2FA Systems Used by Banks Bypassed with Malware, Rogue Mobile Apps
SMS-based two-factor authentication (2FA) mechanisms used by banks to secure their customers’ accounts have been bypassed by cybercriminals using a combination of malware, mobile apps, rogue DNS servers, and phishing sites, according to a report published by Trend Micro on Tuesday.
The security firm has been monitoring a campaign which it has dubbed “Operation Emmental,” because similar to the Swiss Emmental cheese, the security systems used by financial institutions can be full of holes. The individuals behind this operation have been trying to gain access to the accounts of users in Switzerland, Austria, Japan and Sweden by obtaining the security tokens sent by banks to customers’ mobile devices via SMS.
Trend Micro says the attack starts with a fake email that purports to come from a well known company. These messages carry what appears to be a harmless document, which is actually a Control Panel (.cpl) file that’s designed to infect the targeted computer with malware through a bogus Windows update tool.
Once it infects a computer, the malware enables the attackers to redirect victims to arbitrary domains by changing the device’s Domain Name System (DNS) settings. Whenever users try to access certain bank websites, they are redirected via a rogue DNS resolver server to a phishing page set up for one of the 34 targeted banks, six of which are in Austria, five in Japan, 16 in Switzerland, and seven in Sweden.
In order to make these phishing pages look legitimate, the malware installs a new root Secure Sockets Layer (SSL) certificate which prevents Web browser from warning victims when they’re directed to these websites. On the phishing pages, users are asked to enter their username, bank account number, PIN, and other data that’s necessary for the first phase of the authentication process, Trend Micro said.
However, this information is not enough to access a victim’s account because of the two-factor authentication mechanisms used by many banks. In order to gain access to the session tokens sent by the banks to customers via SMS, the attackers instruct users to install an Android application that includes the logo of the financial institution to avoid raising suspicion. This mobile application appears to generate a password which must be entered on the website to continue the authentication process, but in reality it’s just a trick to get people to install the app on their phones. To ensure that the app would not be removed, victims are told that they must leave it on their
mobile devices if they want to be able to perform online banking operations in the future.
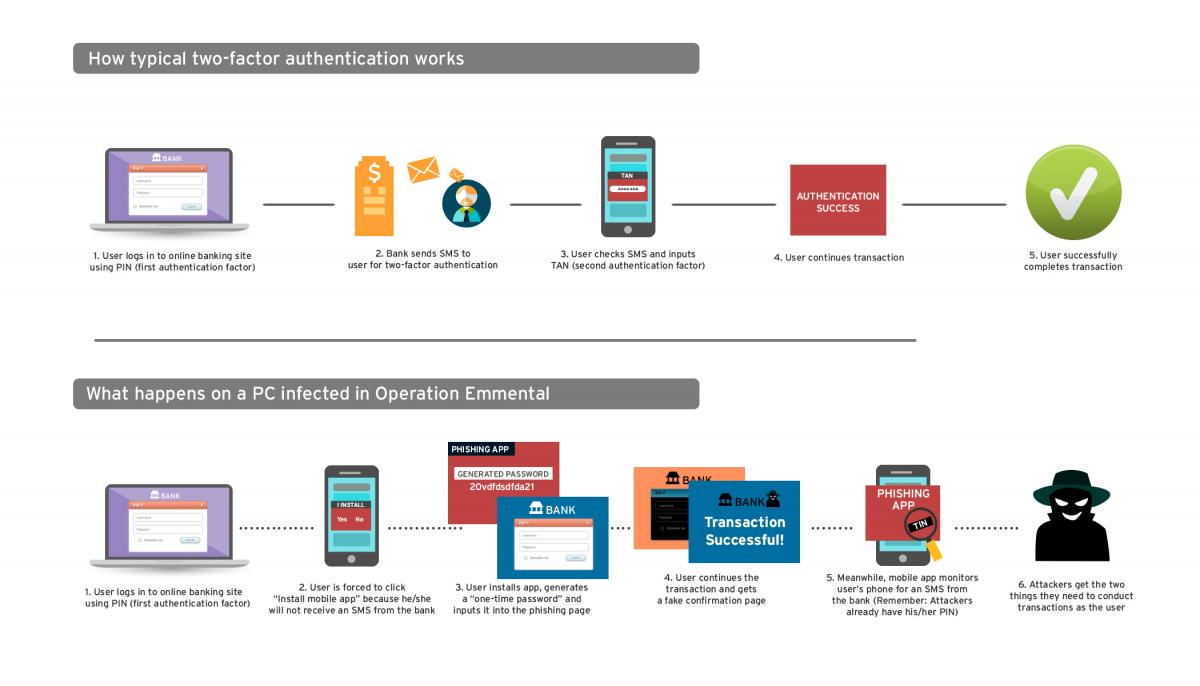 Figure 1. What happens in the 2-factor authentication process when the PC is infected in Operation Emmental [Image Credit: Trend Micro]
Figure 1. What happens in the 2-factor authentication process when the PC is infected in Operation Emmental [Image Credit: Trend Micro]
The real role of this app is to intercept the session tokens sent by banks via SMS and forward them to a compromised machine which the attackers use as a command and control (C&C) server. At this point, the cybercriminals already have the information they need for the first phase of the authentication process, and when victims visit the genuine bank website and they attempt to log in to their accounts, the cybercriminals are provided with the session token, the last piece of information they need.
Trend Micro also pointed out that the Windows malware deletes itself from the computer once it completes its task, most likely to help the attackers keep a low profile.
While it’s usually difficult to track down the actors behind such campaigns, the security company has found evidence indicating that Russian-speaking individuals are responsible.
Tom Kellermann, Trend Micro Chief Cybersecurity Officer, said the security firm managed to identify the location of the malware owners based on connection logs from underground sources.
“It turns out that most of them were from Romania,” Kellermann told SecurityWeek. “This made us think that one of the associates in this cybercriminal enterprise is based in that country. A Russian speaker based in Romania could be responsible for the whole operation.”
“The key point here is that the modern day ‘Peterman’ safe crackers are all Eastern European and the arms bazaar of Easter Europe is responsible for the development and sale of safe cracking tools,” he added. “This new crime kit represents an escalation of a capabilities which will endow the modern day Dillinger gangs a bountiful summer.”
The complete paper on the Emmental campaign is available online.















