New App Helps Detect Secretly Jailbroken, Compromised iOS Devices
Owners of iPhone and iPads can stay better informed on the security of their devices courtesy of “System and Security Info,” a new application designed to provide users with detailed information on what applications and processes are running on their iOS devices.
Developed by Germany-based SektionEins GmbH, the tool was built with jailbreak and anomaly detection functionality, so that security concerned users can check for potential privacy issues and security threats.
Designed with support for devices running iOS 8.1 or later, the utility is compatible with iPhones, iPads, and iPod touch devices and can display info such as CPU, memory and disk usage, and process list. Additionally, the software allows users to inspect running apps (SHA1 Hash, Signature, Entitlements), and to take advantage of capabilities such as jailbreak, security anomaly, and malware detection.
 According to SektionEins, a company that has shown interest in iOS kernel and jailbreaking, System and Security Info can provide users with info on whether an attacker is using a public jailbreak or a customized version to hack and backdoor their devices. The tool does so by running tests meant to find artifacts pertaining to one of the known jailbreaks.
According to SektionEins, a company that has shown interest in iOS kernel and jailbreaking, System and Security Info can provide users with info on whether an attacker is using a public jailbreak or a customized version to hack and backdoor their devices. The tool does so by running tests meant to find artifacts pertaining to one of the known jailbreaks.
Jailbroken devices are exposed to a wide range of threats, since most malicious applications were designed to target these unlocked devices. However, malware and rogue app stores that target non-jailbroken devices exist as well, such as vShare, a rogue app store that provides access to over 1 million apps that haven’t been scrutinized by Apple’s app vetting process.
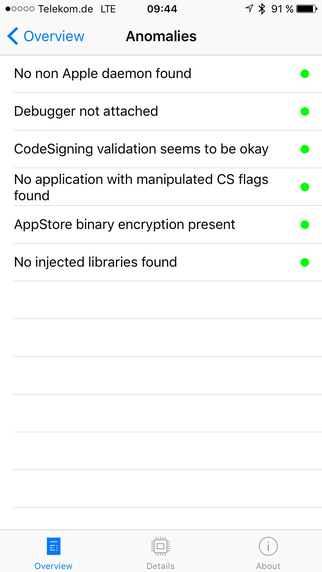
As for the anomaly detection capabilities of the application, the company explains that they are based on testing whether certain security assumptions are still valid. The tool checks the code signing flags of running processes for signs of tampering, and verifies that an app is still encrypted and not running in a debugger.
The security checking utility also verifies that code signing is still capable of detecting malicious apps, meaning that no unsigned binaries are running, and that no unexpected libraries are injected into the process, since this is sign of tweak runtime functionality. Some anomalies might be related to the accessibility features of iOS, which do inject unexpected libraries into the tool’s own process.
The new utility is meant to provide users with a cheap solution to stay better informed on the security and privacy stance of their devices. System and Security Info is now available for download from the App Store as version 1.0.2.
“Of course such tests in a publicly released tool can never fully replace a detailed analysis in our lab, because attackers can adapt and specifically detect and subvert our tool,” SektionEins’ Stefan Esser explained. “They provide however a good first round of checks in the process to determine if the security of your iOS device has been compromised. Furthermore it has been reported that several vendors selling iOS spyware fully rely on modified public jailbreaks for their tools. The chance of detecting one of those is therefore high.”
With the number of Mac OS X and iOS security threats growing fast, as Symantec revealed in a December report, users should be more concerned about the security of their devices. iOS 9 exploits and jailbreaks are included here, albeit they are rare enough to determine exploit acquisition company Zerodium to offer up to $1 million for such bugs.
Currently priced at $0.99, the System and Security Info app made it to the #4 position on the Top Charts for Paid apps in Apple’s App Store at the time of publishing.
*Correction – Incorrectly named Zimperium instead of Zerodium which should have been the company named offering iOS bug bounties.












