Winning in the Cyber Battlefield: Transforming Cyber Defense Planning Model into Actions
In a real life battlefield situation, defenders analyze their own territory and decide which areas they want to protect, i.e., the strategic or essential areas. They then analyze the different routes to attack these areas. Routes to attacks will usually be categorized into risky, very risky but less likely to happen, most likely to happen with moderate risk and so on. Analysis is typically done visually as demonstrated below:
Figure 1: Battle of defense planning
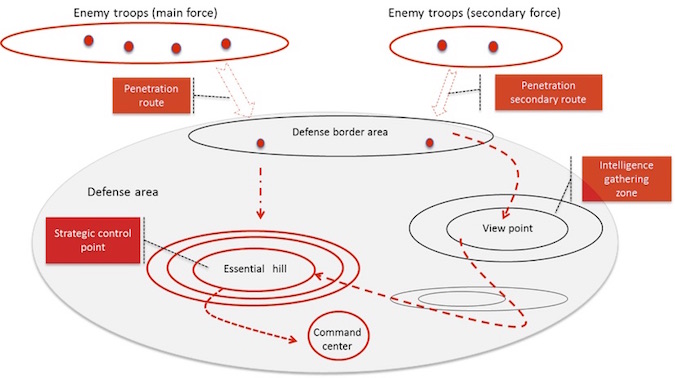
The defenders cannot predict exactly what the next attack will look like and how it will evolve. However, based on their knowledge of their own territory they can analyze the different possible routes to their essential areas, as illustrated above.
Analysis of this sort will allow the defender to plan what defense characteristics are needed and where to place them. This will then be followed by collecting real-time intelligence information from the field and updating what is actually happening vs. the defense plan. This allows continuous risk assessment and re-deployment of defense troops with the required characteristics accordingly.
Taking this analogy to the realm of cyber security, in the planning stages there shouldn’t be much of a difference.
Let’s take the famous Target breach case as an example. Based mainly on public attack analysis reports, it seems that the following general attack stages have taken place. As can be seen, the figure below already integrates some cyber risk analysis results and conclusions:
Figure 2: Cyber Defense Planning
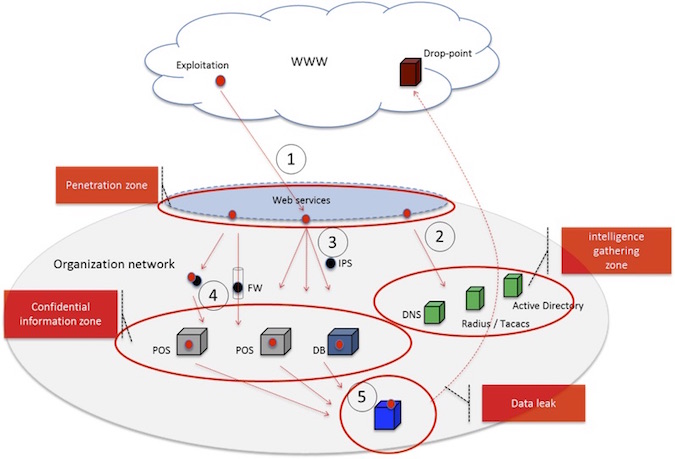
Following is a high level and brief description of what happened in this advanced attack case (in top down order):
• The attacker was able to gain access credentials of one of the target’s contractors (attack vector that is not seen in the illustration above).
• Penetration zone (1): The attacker access target’s web services used for contractors, exploits a web vulnerability on one of the web service hosts, and takes control over that host.
• Intelligence gathering zone (2 and 3):
– The attacker probes the identity and domain name services (e.g., active directory, DNS etc.) and gains information about potential services that store confidential information such as CC and other personal information.
– The attacker scans the network in order to learn its topology and discovers existing network security devices such as firewall and network IPS’s.
• Propagation into the confidential zone (4):
– The attacker activates different types of attack techniques in order to get network admin credentials, e.g., pass-the-hash attack, and to bypass through existing security devices, e.g., port forwarding and other application tunneling techniques.
– He/she then installs remote desktop and procedure tools used for installing malicious processes (malwares) on different hosts that potentially store confidential information.
• Data leak (5)
– The attack sets up an internal “drop-point” service which the malwares “drop” the information into.
– The information is sent to external “drop-point”…
Referring to the analysis of the above advanced threat scenario, some interesting security points need to be emphasized: the 1st is that there is no C&C channel that can be traced by a reputation system. The 2nd is that there is no internal user that downloads executable file(s) from the web, a process which will typically trigger a sandbox or file emulation mechanism that analyzes the file.
Another important security point that needs to be taken into account is that today’s advanced attacks are more prolonged than they have ever been before (read more on prolonged attack challenges in my post “Cyber War Rooms”). This means that defense planning must be done continuously during the attack lifecycle, and not just before it starts. The consequence is that deployment of new or updated countermeasure should be done in real-time against the developing attack – same as in the real battlefield.
My point is that, in order to be effective, security solutions must become more directly associated, in real-time, to the cyber defense planning model shown in Figure 2 above. It should also be much more agile than existing solutions so it can be constantly “shaped” to resist any evolved form of attack that tries to bypass it. Lastly, automatic “insertion” of the security defense functions where they are needed most must also be supported, so that the move from the defense planning model into security deployment will be fast at any stage of the attack.
Let’s look at the following example of the deployment of a solution based on real-time cyber defense planning:
Figure-3: Defense Planning Driven Deployment
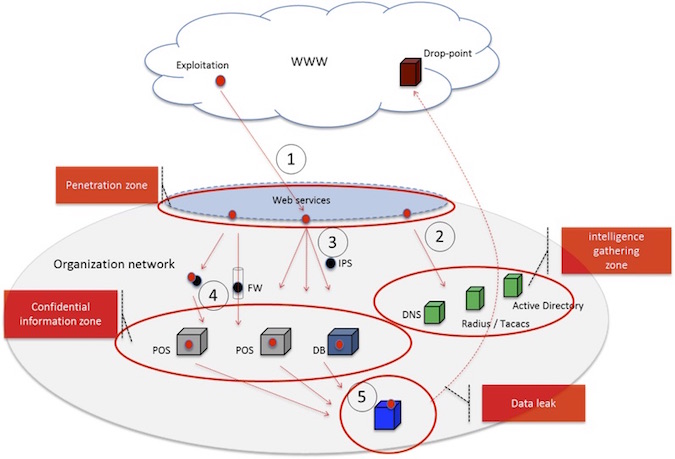
As shown above, “insertion” of a security service is done against the defense planning model. Intrusion prevention functions in (1), anti-probe security functions in (2), (3), user behavioral analysis functions in (4) and (5) – each with a different behavior scope.
This way a security expert can also analyze in real time which attack route the attacker has chosen and adapt the defense mechanisms accordingly – all in the context of the cyber defense planning model. It should be noted that this type of holistic security defense solution need to work across any network topology. For example, the servers in the confidential information zone can be located in multiple datacenters, some in the cloud and some on the premises – the solution should be agnostic to this.
It is obvious that any cyber security war room should adapt this security defense model which will allow real-time analysis and resistance to any form of advanced threat. Although the technology is not there yet, some technology shifts into this direction are on their way already. You may read more about these technologies in my previous column on “Disaggregated Security Functions”.














