As long as human intelligence remains an unsolved mystery, we cannot expect a security system to provide us with a complete solution…
Over the past few years the market has developed new expectations from the network and applications security industry.
One of the most challenging expectations is that information security systems be able to not only detect attacks, but also prevent or mitigate them in real-time. This demand forces systems to be more independent from the human factor. Not relying on the human factor means that operations that were usually conducted by the security expert need now to be performed automatically by the systems themselves.
 The motivation behind the market’s demand for real-time prevention or mitigation rests on two foundations:
The motivation behind the market’s demand for real-time prevention or mitigation rests on two foundations:
1. The growth in the sophistication and frequency of attacks over the last few years.
2. More and more organizations are closely dependant on the Internet in order to conduct profitable business.
Together these factors result in demand for a very fast and accurate response to attacks which threaten Internet connectivity. In most cases, the human security expert cannot comply with the required response time.
When analyzing which technologies will best fit the market’s expectations, it becomes clear that developing new emerging security systems should involve an integration of “nontraditional security technologies”. These systems, in order to be effective, must take control of some responsibilities that before were in the hands of the human security experts.
This article includes a general explanation of the human brain’s assessment methods and how these methods are used by the security expert in order to assess a communication as an attack, suspicious or normal online activity. The main issue is to characterize behavioral analysis technologies which will meet the goal of emulating the human security expert. Technologies such as adaptive expert decision engines and closed-feedback systems are briefly explained.
Real-time Intelligent Decision Challenge
A short examination of the requirements for automated real-time attack mitigation reveals a major difficulty. Real-time mitigation assumes that the system comprises some kind of computerized “intelligence” that will emulate the operations that were previously conducted by the security expert.
In order to understand and confront the challenge of emulating the security expert, let us first characterize a potential process that the human brain executes in order to arrive at conclusions. Understanding the process will hopefully lead us to some conclusions regarding the technologies that may be effective in emulating the security expert.
Human Assessment Methods
In everyday life, the human brain encounters problems that involve varying degrees of freedom. These problems, whether they have to do with an analysis of communication systems or with basic physical operations such as walking, driving etc., can be extremely complicated. Despite this, they are all successfully handled by the human brain.
Degree of Freedom
A degree-of-freedom for a system is analogous to an independent variable for a mathematical function. All system degrees-of-freedom must be specified to fully characterize the system at any given time. In order to solve a multi-degree of freedom problem, a complicated mathematical procedure needs to be performed. The ability of our brain to perform the required complicated mathematical procedures doesn’t really exist. However, we are still able to handle problems that include many degrees of freedom.
The Analytical Approach and the Human Approach
The questions of how we are able to solve multi-degrees of freedom problems so fast without really solving the analytical equations is not yet solved. However, a few suggestions for systems that could emulate human brain operations were raised over the past two or three decades. One of them follows the assumptions which are presented below:
Qualitative Categories
In order to see, feel or hear we use our sensors (i.e., our eyes, ears, etc.). Although the sensors’ inputs can be very precise, we map the environmental inputs we are getting into qualitative categories. When we sense heat for example, different intervals of temperatures will be associated with different qualitative categories. The same goes for quantities such as velocity and distance. Every type of variable has its own set of qualitative categories that are constructed through time in an adaptive manner. The following diagrams illustrate two types of qualitative categories and how inputs from the environment are mapped into the domains of these categories:
Figure 1- Distance Qualitative Categories
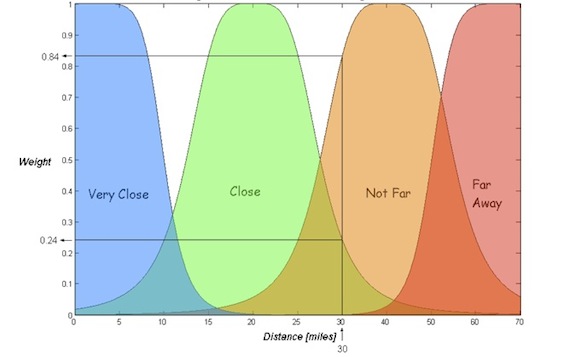
This set of qualitative categories enables us to map precise inputs into these illustrated groups. The position of every input on the x-axis and the category’s shape define the output which is the weight (y-axis). The weight represents the degree in which each input belongs to a specific category.
