An Opportunity for Datacenters with a Real Security Service Centric Approach
The concept of software defined networking (SDN) and the developed standard (Openflow) was first presented in a PhD paper by Martin Casado at Stanford. The question Casado asked was this: if we look back at the developments of the last 15 years or so in areas such as the Internet applications and mobile technologies, today’s world is virtually unrecognizable to what is was 15 years ago.
How is it then that the networking foundation on which everything sits has changed hardly at all? It is stuck in the virtual stone age of the Internet. The implications of this for networking companies and network professionals are tremendous: they are occupied mostly with trying to navigate the complexities of the archaic networking system, instead of focusing on developing real innovations (as we see in the world of applications and the Internet).

Openflow/SDN challenges the basis of the old style of networking, and suggests a completely new approach – a centralized algorithm and centralized intelligence, rather than a distribution approach. This democratization of networks would mean that anyone who wants to control the network, could do it through programming, using an Abstraction Layer or Network Operating System (Network OS). Specific network virtualization standards are not clear yet, and large networking vendors such as Cisco will likely try to stop open networking standards by developing their own proprietary SDN protocols. But despite this, it is clear that the SDN approach has laid the foundation for the future of networking.
Security Services Fabric in the Era of SDN and OpenFlow
SDN, and specifically the Openflow standard, allow simple and granular dynamic routing in next generation datacenter networks. Through new innovative networking virtualization techniques, it provides a networking abstraction layer that allows network managers to program their network fabric per their business needs. One of the important programming capabilities allows the creation of a virtual tenant network model based on the following main characteristics:
• Network computing resource allocations
• User groups
• Application groups
• Required routing algorithms
On top of these virtual network characteristic, the SDN approach allows the network manager to set the required security SLA. For example, a network manager can create a network application that would interface with the network controller (in the world of Openflow it is called “Openflow Controller” or OFC) and will distribute “intelligence” into its network. This can include user groups that are defined as casual users who will be given more “attention” and will be reflected through more security tools they will need to pass, while better-known, “trusted” users will be granted “easier” access to the applications. Taking this example further, the network security manager can also define the security SLA per the end point application that the users are targeting. If, for example, the group of users is targeting an Oracle application, the security filters that these users will need to pass through will be made to fit so as to avoid exploration of Oracle’s known application vulnerabilities.
Using the programmability characteristics of its network, the network security manager can define all these dynamic security rules per general security risk, a time of day, or any parameter he may choose.
The below diagram illustrates how the network manager can define the required security SLA per virtual network tenant, while maintaining the security resources in his network very efficiently:
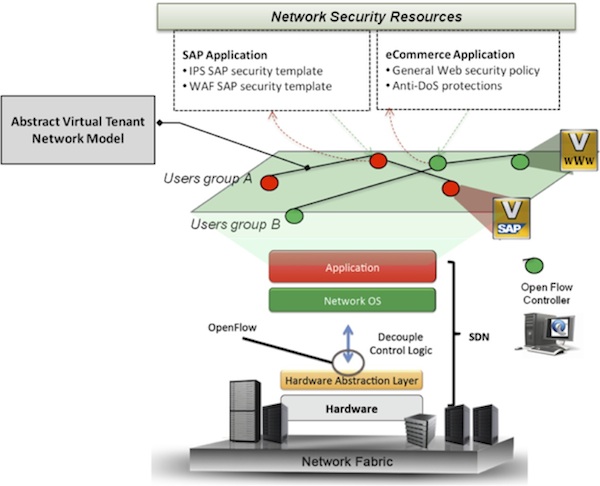
As shown above, the network virtualization abstraction layer “hides” the network physical resources and exposes only abstract logical network nodes that reflect the virtual network tenant – in this case it is defined per group of users and applications (e.g., Users group B to SAP application). The network manager can now choose to provision the proper security resources for specific application (e.g., SAP) in his network. The SDN approach would allow automation of the network operations associated with all that is needed to make that provisioning happen including:
1. Allocating the correct security resources in the network (e.g., firewall, WAF, IPS, Anti-DoS , AV solution, etc.,).
2. Allocating the computing resources of these security functions to meet the traffic processing demands.
3. Automatically creating routing rules that will divert only the users of the specific application through the relevant security resources (e.g., Users group B to SAP application).
4. Advanced policy rules allowing for this routing to take effect only in specific hours, dates or per any other risk analysis method that is applied by the network manager.
5. Further automation that utilizes the APIs of the security resources may allow an automatic configuration of the security rules per target application.
The above process is part of the programmable nature of the network. Thus, the network becomes more dynamic in order to adapt to the required security policies without any physical topology changes in the network and with a simpler, service centric approach that controls the application and the users rather than the network resources, products or features.
The Software Defined Secured Networking (SDSN) described above allows not only for the acceleration of networking innovation, but will also dramatically change the way we think about security. Security resources and layers will become an integral part of what the market today calls “Dynamic Datacenters”, and will be allocated, “shaped” and moved per demand in a simpler and more efficient way than ever.













