What Happened to the Apocalypse?
Are you surprised that we are still here? Well, most of us.
Wait a minute – the Mayan Apocalypse was a myth? Since I am a security geek, I just happen to talk about security a lot. What are some security myths I have heard in my conversations with some very bright people?
1. Passwords don’t work.
Well, they don’t. And they do. It depends as much on what you use them for as how you use them. Maybe it is more correct to say “bad passwords don’t work”. But even a bad password can be better than no password in the right situation.
The catch is using good passwords and following all those other password rules. Password rules like composition and re-use exist for a reason. If, for instance, your password is something like qwer1234, or you are using the same “cool” password on all of your social media and banking sites – let’s just say I find myself unwilling to reinforce such behavior. But, if you have a good password, it can work wonders at keeping out the riff-raff. A good password can help throttle access to your system and/or your data, but there are often ways around passwords, or ways to simply make them irrelevant.
Unfortunately, some people use bad passwords and think that makes them secure. If you are relying on a password to keep your financial, sensitive, or classified information from a determined, professional attacker, you are probably not really thinking that through. Now, if that password is something like “qwer1234”, I have an offer for you from a Nigerian Prince that you might find interesting.
If you are relying on a good password (at least a decent one) to stop casual access, inexperienced attackers, and protect general privacy, you probably have the right mindset. A good password can help protect your system and data, which is the important part of information security.
2. I have my anti-virus up-to-date, so I am safe.
Heh. Where do I start? Anti-virus is one tool that helps shrink the size and number of threats to which you are vulnerable. Unfortunately, it is not a perfect solution, or not, it turns out, necessarily even a great one.
A recent Threat Report summarized the virus testing done by members of Solutionary’s Security Engineering Research Team (SERT). They tested and analyzed many different viruses, with several different anti-virus toolkits. Their results indicated that only 46% of the malware samples analyzed were detected by common anti-virus software. And, not all of those anti-virus tools even did the best job of actually removing all the viruses that they detected.
Yeah, that was less than half.
The real problem is that the real-world is brimming with viruses and other forms of malware. Some of it is bulk tripe that is the same stuff we have seen for years – just a redistribution or repackaging of old stuff. Any decent anti-virus can see and remove it. In that case, a good anti-malware solution is invaluable. But some of the malware is really good, uses great stealth techniques, is just plain hard to see, and can be even harder to remove.
Would you count on a parachute that only opened 46% of the time? Probably not.
And, chances are that “having your computer compromised” is probably not quite as bad as that squishy noise you will make if your parachute does not open, the point is that we need to remember that we cannot completely trust anti-virus. So while most of us have come to think of anti-virus/anti-malware as a necessity, it is only one piece of the puzzle when protecting your environment.
3. I have to worry more about the internal threat than everything else.
In all honesty, you do have to worry about the internal threat, but definitely not to the exclusion of all others. For that matter, not even ahead of all others. I don’t necessarily want to generalize, but generally speaking, companies should not generalize. Most organizations should have an understanding of the market in which they work, and of the threats to which they are normally exposed as part of normal operations.
Perhaps your biggest threat is insiders – but I have been doing this stuff for almost 30 years and I have yet to meet the organization that really needed to prioritize the insider threat above all others.
I probably abuse the data, but PrivacyRights.org is a valid source of reported breach data. As of 19 Feb 2013, they show data on 3617 breaches going back to June of 2006. As of the time I wrote this, the breaches included a total of 607,110,929 records.
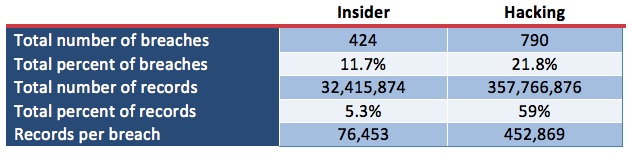
Comparing the number of breaches that were attributed to “improper insider access” and “hacking” shows some interesting statistics.
The numbers from the Privacy Rights Clearinghouse don’t even have to be close to show the fallacy of “the evil insider” claim. The site shows only a little bit over half as many insider breaches as “hacks”, which included about 9% of the number of compromised records. Not only that, but from the reported data, the average hack compromised almost six times as many records.
Now, that does not mean I am saying you should only be worrying about the external threat. The point is not to develop tunnel vision on how overwhelming the insider threat is. Oh, it obviously is a threat, just not the only one.
4. Companies want to be secure.
Well, kind of. We buy information security because we have to, not because we want to. No one ever says, “You know, it would be really cool if we spent $800,000 to add layered firewalls and create a series of DMZs for our web and commerce sites.” No one ever thinks that buying an enterprise license for anti-malware software is a good investment that helps an organization meet its business goals (well, except for anti-virus vendors).
We don’t buy security because it is cool. In the end, we buy security because:
a. We have to because of some regulatory or other compliance requirement.
b. We have to in order to protect the information we need to actually run the business.
c. We have to because we want to avoid exposure to litigation in the event we do lose information due to criminal activity or some accident.
We HAVE to.
Yes, I suppose that the truth is that most companies have a vested interest in protecting their information and the information of their clients, and generally WANT to do the right thing and serve as a good custodian of that information. But, if we could propose a complete and total end to all viruses, cyber-crime, and hacktivists, how many of those same companies do you expect would object?
Thought so.
5. I have a Mac, I don’t worry about viruses.
Maybe once upon a time I would not have argued against this statement, but malware like MacDefender, MacProtector, and others like them prove this is just no longer true. Flashback reportedly infected over 600,000 Apple computers – that is not just a drop in the bucket.
Yes, anyone would admit that there are dramatically more viruses that affect PCs than there are that affect Apple systems, but there is a very good reason for that. At less than 11% of the Operating System market, there are so many fewer Apply systems that they are just not as attractive targets as are PCs. Think about that if you want to feel better. If I am writing a piece of malware, and have to decide on my target audience, do I want to target the group of 900, or the group of 100. I can even get a lower percentage of the 900 and still get better results, simply because there are so many more of them.
But, there are still people poking at the 11% – partially because of the invulnerable attitude that seems to infect them. The virus is part of the problem, but the lack of awareness is just as important.
Armageddon Revisted.
In reality, expecting the world to end because the Mayan calendar ended would be like saying that the world was going to end because the 2012 calendar I got from my insurance agent only goes through December 31st.
So, maybe we are working on borrowed time.














