Banking Trojans offered up via the BlackHole exploit kit created pages dominated the malware scene over the third quarter, according to a new threat report from managed security services firm Solutionary.
A majority of the malware are mass distributed through phishing emails masquerading as coming from trusted brands or from plain spam, Solutionary said in its first quarterly research report, covering the third quarter of 2012, released Thursday. The original plan was to present an analysis of all the analyzed malware samples, but the Security Engineering Research Team at Solutionary decided to narrow the focus on to the BlackHole exploit kit and payload after realizing how BlackHole attacks dominated the quarter, Solutionary said.
Email remained the most common way to deliver banking Trojans, Solutionary said in its report, and malicious pages built using the BlackHole exploit toolkit proliferated during the quarter. Recent Solutionary analysis suggests BlackHole represents 67 percent of all exploit kit attacks, making it the most popular kit among cyber-criminals.
 “The malware types identified in our report impact enterprises, SMBs, government agencies and consumers,” said Rob Kraus, director of SERT.
“The malware types identified in our report impact enterprises, SMBs, government agencies and consumers,” said Rob Kraus, director of SERT.
While several large financial institutions were hit by a wave of distributed denial of service attacks at the end of September, most small-to-midsized financial institutions battled a BlackHole campaign that used DDoS attacks as a diversionary tactic.
Large financial institutions, including Bank of America, Wells Fargo, PNC Bank, and JPMorgan Chase, experienced high traffic volumes and intermittent outages within a few days of each other over a two week period. While these highly disruptive attacks don’t appear to have resulted in financial fraud or theft, the group responsible or the motivations are still unclear.
Solutionary referred to the warnings from the Federal Bureau of Investigation (FBI) and the Internet Crime Complaint Center in September in its analysis of the BlackHole operation against smaller financial organizations. In these attacks, banking personnel were targeted with spam containing malicious links directing victims to BlackHole-enabled Websites. When the users clicked on the link, they were infected with banking Trojans, usually ZeuS or Cridex, according to Solutionary. What made this campaign different from any other fraudulent wire transfer operation was the fact that many of the victims were also hit with DDoS attacks.
The fraudulent wire transfers were preceded, or followed-up by, DDoS attacks to cover up the fraudulent activity being conducted, Solutionary said in its report. In some cases, the attacks were launched with the DirtJumper botnet.
“Cybercriminals constantly evolve malware and attack techniques to evade security and gain the most profit from their targets,” said Kraus.
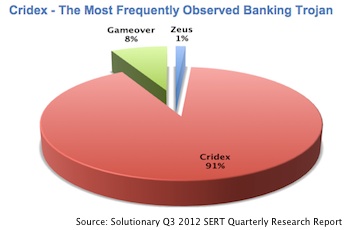
Solutionary found that 92 percent of malware samples analyzed by SERT over the last quarter were mass-distributed malware. Of the malware, the majority were banking Trojans, including ZeuS, Gameover, and Cridex. In fact, the report found that of the sample analyzed over the quarter, 91 percent of the banking Trojans actually belonged to the Cridex family.
Cridex copies itself to the victim’s system and attempts to inject itself into several processes that are running at the time. Like ZeuS, Cridex has a configuration file which lists HTML pages and Websites it can inject code into. Cridex is not just after banking information, as it can harvest user credentials for social media sites and monitor and manipulate cookies. The harvested data is saved to a file and sent back to a command-and-control server.
“Only 54 percent of those samples were detect by common anti-virus software at the time of analysis,” Solutionary said in its report, noting that the variants were relying on obfuscated code to avoid detection.















