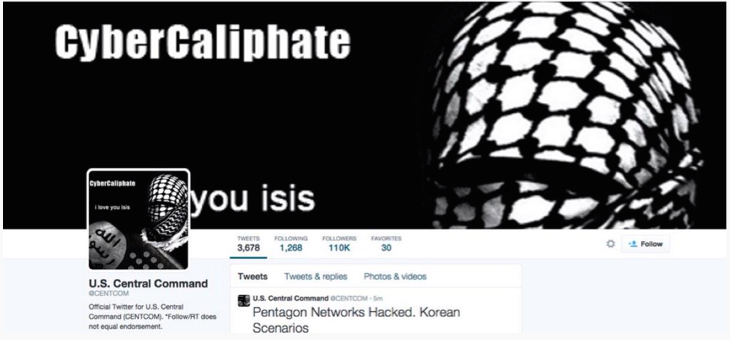
Hackers supporting Islamic State jihadists briefly took control of the Twitter and YouTube accounts of the U.S. Central Command (CENTCOM), the Department of Defense confirmed Monday.
In the attack, hackers replaced the main banner for CENTCOM’s Twitter account with an image of a masked fighter along with the words “CyberCaliphate” and “I love you ISIS”.
The attackers Tweeted and posted a message to Pastebin saying, “You’ll see no mercy infidels. ISIS is already here, we are in your PCs, in each military base. With Allah’s permission we are in CENTCOM now. We won’t stop! We know everything about you, your wives and children. U.S. soldiers! We’re watching you!”
The attackers also posted information and details on Military personnel and photos, including a phone directory of officers, which some say it out-of-date and already publically available.
“We can confirm that the US Central Command Twitter and YouTube accounts were compromised earlier today. We are taking appropriate measures to address the matter,” a Deparment of Defense representative said in a statement.
“CENTCOM’s operational military networks were not compromised and there was no operational impact to U.S. Central Command,” a CENTCOM news statement issued later in the day said.
“We are viewing this purely as a case of cybervandalism,” the statement continued. “In the meantime, our initial assessment is that no classified information was posted and that none of the information posted came from CENTCOM’s server or social media sites. Additionally, we are notifying appropriate DoD and law enforcement authorities about the potential release of personally identifiable information and will take appropriate steps to ensure any individuals potentially affected are notified as quickly as possible.”
Related: ISIS Cyber Ops: Empty Threat or Reality?
The @CENTCOM Twitter account was suspended at the time of publishing, but the Department of Defense has regained control of the compromised accounts.
“The account compromised was timed with the release of a couple of sensitive documents on Pastebin, which appears to have been designed to intimidate US soldiers,” Trey Ford, Global Security Strategist at Rapid7, told SecurityWeek. “One thing to note: the Sony document dumps were laced with malware, and I expect these files may also be part of a targeted malware campaign targeting military analysts and their families.”
“This attack looks to be the same actors as the WBOC and Albuquerque Journal attacks last week,” Ian Amit, Vice President at ZeroFOX, said. “The verbiage is the same, the behavior is the same, the hashtags are the same — all indicators suggest this is the same group. The full extent of the damage: 3 Twitter accounts and 1 YouTube account.”
“Much of this appears to be simply scare tactics,” Amit added. “All of the “leaked” documents are in fact public domain, repackaged to look like a real data breach. These actors are trying to make themselves look more legitimate by threatening soldiers wives and claiming to have mobile access. In truth, they likely only stole a password, either through a phishing scam or a brute-force attack.”
On Sunday, European, US and Canadian security ministers said that increased Internet surveillance and tighter border checks were “urgently” needed to combat jihadist attacks of the sort that shocked Paris last week.
U.S CENTCOM promotes cooperation among nations, responds to crises, and deters or defeats state and non-state aggression.
One of nine unified commands in the U.S. military, CENTCOM’s has an area of responsibility in the central area of the world consisting of 20 countries, including Afghanistan, Iran, Iraq, Jordan, Kazakhstan, Kuwait, Kyrgyzstan, Lebanon, Oman, Pakistan, Qatar, SaudiArabia, Syria, Tajikistan, Turkmenistan, United Arab Emirates, Uzbekistan, and Yemen.
The attacks against CENTCOM came just as President Obama give an address and announced a series of initiatives designed to enhance the nation’s cybersecurity and privacy environment.