Adaptation
After qualitative categories have been shaped and positioned along their reference axis, it is assumed that the order and styles of the shapes will not change over time, unless a drastic change in the environment’s rules takes place. However, the position of the categories can be shifted along the reference axis (i.e., x-axis), as well as categories’ actual shapes within their styles according to an adaptive process.
For example, if we take the distance set of category shapes (i.e., very close, close in Figure 1) and use those in order to quantify the distance between our location and that of a person standing in front of us, then 70 miles will be considered as ‘Far Away’. In most cases, this seems to be a reasonable decision. But if we want to use the same set of distance category shapes in order to quantify how close or far from us an asteroid is located, than a 70 miles input will have to produce ‘Very Close’ output.
The adaptation process helps us to shift and to scale (i.e., shrink or stretch) the category shapes along the reference distance axis according to the environment that surrounds us. Each environment defines a different scale; in this case, a different scale of distance.
To illustrate this adaptation process let’s examine the following adapted qualitative categories figure:
Figure 2- Adapted Qualitative Categories
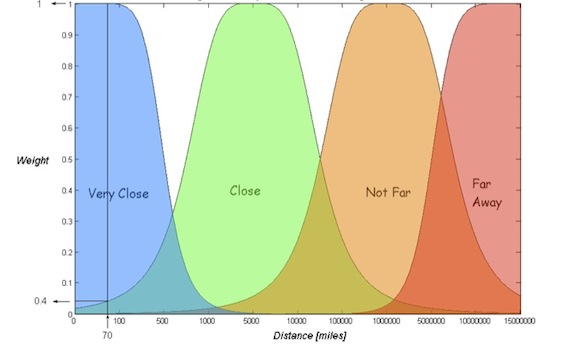
Compared to Figure 1, the x-axis scale was adapted to fit different environments, such as an environment that needs to deal with measuring distance between an asteroid and earth. As shown, the order of the categories along the x-axis and the shapes did not change.
Correlation Rules – Intelligence
After the inputs are mapped into categories, giving each one of them a suitable weight (i.e., level of belonging), expert rules that define the relationships between the weights need to be established. As opposed to differential operators, which are used in order to correlate between the variables in multi-degrees of freedom mathematical equations, these rules are much simpler. For example:
a) if the asteroid DISTANCE is far away AND its velocity is slow then (LEVEL OF ALERT IS LOW) ELSE
b) if the asteroid DISTANCE is not far AND its velocity is slow then (LEVEL OF ALERT IS MEDIUM) ELSE
c) if the asteroid DISTANCE is close AND its velocity is medium then (LEVEL OF ALERT IS HIGH) ELSE
A set of such rules will create correlation that in the end generates a decision followed by an action or inaction. As long as these rules are built logically and more cases (i.e., rules) are adapted and piled up, the decision becomes more robust. As long as these rules are logically consistent, the level of ‘intelligence’ becomes higher.
Closed – Feedback
Closed-feedback operations are necessary for any kind of system which isn’t purely analytical, like the human brain or the alternative I present in this article. The brain constantly examines the actual result of its actions and compares them to the desired results. This operation is responsible for fixing a decision until an acceptable result is achieved.
The Security Expert
Lets us use the previously described process on the operation which the information security expert needs to perform.
In order for the security expert to be able to analyze communication parameters, decide about their level of threat and the appropriate mitigation methods, the following operations are required:
1. Sensors / Network Monitors – These tools enable the security expert to watch and aggregate communication characteristic parameters in real time. With the sensors’ inputs, the security expert can create qualitative categories.
2. Creating Qualitative Categories – The security expert adapts the network environment. He needs to know which:
• Rate parameters per network and application protocols
• Network and application protocol distribution
• Typical latency and server response time
• Network and servers capacities (e.g., CPU , memory)
• Concurrent sessions per time in a day
• Frequency of server error response
The security expert builds qualitative categories in his mind. These categories are not different from the ones described previously. According to his acquired knowledge, he adapts a shape and position to each category, probably in the same way described in the previous section as an adaptation process.
