Officer at SentinelOne told SecurityWeek that a new attack targeting a Ukranian power facility was just detected on Tuesday, but was unable to provide specific details, other than saying the attack vector appears to the be the same variant analyzed in this report.
















