App Genome Project Enables Rapid Identification of Bad Applications
San Francisco based Smartphone security company, Lookout, today unveiled plans for an initiative to map and study mobile applications in order to identify security threats and provide insight into how applications are tapping into personal data and accessing other phone resources.
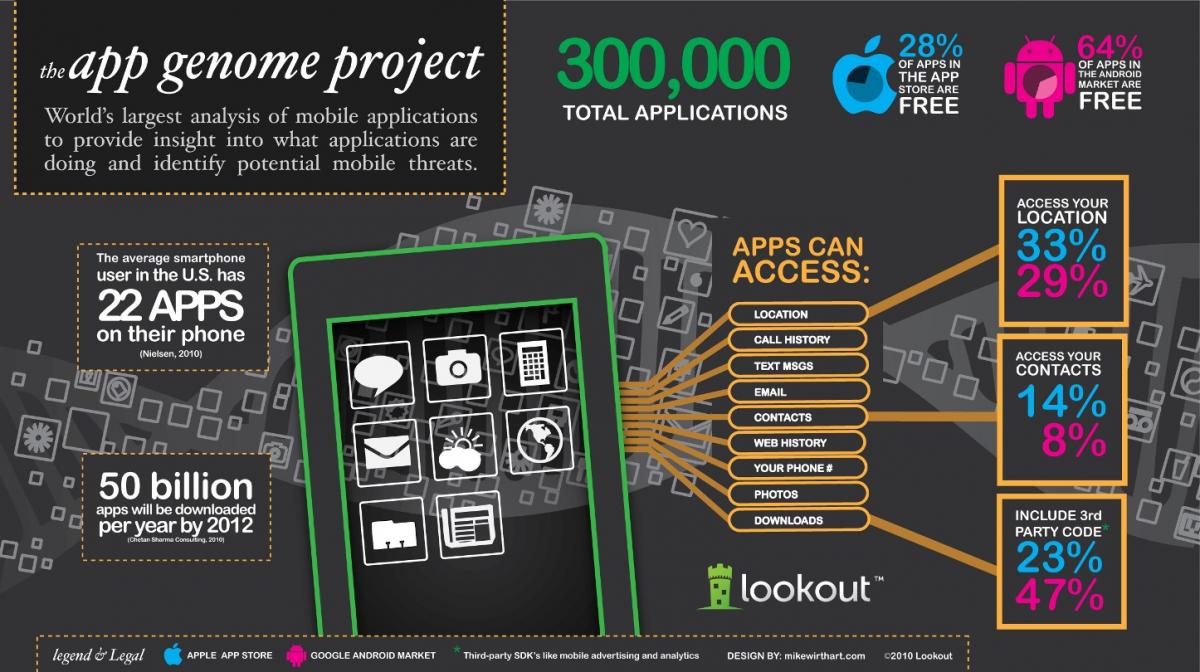
The project, dubbed “App Genome Project,” has already scanned nearly 300,000 and fully mapped almost 100,000 applications but will be an ongoing effort. 
Discoveries so far show differences in the sensitive data that is typically accessed by Android and iPhone applications and a proliferation of third party code in applications across both platforms.
The project examines components that make up mobile applications and determines what mobile applications are capable of doing when people install them. By combining real time application analysis with an understanding of platform issues, Lookout security researchers are able to rapidly identify applications that are either unintentionally or intentionally creating security risks for users.
Results found that applications on Android are generally less likely than applications on iPhone to be capable of accessing a person’s contact list or retrieving their location, with 29% of free applications on Android having the ability to access a user’s location, compared with 33% of free applications on iPhone. Additionally, nearly twice as many free applications have the capability to access people’s contact data on iPhone (14%) as compared to Android (8%).
The App Genome Project also found that a large proportion of applications contain third party code with the capability to interact with sensitive data in a way that may not be apparent to users or developers. This third party code is generally supports ad serving or analytics. The project found that 47% of free Android applications included this third party code, while that number is just 23% on iPhone. Third party code is difficult to globally update and creates potential cross platform vulnerability.
“The ability for applications to easily access personal data has opened up a world of possibilities for mobile applications, but also places a greater burden of responsibility on both developers and users,” said Kevin Mahaffey, CTO of Lookout and co-author of the study.
At the Black Hat security conference this week, Lookout security researchers will release findings from the App Genome project and demonstrate new vulnerabilities caused by inadvertent developer practices and platform issues.
App Genome Project












