Threat intelligence firm ThreatConnect announced this week the launch of a new suite of products designed to help organizations understand adversaries, automate their security operations, and accelerate threat mitigation.
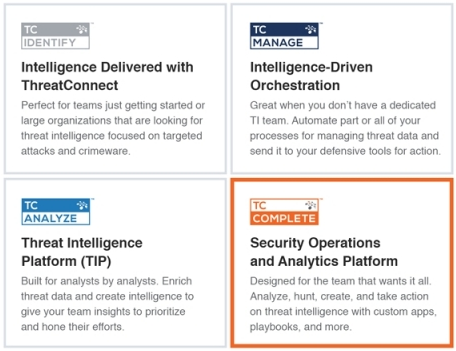
The new products, built on the ThreatConnect Platform, have been named TC Complete, TC Analyze, TC Manage and TC Identify.
TC Complete, the company’s flagship product, is a security operations and analytics platform that aims to enable companies to efficiently run their security operation center (SOC) by giving them the ability to orchestrate security processes, analyze data, respond to threats, and report progress from a single location. TC Complete incorporates the features and benefits of all the other ThreatConnect products.
Another new product is TC Identity, which provides vetted threat intelligence collected from over 100 open source feeds, ThreatConnect communities, the company’s research team and, optionally, intelligence from members of the TC Exchange program.
TC Manage is an intelligence-driven orchestration tool that enables organizations to automate threat data management processes, including notifying team members when manual tasks need to be performed, or sending indicators to defensive tools for blocking or alerting.
The last new product is the TC Analyze threat intelligence platform, which provides a central location for analyzing data and integrating with existing security tools. The platform allows analysts to better understand which threats are relevant, gain visibility into attack patterns, and share threat intelligence with executives and other stakeholders.
“By introducing our new innovative suite of products, we are able to address all levels of need in the marketplace. With these four specific products, ThreatConnect allows any organization with any size security team the option to extend its capabilities,” said ThreatConnect VP of Product Andy Pendergast. “We conducted substantial research into organizations’ current and potential intelligence needs to protect their environment and came up with these specific products to reach them where they are now and where they need to be in the future.”
Related: ThreatConnect Closes $16 Million Series B Funding
Related: Misconceptions of Cyber Threat Intelligence
Related: How to Make Threat Intelligence Practical for Your Organization














