Juniper Networks today released its 2011 Mobile Threats Report which showed a 155 percent increase in mobile malware across all mobile platforms in 2011, and a whopping 3,325 percent increase in malware specifically targeting the Android platform in the last seven months of 2011 alone.
In addition to a significant jump in overall mobile malware, Juniper echoed the industry consensus that the sophistication of malware-infected applications and other schemes targeting mobile devices has increased, with a new level of maturity reached in terms of security threats targeting mobile devices.
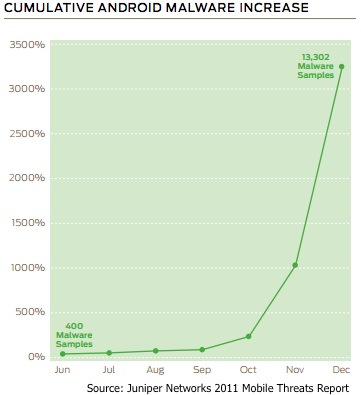 Juniper’s Mobile Threat Center (MTC) examined more than 790,000 applications and other vulnerabilities across every major mobile device operating system to compile the report. Juniper says its MTC’s malware sample library contains over 28,000 samples, which compared to traditional PC-based malware is tiny, but is significant in terms of growth percentage.
Juniper’s Mobile Threat Center (MTC) examined more than 790,000 applications and other vulnerabilities across every major mobile device operating system to compile the report. Juniper says its MTC’s malware sample library contains over 28,000 samples, which compared to traditional PC-based malware is tiny, but is significant in terms of growth percentage.
Juniper noted that many of the threats didn’t actually exploit technical vulnerabilities, but instead relied on social engineering tactics, including an attack method known as “Fake Installers”, a way cybercriminals dupe victims into paying for applications that may otherwise be available for free.
In other attacks, victims can be hit with Premium SMS scams. “Victims are tricked into agreeing to terms of service of pirated applications that then send profits via premium SMS messages to the scammers,” noted Daniel Hoffman of Juniper Networks. “While these attacks don’t lead to complete financial ruin, they have the promise of making attackers a tidy profit a few dollars a time.”
In January 2012, Denis Maslennikov, a mobile security expert from Kaspersky Lab, discovered what he said was the first IRC bot for Android. In this case, the malicious Android application had disguised itself as “MADDEN NFL 12”, a mobile version of the popular NFL football video game, but instead is mobile malware is packaged with a root exploit and an SMS Trojan, working in tandem and providing the attacker with full access to an infected Android device.
“In 2011, Juniper Networks observed industrious hackers moving malware from proof of concept to profitability,” the report notes. “Whether the motivation is notoriety, corporate espionage or financial gain, today’s hackers are more sophisticated and chasing higher rewards in their attacks. This means sensitive information from businesses, governments, service providers and users is at greater risk.”
In its threat report for the first half of 2011, Damballa said that the number of Android devices engaging in live communications with a command-and-control server reached nearly 40,000 at one point.
A Low Barrier to Entry?
“There is a low barrier to entry,” Juniper says. “Applications are turning out to be the “killer app” for hackers — and application stores are fast becoming the prime delivery mechanism for infected applications. Mobile users are downloading applications more than ever before. As we have seen a boom in the number of application developers, we have also seen a flood in the number of attackers. Juniper MTC data shows an evolution from more sophisticated, complex and deep attacks to attacks that are lightweight, fast, and application-based.”
Android Developer Resource: Mitigation of Security Vulnerabilities on Android
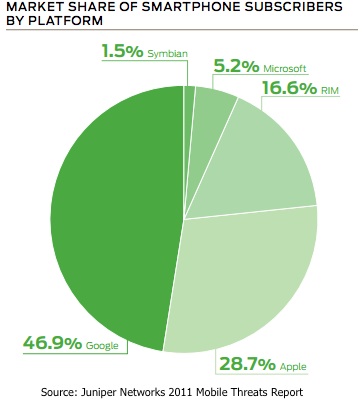 In fairness to Android, it’s simply a more attractive platform for attackers. Given the open platform and Android market which until recently, had little oversight and allowed malicious applications to often work their way into alternative android markers and even the official Android Market, it makes sense that attackers would target Android. While iOS is by no means immune to mobile malware, the platform has enjoyed a much safer environment due to Apple’s closed system and application approval process. Android is also wildly popular, and out pacing many other rivals including BlackBerry OS, Windows Mobile, and others. Massive adoption and path of least resistance make it an obvious choice for attackers looking to capitalize on the smartphone boom.
In fairness to Android, it’s simply a more attractive platform for attackers. Given the open platform and Android market which until recently, had little oversight and allowed malicious applications to often work their way into alternative android markers and even the official Android Market, it makes sense that attackers would target Android. While iOS is by no means immune to mobile malware, the platform has enjoyed a much safer environment due to Apple’s closed system and application approval process. Android is also wildly popular, and out pacing many other rivals including BlackBerry OS, Windows Mobile, and others. Massive adoption and path of least resistance make it an obvious choice for attackers looking to capitalize on the smartphone boom.
2012 promises to be a remarkable year for mobile device security, Juniper says, with the projected rapid increase in malware already being seen. “Other notable trends include the targeting of online banking and financial transactions, browser-based exploits including drive-by downloads and the targeting of third-party applications installed on the device,” Hoffman added.
“Although [mobile] malware is still pretty rudimentary it’s mostly because it does not have to be too sophisticated to thwart defenses today,” Dan Hubbard, chief technology officer at Websense, told SecurityWeek in November. “We have seen some more sophisticated stuff coming out that does server-side polymorphism and some interesting banking Trojans also.”
While the number of threats targeting mobile devices will absolutely increase, the good news is that user awareness seems to be improving, though still may have a long way to go.
“We think that users in general are becoming more aware of security threats in general, and have been hearing more about Android attacks and exploits in the past few months,” said Kurt Stammberger, Mocana’s vice president of market development told SecurityWeek in late 2011. “As smartphones displace old feature phones, even consumers are aware that these devices are, for all intents and purposes, computers in their pocket. And consumers have plenty of personal experience with malware and virus infection on their home PCs, so it’s not difficult for them to see where this all is heading.”
Juniper’s 2011 Mobile Threats Report is available here. (Free PDF)
Related Reading: Department of Defense Makes Move Towards Android












