Amazon’s latest security offering provides Amazon Web Services (AWS) customers with a separate appliance to securely store encryption keys, issue digital certificates, and manage cryptographic keys used for data encryption.

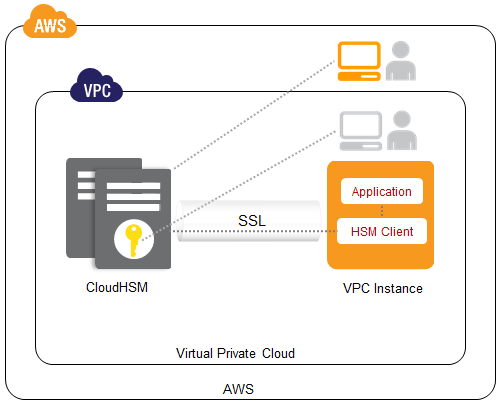
With the new Amazon offering, called AWS CloudHSM, customers can store their encryption keys in a dedicated Luna SA appliance from SafeNet, Jeff Barr, chief evangelist for Amazon Web Services, said on the AWS blog. Available within Amazon EC2, CloudHSM (HSM is short for Hardware Security Module) is available as an appliance within the company’s Virtual Private Cloud. Amazon can manage the physical appliance, but cannot access anything stored within the appliance.
Up until now, companies who needed to retain control over their keys had to keep their most sensitive data on-premise or deploy physical appliances to manage the keys. If the data was in the cloud and the keys were stored locally, performance was slow because of network latency to decrypt and encrypt the data. With CloudHSM, customers now have access to a dedicated hardware security module in the cloud, Amazon said.
Free Resource: Aberdeen Research: Encryption, Without Tears
“With AWS CloudHSM, customers maintain full ownership, control and access to keys and sensitive data while Amazon manages the HSM appliances in close proximity to their applications and data for maximum performance,” Amazon said.
The new service can be used to support “a variety of use cases and applications,” such as database encryption, digital rights management, and public key infrastructure, Amazon said. PKI includes authentication and authorization, document signing, and transaction processing. CloudHSM targets customers subject to stringent regulatory, corporate, and contractual requirements to apply additional layers of data security.
“Some of our customers are in situations where contractual or regulatory needs mandate additional protection for their keys,” Barr said.
The Luna SA appliance has a tamper-resistant enclosure and can use the stored cryptographic key without exposing it outside the device. CloudHSM customers receive a single-tenant access to each Luna SA appliance, which appears as a network resource in Amazon’s Virtual Private Cloud. VPC customers access their virtual servers over virtual private networks and employ other layers of security.
Customers can create and manage cryptographic keys, create user accounts, and perform cryptographic operations using those accounts, Amazon said.
“You can securely generate, store, and manage the cryptographic keys used for data encryption such that they are accessible only by you,” Barr promised, adding, “We do not have access to your keys; they remain under your control at all times.”
CloudHSM costs $5,000 upfront and $1.88 per hour for as long as the customer owns the appliance. That averages out to about $1,373 per month. Network data transfers in and out of each unit exceeding 5000GB per month will incur an additional charge of $0.02 per GB. While there is no additional charge for using the VPC, enterprises connecting via hardware VPN gateway will be charged $0.05 per hour.
The service is available for two of Amazon’s data center hubs, US East (Northern Virginia), and EU West (Ireland) and the plan is to slowly expand to include other Amazon data centers around the world based on customer demand.
Resource: Is Your Enterprise Managing Certificates? Three Reasons It Should Be.

















