If you’re an administrator or security team member for your organization’s network, you’ve likely heard about the Crisis malware at some point in your risk management research. On Friday, Symantec published a new white paper on the malware, with a rounded overview into its history and details of its capabilities.
Crisis was discovered in July, by accident, in the massive sample repositories provided to the AV industry by Virus Total. Mac-based AV firm Intego broke the story, and gave it a good deal of attention, because the malware itself is capable of infecting systems running Mac OS X and Windows.
At the time, we here at SecurityWeek felt the threat was over-hyped. We are still taking that stance, because the overall threat Crisis represents is mitigated by the various protection layers commonly deployed within a given network – including IDS, IPS, endpoint protections, and proactive gateway defenses.
Yet, we’ll freely admit Crisis is something worth watching. While some vendors overhyped the crisis that is – ahem – crisis; there’s no denying that it was evolved. The ability to create a backdoor into a system isn’t just an OS X attack vector; Crisis can do that on Windows systems too. Moreover, it can attack virtual machines, and once it’s installed on any of the three it can then move on to other functions.
Crisis can be used to capture Wi-Fi data in order to triangulate position, it can upload and download files on a compromised host, it can record video and audio, log keystrokes, copy clipboard data, snatch address book details, log IM data, monitor browser sessions, capture social networking data, and take screenshots. In short, Crisis packs a punch, provided it isn’t detected during the initial payload delivery.
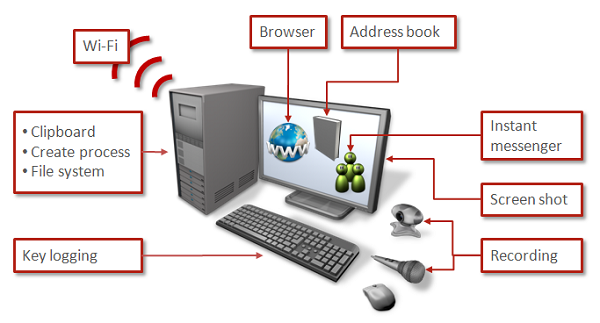
“The features found in this malware suggest that it may have been designed for the purpose of either private investigation or espionage, and are much more advanced than those found in the average information stealing malware,” Takashi Katsuki, a Software Engineer from Symantec explained in the white paper.
Yet, there is no proof that Crisis is a law enforcement tool, only speculation. Still, Symantec believes that the malware will only continue to evolve.
“In our research into Crisis, we have seen older samples of the malware that did not have virtual machine propagation techniques or the presence of the social function,” the white paper noted. “By observing variants and the timeline of creation, we can surmise that there is continued investment and development of the Crisis malware. The demand for private IT investigations and espionage will never disappear and, so long as there is customer demand, it is likely that we will see new functionality emerging in this area in the near future.”
“The features found in this malware suggest that it may have been designed for the purpose of either private investigation or espionage, and are much more advanced than those found in the average information stealing malware,” the report concludes.
















