For the past several years, enterprise security leaders have been challenged with the task of locking down endpoints with traditional security solutions that are proving to be ineffective against todays threats.
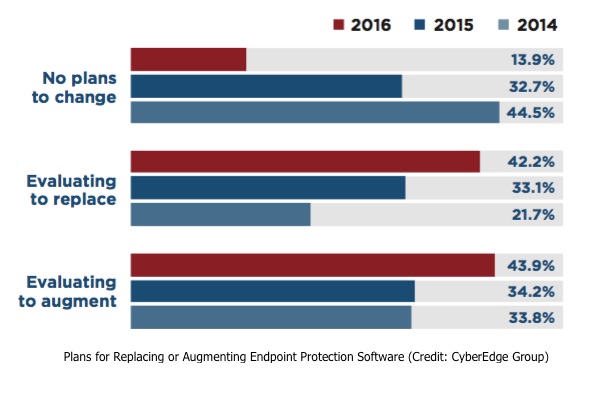
According to the results of a just-released survey of 1,000 IT security decision makers and practitioners, nearly 9 of ten respondents said their organization plans to replace or augment their current endpoint security defenses, maintaining the belief that current solutions in place are not providing adequate protection. That figure is up from nearly 7 of 10 respondents in last year’s report.
In its third-annual Cyberthreat Defense Report, released Thursday, CyberEdge Group found that an astounding 86 percent said they intend to replace (42 percent) or augment (44 percent) their current endpoint protection solutions. This figure is up from 67.3 percent last year.
Interestingly, respondents from Japan seem to be the most determined to get their endpoint security revamped, with 93.2 percent saying they would replace or augment their endpoint defenses.
“It has become abundantly clear that enterprises are fed up with inadequate endpoint defenses,” Steve Piper, CEO of market research firm CyberEdge Group, told SecurityWeek.
For three consecutive years, respondents have expressed growing dissatisfaction with their current endpoint security defenses.
“I believe we’re at the dawn of an endpoint protection revolution, opening up new doors for security upstarts to augment and, in some instances, replace traditional endpoint security platforms,” Piper said.
“Although signature based antivirus/ anti-malware still tops the currently-in-use technologies list, its hold on this position is clearly tenuous, as it also took the biggest hit in year-over-year results, stumbling just over 11 points,” the report said.
Traditional signature-based antivirus solutions have been under fire for years, with some vendors even admitting to inefficiencies of their own products.
Antivirus “is dead,” Brian Dye, Symantec’s senior vice president for information security at the time, told The Wall Street Journal in 2014.
While many accept the fact that traditional signature based security tools won’t do the job, most companies have not given up on the technology altogether.
“The effectiveness and value of traditional endpoint security solutions, especially those that rely on signature-based detection mechanisms, have been in question for some time,” CyberEdge said in its report. “However, with advanced malware now featuring countless tricks – such as polymorphism, active sandbox deception, and the ability to erase all traces of its presence after striking – the answer is clearly in.”
Respondents from Germany (76.2 percent) and the government (75.4 percent) and education verticals (77.4 percent) expressed the least amount of interest in making a change to their endpoint security setup, the report found.
Among those organizations said to be looking for something new, there was roughly a 50:50 split between those intending to replace their incumbent endpoint protection solution and those merely looking to augment it, the report revealed.
The latest report from CyberEdge is certainly not the first to indicate concern over endpoint security. According to Ponemon Institute’s 2015 State of the Endpoint Report, 71 percent of survey respondents said managing endpoint risk has become exceptionally difficult in the last two years.
A report from Enterprise Strategy Group (ESG), released at this time last year, highlighted the fact that traditional endpoint solutions such as antivirus and host-based firewalls that rely exact-match signatures and rules are struggling to keep up with the techniques used by today’s attackers.
In a 2015 survey of 340 IT and information security professionals by ESG, eighty-five percent said their organization planned to spend more on endpoint security, with improving incident response (29 percent) and detection (29 percent) cited as the two key reasons.
Other findings of interest in the 2016 Cyberthreat Defense Report include:
Increased Spending – 85 percent of responding organizations indicated they are spending more than 5 percent of their IT budgets on security, up from 70 percent in 2015.
BYOD Deployments Drop – The percentage of organizations with active BYOD deployments dropped for the third consecutive year – from 31 percent in 2014 to 26 percent in 2016.
Network security wish list – Next-generation firewalls were the top-ranked network security technology planned for acquisition in 2016, followed by threat intelligence services and user behavior analytics.
Mobile Risks – For the second consecutive year, mobile devices were perceived as IT’s “weakest link.” Overall, 65 percent of respondents said they witnessed an increase in mobile threats over the prior year.
SSL blind spots – Just a third of responding organizations said they have the tools necessary to inspect SSL-encrypted traffic for cyberthreats, revealing a gaping hole in enterprise security defenses.
“While there are no silver bullets, the strategy that is working best for the organizations I speak to is a proactive stance,” Simon Crosby, Co–founder and CTO at Bromium, wrote in a recent SecurityWeek column. “A new generation of endpoint security suite providers has emerged, and there is a clear need to identify which of the offerings can both detect breaches and secure your endpoints, while allowing you to empower your users. It is imperative that you begin to re-evaluate the endpoint, and to move beyond legacy endpoint protection platforms that simply cannot protect the endpoint or detect rapidly evolving attacks.”
“These results point to a segment of the security market on the verge of revolution – one where incumbent providers are far from safe as so- called next-generation endpoint security solutions are poised to grab a significant piece of the pie,” CyberEdge concluded.
The 2016 Cyberthreat Defense Report was compiled after surveying 1,000 IT security decision makers and practitioners representing 19 industries and 10 countries across North America (U.S. and Canada), Europe (U.K., Germany, and France
), Asia Pacific (Australia, Singapore, and Japan), and Latin America (Brazil and Mexico) in November 2015. Respondents completed a 26-question online survey, and each participant was employed by a commercial or government entity with a minimum of 500 employees.










