Amazon announced this week that it has added five new security and encryption features to its Simple Storage Service (S3), including one that alerts users of publicly accessible buckets.
Improperly configured S3 buckets can expose an organization’s sensitive files, as demonstrated by several recent incidents involving companies such as Viacom, Verizon, Accenture, Booz Allen Hamilton, and Dow Jones.
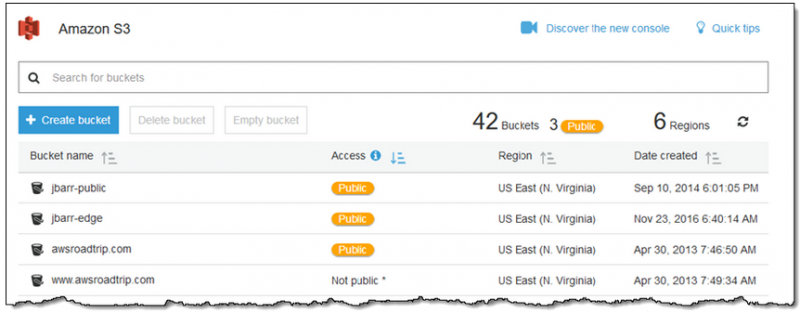
In an effort to help organizations avoid data leaks, Amazon introduced permission checks that provide clear information and indicators about publicly accessible buckets. The feature was made available shortly after Amazon announced the launch of a set of managed configuration rules designed to help users secure their S3 buckets.
With the introduction of permission checks, users immediately know if a bucket is configured for public access via the main page of the S3 Console and in each bucket’s own page.
Users can now also install an encryption configuration to mandate that all objects in a bucket must be stored in encrypted form. This means that customers will not have to create a bucket policy for rejecting non-encrypted objects.
Two of the new features are related to Cross-Region Replication, functionality that allows users to copy mission-critical objects and data to a bucket in a different AWS account. Objects are typically copied with the associated access control list (ACL) and tags, but a new feature enables users to replace the ACL while the data is in transit to ensure that the owner of the destination bucket has full access.
When administrators use Cross-Region Replication, they can now also replicate objects that are encrypted with keys managed via the AWS Key Management Service (KMS).
The last new feature is related to S3 inventory reports, which now provide information on the encryption status of each object.
All the new features are immediately available at no extra charge.
Related: AWS S3 Buckets at Risk of “GhostWriter” MiTM Attack
Related: Amazon Launches “Macie” Security Service to Protect Data in AWS

















