The world of cybersecurity is becoming more and more complicated and – some say – almost unmanageable. This is due to the increasing volume of advanced attack campaigns and subsequent investment by organizations in more and more security tools – tools that are potentially effective, but are also trapped in silos that limit their capabilities. Each of these security tools has its own abilities, with different policy models and different alert languages.
If you take, for an example, an organization that invests in at least 35 different security technologies and hundreds of devices, the result is a large group of platforms that don’t speak the same language, let alone integrate, creating heavy, non-adaptive and inflexible security infrastructures which, rather than enable security, actually burden it – unwittingly providing attackers with a continuous advantage.
This “the more the merrier” approach compels security teams to monitor and manage a jumble of non-integrated tools, leaving overworked staff desperately attempting to “connect the dots” (or correlate the information) in order to orchestrate their motley mix of defense capabilities to assure that each tool addresses the right threat at the right time. This presents an impossible task, no matter how large or skilled security teams are.
Our cybersecurity ecosystem needs to be simplified – this is a fundamental challenge that the industry has avoided talking about. This need for simplification is what lies at the core of “Security Abstraction “
As mentioned in previous columns, abstraction has been used successfully to solve similar problems when systems reach a certain level of complexity.
Security Abstraction
Security Abstraction enables the generalization of complex cyber security models. The goal is to break down the cybersecurity ecosystem into abstract components in a way that clearly defines the security role of each one – its pros and cons –all using one common language. This can provide us with a simplified view of the complex security infrastructures.
How will that help?
Understanding the role of each capability (security particle) leads to instant understanding of the security event that the same capability can generate – which is the intent of the attack. Security Abstraction enables the intent of each event to be instantly identified, allowing organizations to deploy the best security particles with the relevant capabilities to handle the threat. This abstraction process makes the work of determining if a real threat exists and effectively orchestrating the proper security “troops” to best deal with it much faster and more accurate.
Some people will say this is impossible. Well, it is certainly an enormous challenge – but not impossible. This is because of some significant technology shifts have occurred in the past few years:
• API – Based on demand from significant customers, vendors are designing and developing APIs that are more predictable and stable than ever.
• SDDC & NFV – Customers demand more “openness” and “programmability” in order to integrate, customize, and automate the underlying networking technologies and better fit them to their business needs. This results in more “transparency” of APIs internal functions, which allows for better control over these products.
• Artificial Intelligence technologies have advanced significantly, especially Machine Learning technologies that can artificially understand meaning and context, i.e., classification algorithms.
All these have created a foundation which makes security abstraction a reality.
Abstraction of complex security infrastructure means two things:
• Analyzing and breaking down security tools and services into their various detection, investigation and mitigation or remediation capabilities. This should be done continuously, because security products are constantly updated with new security data and hence, new capabilities (e.g., weekly updates of intrusion attack DBs, new malware hashes, etc.).
• Abstracting threats by analyzing the huge number of logs and classifying them into groups of security intents.
Machine learning is all about solving the problem of how to assign a new data point into a cluster based on previous learning processes. In the world of cyber-security, these data points can be attack signatures (in IDS/IPS attack databases), malware names and descriptions, or hashes, security rules etc., and the clusters represent groups of security intent. Each cluster has a different security meaning (a threat intent or a defense intent). This process is illustrated below:
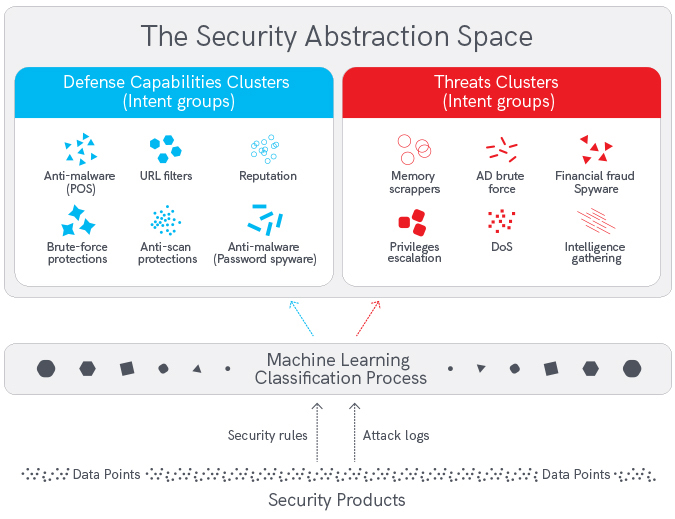
Per the illustration above, it is clear that by understanding the threat intent of the security logs (the threat clusters on the right side), it becomes simple to correlate them with the best security defense capabilities (the defense clusters on the left side).
To give a more concrete example of what we will expect from a classification process of attack logs or security capabilities into security intent groups (“security particles”), let’s look at the table below, which includes a selection of real threat data points, and the classification results that represents intents:
Machine Learning
| Attack Name (Taken from the log) | Threat Clusters |
| Dirty COW | Privileges Escalation |
| Mimikatz | Privileges Escalation |
| Xtreme RAT | C&C Activity |
| POODLE Attack | Intelligence Gathering |
| Citadel | Spyware (password theft) |
| KAPTOXA | POS Memory Scraper |
Machine learning plays a major role in creating this abstract view. It facilitates the creation of an adaptive security taxonomy which provides an understanding of both the security capabilities and of the threats themselves (which is the other side of the same coin), thus enhancing the ability to analyze a very large amount of security data. This enables instant data correlation, because when the intent is clear, correlation becomes simple. Lastly, it allows one to correlate the threat (per its intent) with the best response capability.
The value of machine learning classification algorithms goes beyond just clustering. The fact that these algorithms can work on almost any source of data points and group them into security clusters, i.e., into security intent groups, makes them agnostic to the underlying security products. This means that the security taxonomy created can be considered an abstract layer that sits on top of any medium to large organization’s existing security configuration, and provides the required clarity (discussed above), no matter which set of security vendors the organization decides to use.
Conclusion
Abstraction is a concept that has proven very successful in many instances, and should be adopted by the security community as well. Abstraction models such as the TCP/IP OSI communication model, smart phone “apps” platforms (e.g., IOS), and web design platforms are just a few examples of the great power that these models hold.
In the realm of cybersecurity, security abstraction can create radical change. It will enable swifter, more scalable identification, investigation and mitigation of threats, in a manner which is agnostic to the underlying security infrastructure. The clarity that security abstraction can provide will allow organizations to effectivity identify the intent of each security event no matter its source, and to correlate it with the best available response. The security resources are already there; we just need to learn to use them more effectively.














