Jigsaw, a unit of Google’s parent company Alphabet, on Tuesday made available a quiz that tests users’ ability to identify phishing attacks and teaches them what signs to look for to determine whether an email or webpage is legitimate or not.
The quiz first instructs users to enter a name and email address, which will not be stored anywhere, but will help make the quiz more realistic, Jigsaw says.
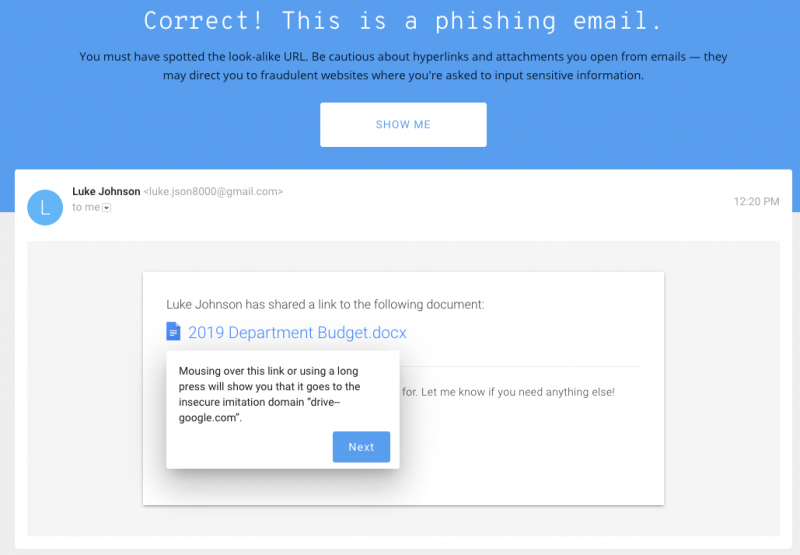
Users are shown eight different pages and for each of them they have to say if it’s part of a phishing attack. The user is given hints on what to look for in each case.
Once the “phishing” or “legitimate” button is pressed, the individual taking the test is informed whether the response was correct or not, and an explanation is provided for each of the elements that could point to a potential phish.
The emails include financial-themed messages, fax notifications, messages that appear to be personal and link to a photo, Dropbox notifications, and security alerts. The last test involves a page where the user is asked to allow an app to access their email messages and settings.
Once the quiz has been completed, the user learns how many of the tests they’ve passed and they are provided a link to Google resources for securing their account.
“Kudos to Jigsaw for building greater consumer awareness on this important topic. This is a solid effort that clearly highlights how crafty modern phishing emails can be,” commented Michael Madon, SVP & GM, security awareness at Mimecast. “But this crash-course is no substitute for ongoing initiatives by IT security leaders to tackle this education problem and truly change the security culture of an organisation.”
“Employees need compelling reasons to care about security. Mimecast’s training data analysis shows that individual risk scoring is a key factor. When used alongside humorous content, the passive resistance most employees have to training can be broken down,” Madon added. “Email security controls can be modified depending on the organisation’s own security stance, real inbound threats and the training scores of employees.”
Related: Phishers Use Zero-Width Spaces to Bypass Office 365 Protections
Related: Evasive Malware, Meet Evasive Phishing
Related: Latest Phishing Technique Uses Fake Fonts to Evade Detection