For example, the number of protocol/server error replies can be characterized in the following way:
Figure 3- Server Error Replies Qualitative Categories
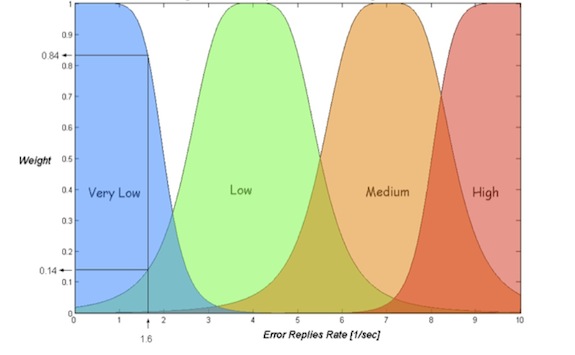
It should be emphasized that one communication parameter which was characterized as high in a certain environment can be characterized as low in another, according to the adaptation process.
3. Correlation (“Intelligence”) – Relying on an assessment of each communication parameter independently of the other type will usually lead to a wrong decision (defined as false positive decision). Therefore, the security expert correlates between all weights (i.e., degrees of belonging to a category) through logical rules he has constructed in his mind. These expert rules are deterministic relationships that will eventually define the level of decision accuracy.
In the case of Error Replies (Figure 3), the security expert might follow the below rules (adding additional parameters), in order to come to a decision:
a) If the error rate is high AND the number of source IP addresses that cause the errors is high then (LEVEL OF THREAT IS MEDIUM) Else,
b) If the error rate is high AND the number of source IP addresses which causes the errors is low then (LEVEL OF THREAT IS HIGH) Else …
If rule b is true, then there is a higher probability that the cause for these protocol error replies is a real attacker (e.g., threat type such as dictionary attack, application scans, etc.).
4. Closed-Feedback Operation – No system is perfect. In order to reduce false positives, the security expert conducts closed-feedback operations. These operations enable him to ‘fix’ inaccurate decisions. When a decision on some kind of attack mitigation action is made, the expert checks the results of this action. If the difference between the desired result and the actual result is acceptable, then the same action needs to be continued. If the difference isn’t acceptable, then the expert would stop using the last action and continue to search for a more appropriate one.
Without adapting a technologies that will enable an appropriate alternative to at least some of the security expert’s operations, the transition into a system that is supposed to automatically mitigate attacks cannot be really made.
Applicable Behavioral Analysis Technologies
Expert Systems Expert systems have proved themselves to be effective in many areas such as guided missiles systems, controllers of high speed trains, aeronautics, and more.
An expert system is software that works with both knowledge and information. It aids in formulating a decision the way an expert in the field will do. In order to do this, expert human rules are formulated in such a way that the system will be able to use them in the decision-making process.
Because expert systems provide a way of drawing definite conclusions from vague and ambiguous or imprecise information, it can overcome analysis difficulties usually raised in network communication. Some of the generic components of an expert system are described below:
Knowledge Base: A store of factual and heuristic knowledge. This knowledge can be expressed through mathematical functions that formulate qualitative category shapes, as described previously.
Decision Engine: Inference mechanisms for manipulating the outputs (i.e., weights) of each category function in order to form a line of reasoning in solving a problem. The inference mechanism can be constructed through chaining of IF-THEN rules such as those described before as Correlation Rules.
Knowledge Acquisition System: This system helps to build knowledge bases. Collecting knowledge is needed in order to adapt the network’s environment. This knowledge is important in order to tune the system’s decision and can be understood as the adaptation process that was described before.
Closed-Feedback Systems: Feedback Control is an error-driven strategy; corrections are made on the basis of a difference between the system’s current state, and the desired state. In the simplest case of linear Feedback Control, the corrections are proportional to the magnitude of the difference, or error. Closed feedback algorithms help to minimize false positive decisions.
Conclusions
Over the last couple of years, the requirements from real-time network and application security systems become more challenging. The most demanding one is to integrate “nontraditional security technologies” that would add more intelligence to the security systems. The main goal is transfer control of some responsibilities that before were in the hands of the human security experts, to expert systems acting in real-time and with minimal mistakes in order not to negatively impact the business transactions.
As long as human intelligence remains an unsolved mystery, we cannot expect a security system to provide us with a complete solution. However, this article characterized the process in which the human security expert comes to conclusions. These characteristics are similar to the ones which exist today in expert systems.
The field of expert systems is a mature discipline and is researched all over the world in both academic institutions and the industry – It will be beneficial to use the expert systems outlined in this article in order to successfully emulate the security expert decision inside the security Box. Some systems already do that but the way to a real ‘security expert in the box’ is still a long way off.














