What’s in your Extended Enterprise?
Analyzing its make-up and what risks it carries
Coined years ago, the term “extended enterprise” acknowledges that organizations are no longer just made up of employees and management working under one roof, but also encompass partners, suppliers, service providers, and customers. Fast forward to the digital present where it has taken on a whole new meaning and a whole new set of risks. Enterprises today exchange information almost completely online with more providers and partners, in more ways and more places than ever, enabled by technologies such as cloud computing, virtualization, and social networking.

While this seamless engagement with outside organizations in virtually all business processes is good for the bottom line, it opens enterprises to a whole new set of security issues. Any security breakdown outside of a company’s walls can instantly become a problem inside its walls.
Dangers to the extended enterprise have been clearly and starkly illustrated by hijackings of organizations’ Domain Name System (or DNS) accomplished through the compromising of their extended enterprise partners. DNS acts as a directory between a domain name and an IP address. When it is hijacked, either directly from an organization or indirectly via an extended enterprise partner, cyber criminals gain access to vital data at the victim organization – as if they were inside it.
For example, with CheckFree, the nation’s largest e-bill payment system, hackers were able to hijack the company’s domain names by stealing the user name and password needed to make account changes at Network Solutions, CheckFree’s domain registrar. The criminals then logged in to the extended enterprise partner’s system using these stolen credentials, changed the address of CheckFree’s authoritative DNS servers, and pointed visitors to all of CheckFree’s domains to an Internet address loaded with malware and controlled by a server in the Ukraine. As recent DNS attacks have proven, organizations must understand the risks and vulnerabilities they are exposed to via their extended enterprise connections so they can take proper steps to protect the integrity of their system.
Another emerging trend is the tighter regulations to protect personally identifiable information (PII) and sensitive customer information. Exposure of huge data breaches in recent months has led legislators and regulators to scrutinize the complex nature of the extended enterprise and the roles organizations have in keeping their customers safe. Insurers have taken notice as well. It is no longer sufficient to carry standard liability insurance and blame others when your customers’ data is lost. Putting concrete programs in place to protect your customers’ information wherever you send it, auditing the security of your partners, and having active procedures for incident response and mitigation are all required to avoid fines and direct liability when breaches occur that expose data anywhere in your extended enterprise.
No matter what category of enterprise, most are missing a coherent picture of their extended enterprise and therefore cannot identify its vulnerabilities. Below we will explore the make-up of a typical extended enterprise: what departments own these vital connections, and what vulnerabilities may be lurking through these webs of relationships.
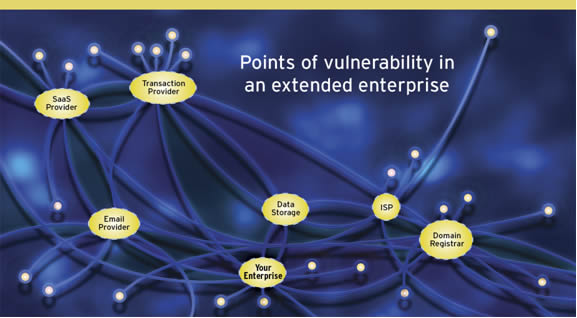
IT Operations
IT Operations own some key business relationships and also manage the technical connections with your extended enterprise partners. These departments are the heart of an enterprise’s Internet operations from which everything branches out.
Here’s what to look for:
• Domain Name Registrars and Internet Service Providers (ISPs) – The registrar is the linchpin for your enterprise’s online presence, and ISPs provide vital connectivity, systems hosting and e-mail. When these key vendors come under attack or have their systems compromised, your organization’s entire online operations are at critical risk.
• Third Party Application and Content Providers – With the emergence of social networking and news organizations sharing stories from multiple outlets more frequently, third party applications and content are more vital than ever to secure. But who manages all of these third party applications and content? If a content partner is compromised, your users could be unknowingly redirected somewhere dangerous online through your trusted location.
