Large-scale financial cybercrime and state-affiliated espionage dominated the security landscape in 2012, Verizon said in its latest data breach report.
While 75 percent of all the breaches investigated by Verizon RISK Team in 2012 were financially motivated, state-affiliated espionage campaigns was the second most common type of breach, at 20 percent, according to the Verizon 2013 Data Breach Investigations Report released Tuesday. Cyber-espionage incidents included stealing intellectual property such as classified information, trade secrets, and technical resources, which could further national and economic interests, Steve Brannon, a senior analyst with the Verizon RISK Team, told SecurityWeek.
 Even though the proportion of incidents involving hacktivists—attackers targeting networks and systems for ideological reasons “or even just for fun”—remained constant, the actual amount of data stolen decreased from last year, Verizon RISK Team found. The drop in the number of records may be a result of hacktivists shifting to other types of attacks such as distributed denial of service attacks in order to disrupt business operations instead of going after business data.
Even though the proportion of incidents involving hacktivists—attackers targeting networks and systems for ideological reasons “or even just for fun”—remained constant, the actual amount of data stolen decreased from last year, Verizon RISK Team found. The drop in the number of records may be a result of hacktivists shifting to other types of attacks such as distributed denial of service attacks in order to disrupt business operations instead of going after business data.
“Some organizations will be a target regardless of what they do, but most become a target because of what they do,” Verizon RISK Team wrote in this year’s DBIR.
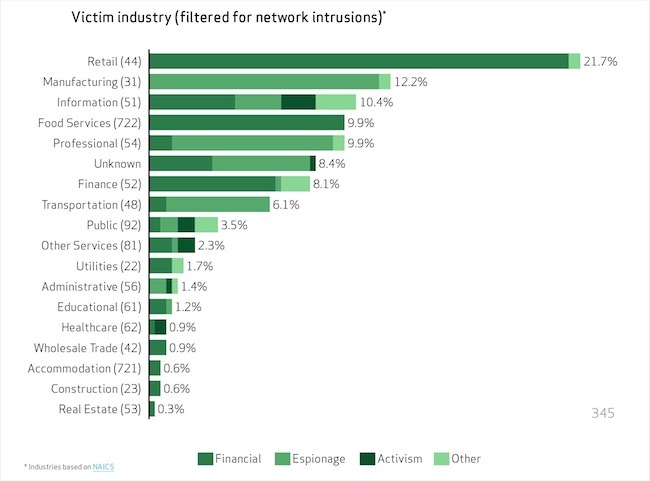
Enterprises, small businesses, government agencies, and global companies were all targeted in 2012, Brannon said. About 37 percent of breaches affected financial organizations, 24 percent affected retailers and restaurants, and 20 percent involved manufacturing, transportation and utilities, and information and professional services firms, according to the DBIR. While breaches in retail and restaurants declined since last year, attacks on other industry sectors all increased.
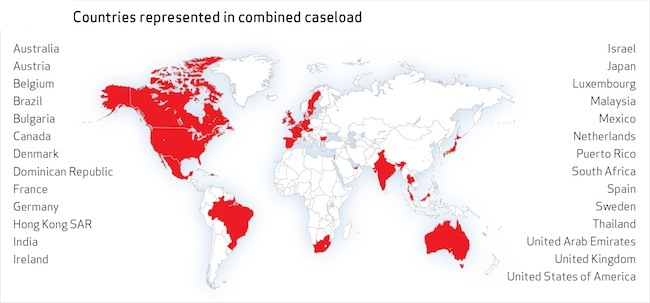
About 38 percent of all the attacks impacted large enterprises. Last year, the report tipped toward the small businesses, but this year, the ratio among organization sizes was fairly even, according to Verizon. This year’s DBIR contained data from 27 different countries.
Motives for these attacks were diverse, but the vast majority of the data breaches remained external attacks, at 92 percent. External attackers include groups such as organized crime, activists, former employees, long hackers, and even nation-state sponsored groups. In fact, state-affiliated actors tied to China were the biggest movers in 2012, with intellectual property theft consisting almost 20 percent of the breaches, Verizon found.
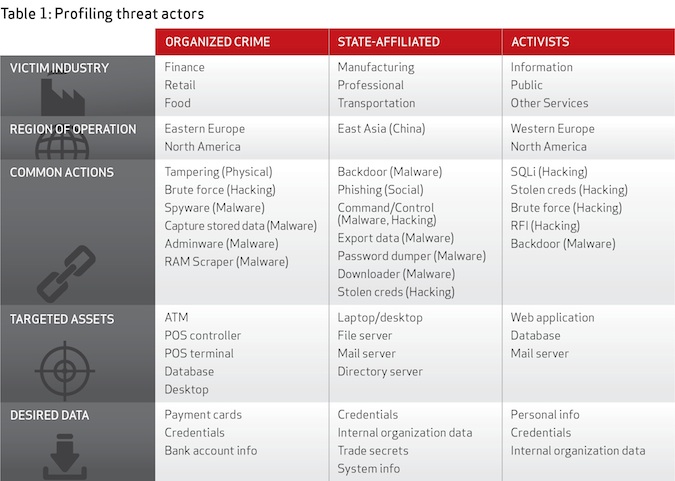
Despite the growing number of disclosures and news headlines, many organizations assume they won’t be impacted by cyber-espionage, Brannon said. Unfortunately, cyber-espionage is no longer just a problem for the largest enterprises, and can impact anyone, small or large, Brannon said. While size did not seem to matter, some industries to appeared to be more targeted than others, he said. Organizations also need to consider that even if no one is after their intellectual property, they may still be hit as part of a stepping-stone attack, where the attackers use one network as a “pivot point” into the actual targeted environment, according to the report.
Even though insiders accounted for only 14 percent of the data breaches included in the DBIR, when looking at all the security incidents in the report, “insiders wear the crown,” the Verizon RISK Team said. Insider attacks included simple card skimming and complicate plots intended to smuggle intellectual property to competitors.
Hacking remained the most common cause of data breaches, accounting for 52 percent of incidents in the DBIR, Verizon said. About 76 percent of network-based breaches exploited weak or stolen credentials, such as the username or passwords, while 40 percent employed some version of malware. Just 25 percent involved physical attacks, such as ATM skimming, and 29 percent took advantage of social engineering attacks, such as phishing.
Phishing attacks quadrupled in 2012, according to the DBIR. Verizon RISK Team speculated that the primary reason for the jump may be directly related to the fact that phishing is commonly used in targeted cyber-espionage campaigns.
The “one-two combo” of attacks using both hacking and malware was less common in 2012 than previous years, according to the report.
Almost three-quarters of incidents, or 71 percent, targeted user devices and 75 percent were considered opportunistic attacks, according to the DBIR. About 78 percent of the breaches were rated as “low difficulty” intrusions, suggesting that attackers didn’t need to employ sophisticated methods.
Breaches still take “forever and a day to discover, and that discovery is rarely made by the victim,” according to report. In fact, a full 69 percent of breaches were initially discovered by third-parties, according to the report, and 66 percent of the incidents took months to discover, even years.
The 2013 DBIR marks Verizon’s sixth year analyzing data breaches, and includes 621 confirmed breaches, 47,000 reported security incidents, and analysis provided by 18 different organizations around the world. Data partners include Ireland’s Guardia Civil, CyberSecurity Malaysia, Danish Defense Intelligence Service, and Europol’s EC3.
Over the past nine years, Verizon RISK Team has analyzed over 2,500 data breaches and 1.2 billion compromised records, according to Verizon.
“Understand your adversary—know their motives and methods, and prepare your defenses accordingly and always keep your guard up,” Wade Baker, principal author of Verizon’s DBIR, said in a statement.
The full report from Verizon can be found here.