• Transaction providers and partners – Examples of transactional relationships include Automated Clearinghouse (ACH) transaction partners, credit card processors, order fulfillment services and outsourced customer service providers. While the business owners for these relationships may be scattered throughout an organization, IT Operations is likely responsible for implementing the actual transactional communications infrastructure. Threats to that infrastructure, such as DNS hijacking or connectivity disruptions, can cripple an organization’s ability to carry out business. Even worse, your systems could automatically send PII straight to the criminals who pirated your partner’s infrastructure.
• Your company’s most visited Internet locations – Like it or not, Google, LinkedIn, Facebook, CNN and other websites popular with your employees are part of your extended enterprise. Search and news sites provide timely information, while social networking sites help your sales team connect with key prospects. If a website or service that employees regularly frequent is compromised, your entire organization may be exposed to dangerous malware or other threats.
Finance and Accounting
The Finance group is likely a business owner for many of the transactional relationships described above, like the ACH and credit card processors. It also manages relationships with many other financial services providers, including banks, finance companies and collection agencies. Members of your finance and accounting teams routinely log into transaction systems to conduct company business with your various accounts. Compromises at these extended enterprise partners or to the communications channels that connect your organization to them can do immediate, tangible damage to your organization’s bottom line.
Legal
Your organization’s legal group regularly communicates highly confidential information with counterparts at other companies and with outside legal counsel. What happens if the security at the law firm or a company you are negotiating with is compromised? Vital information for an enterprise could give criminals open access to bids, contracts, merger and acquisition data, employee information, and so on.
Human Resources
Does your organization outsource staffing in any form? For example, do you use staffing services to hire, use an outside source to conduct payroll, use a PTO tracking vendor? You undoubtedly deal with state and federal agencies on employment issues, and of course with insurance companies, too. If so, that means you regularly communicate vital employee data like social security numbers with these companies. If any of these extended enterprise partners is compromised, cyber crooks suddenly have personally identifiable information and you have the liability and direct cost of a data breach problem.
Sales
If you are like millions of enterprises, you outsource your Customer Relationship Management (CRM) to an outside vendor. These solutions provide intuitive, cost-effective, automated systems that keep in touch with current and potential customers. While the upside is great, these extended enterprise partners have your vital proprietary information, like contact information and insider documents. In one recent case, criminals used information stolen from a CRM vendor to launch highly targeted attacks against the organization’s clients, while pretending to represent the victim organization! Needless to say, the victim organization suffered significant harm to its reputation and its customer relationships.
Marketing
Do you use outside marketing help? Do you have an outside public relations firm? Do you use an outside design firm? To do their job for you, these extended enterprise partners need access to proprietary information like details about new products, merger and acquisition information, market statistics and more. What is the damage if that information falls into someone else’s hands?
Research and Development
Is your company constantly looking to develop and grow? Most medium to large sized businesses outsource some of their research and development. That means your top-secret product development information is outside your direct control, and protection. While these outside sources have most likely signed NDA’s, a criminal that hacks into that outside organization or intercepts your communications with them couldn’t care less about an NDA. Top secret project no more—now the product being developed could go to the highest bidder.
Conclusion
With today’s extended enterprise, the connections are endless. This outline is only the beginning of what to look for in an always-expanding ecosystem of online partners. These key questions will help define the components and extent of your extended enterprise and the risks that go with it:
• To whom do you routinely send Personally Identifiable Information (PII) and other sensitive data about personnel or customers?
• Who do you transact with regularly and automatically?
• Do your partners fully control their infrastructure and communications channels?
• Do your partners have all data safely stored?
• Will a liability contract cover your true losses? Is it ironclad, and how is the coverage limited?
• Will regulations apply if a data breach or loss of PII was a third party’s fault? Will your organization be penalized regardless, since ultimately your organization is responsible for that information’s safety?

In today’s Internet-connected world, organizations routinely and necessarily share large amounts of proprietary and mission-critical information with others. You must be able to trust other organizations as if they were part of your own enterprise. It is imperative for every organization to define, examine and understand its extended enterprise relationships and related risks. With so much information out of your direct control and protection, wouldn’t you want to monitor the security of everyone in your extended enterprise?
In order to keep your castle walls secure, you must make sure the village is secure as well.














